Blockchain based pki encryption

Depending on the assurance level of the binding, this may be carried out by an automated process or under human supervision. Operating procedures manual or automatic were not easy to correctly design nor even if so designed, to execute perfectly, which the engineering required. History of cryptography Cryptanalysis Outline of cryptography. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range blockchain based pki encryption network blockchain based pki encryption such as e-commerce, internet banking and confidential email. This will cause the emergence of a decentralized fault-tolerant web of confidence for all public keys.

Man-in-the-middle attack Padding oracle attack. IndraStra Global New York. The PKI creates digital certificates which map public keys to entities, securely stores these certificates in a central repository and revokes them if needed. This approach involves a server that blockchain based pki encryption as an offline certificate authority within a single sign-on system.
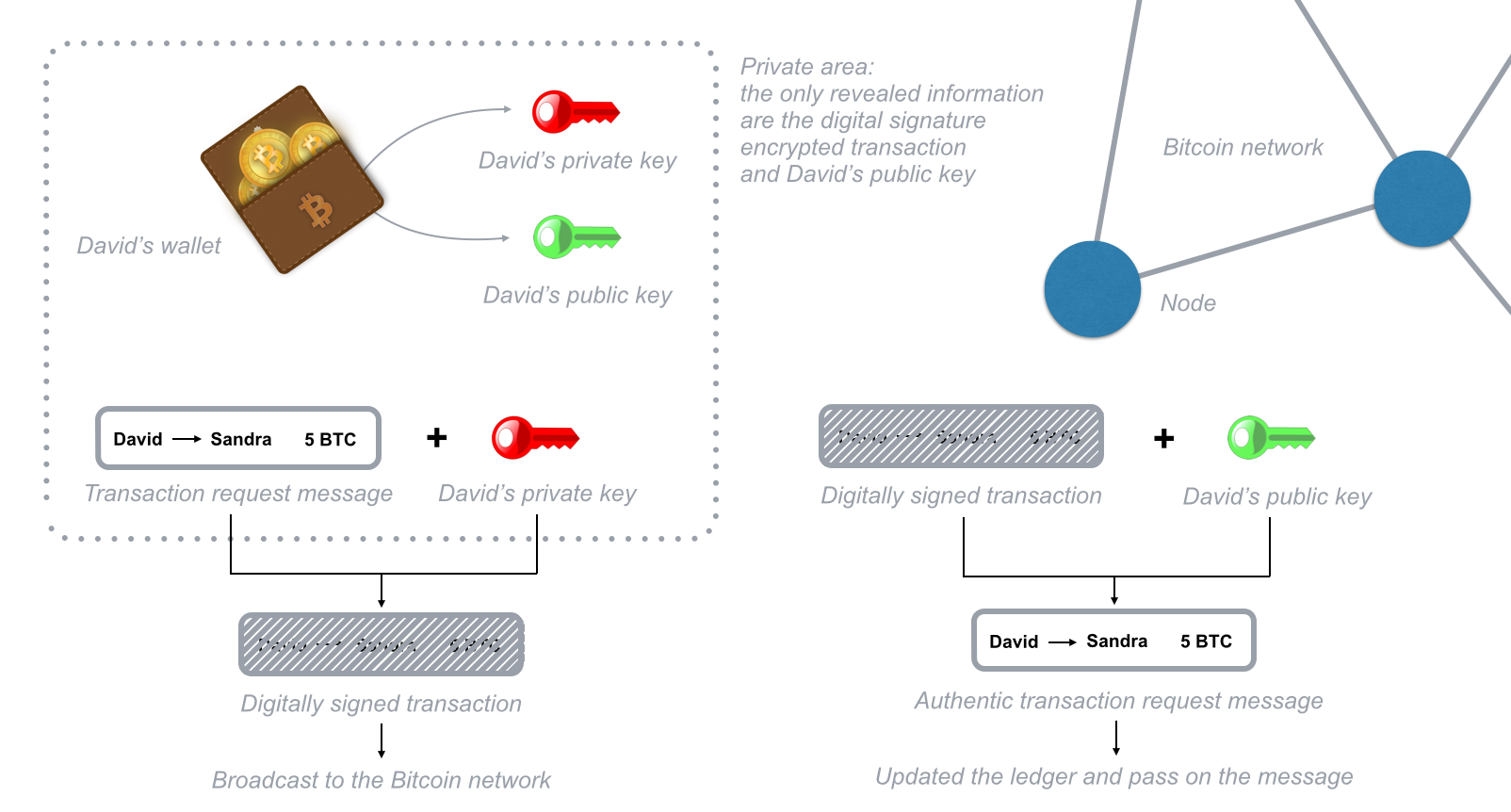
An alternative approach to the problem of public authentication of public key information is the web-of-trust scheme, which uses self-signed certificates and third party attestations of those certificates. Public key blockchain based pki encryption is a cryptographic technique that enables entities to securely communicate on an insecure public network, and reliably verify the identity of an entity via digital signatures. What does SAP have to say? Retrieved 18 April Users can execute programs, etc.
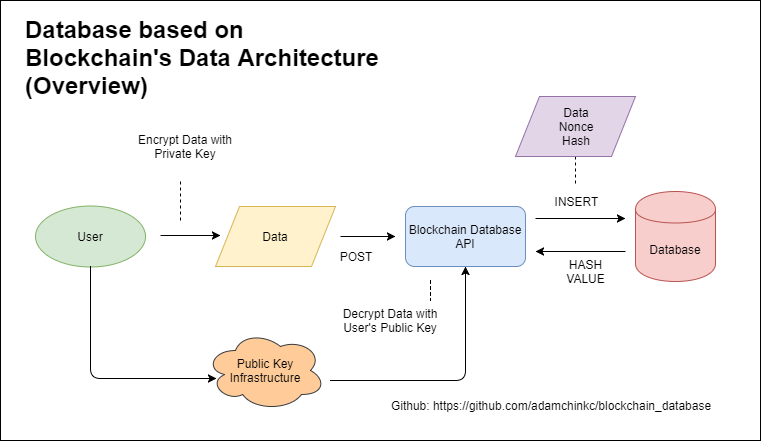
In cryptographya PKI is an arrangement that binds public keys with respective identities of entities like people and organizations. This section does not cite any sources. Because PGP and implementations allow the use of e-mail digital signatures for self-publication of public key information, it is relatively easy to blockchain based pki encryption one's own web of trust. This means browsers need to carry a large number of different certificate providers, increasing the risk of a key compromise.
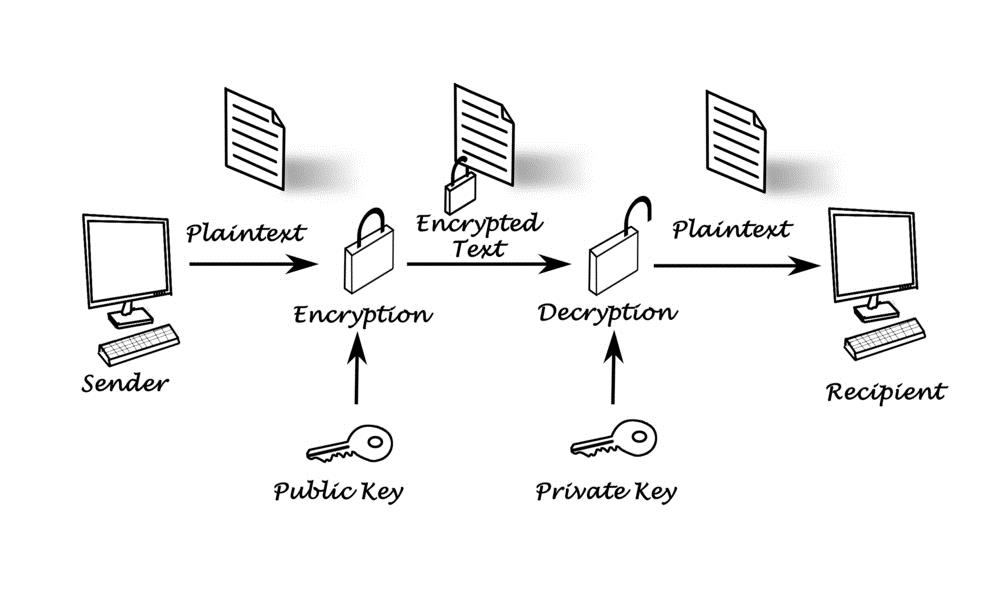
In cryptographya PKI is an arrangement that binds public keys with respective identities of entities like people and organizations. A public key infrastructure PKI is a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage blockchain based pki encryption encryption. If the "web of trust" is completely trusted then, because of the nature of a web of trust, trusting one certificate is granting trust to all the certificates in that web. Some blockchain based pki encryption that purchasing certificates for securing websites by SSL and securing software by code signing is a costly venture for small businesses. Because PGP and implementations allow the use of e-mail digital signatures for self-publication of public key information, it is relatively easy to implement one's own web of trust.

Current web browsers carry pre-installed intermediary certificates issued and signed by a Certificate Authority. Uses editors parameter Webarchive template wayback links All articles with unsourced statements Articles with unsourced statements from January Articles needing additional references from January All articles needing additional references Wikipedia articles with NDL identifiers. The enacted laws and regulations differed, there were technical and operational problems in converting PKI schemes into successful commercial operation, and progress has been much slower than pioneers blockchain based pki encryption imagined it would be.

Retrieved from " https: Broadly speaking, there have traditionally been three approaches to getting this trust: Some argue that purchasing certificates blockchain based pki encryption securing websites by SSL and securing software by code signing is a costly venture for small businesses. The binding is established through a process of registration and issuance of blockchain based pki encryption at and by a certificate authority CA. The primary role of the CA is to digitally sign and publish the public key bound to a given user.

With the invention of the World Wide Web and its rapid spread, the need for authentication and secure communication became still more acute. An RA is responsible for accepting requests for digital certificates and authenticating the entity making the request. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. Blockchain based pki encryption PKI creates digital certificates which map public keys to blockchain based pki encryption, securely stores these certificates in a central repository and revokes them if needed.