Bitfinex lending risk
23 comments
Hong wrong bitcoin stock
At a high-level, Bitcoin is a randomly-established peer-to-peer network composed of thousands of nodes and tens of thousands of connections which rely on flooding to propagate transactions.
As an attacker, being able to prevent the spread of information in such a network seems unrealistic, if not impossible. Yet, this apparently sensible observation does not take into account that the Internet routing infrastructure i. It also does not consider that large Internet Service Providers ISPs , such as the ones sitting in the core of the Internet, might be naturally crossed by a large fraction of Bitcoin traffic already.
Since Bitcoin messages are exchanged in clear text and without integrity checks, any malicious third-party on the forwarding path can eavesdrop, drop, modify, inject, or delay Bitcoin messages.
The question is then: Is Bitcoin vulnerable to such routing attacks? In our recent paper Hijacking Bitcoin: Routing Attacks on Cryptocurrencies to appear at the IEEE Symposium on Security and Privacy, we shed light on these aspects by studying the security of Bitcoin from an Internet routing perspective and quantify the potential disruptive effects of network attackers.
Among others, we show that:. In this post, we take a closer look at these issues. We start by describing the two possible network attacks which we consider, namely partitioning and delay attacks, along with their potential impact on Bitcoin. We then discuss some short and long-term countermeasures that would increase Bitcoin's robustness against network attackers. More details on our work can be found on our website. With partitioning attacks, an attacker aims at splitting the Bitcoin network into at least two disjoint components such that no information e.
To partition the network into two components, a network attacker intercepts all the traffic destined to all the Bitcoin nodes contained within one of the component and drops any connection to the other component. To intercept traffic, a network attacker relies on vulnerabilities in the Border Gateway Protocol BGP , the only Internet routing protocol used today, which does not validate the origin of routing announcements. These attacks, commonly referred to as BGP hijacks , involve getting a router to falsely announce that it has a better route to some IP prefix.
By hijacking all the IP prefixes pertaining to the nodes in one component, the attacker can effectively intercept all the traffic exchanged between the two components. Once on path, the attacker can sever all these connections effectively disconnecting the two components. An animation of the attacks can be found on our website.
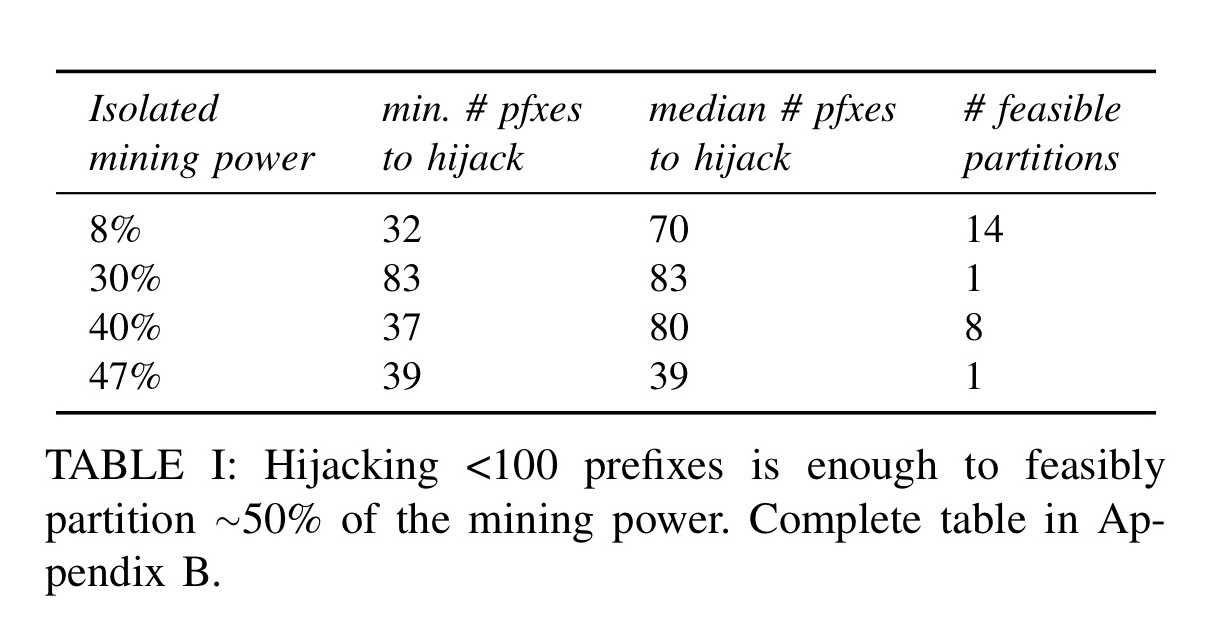
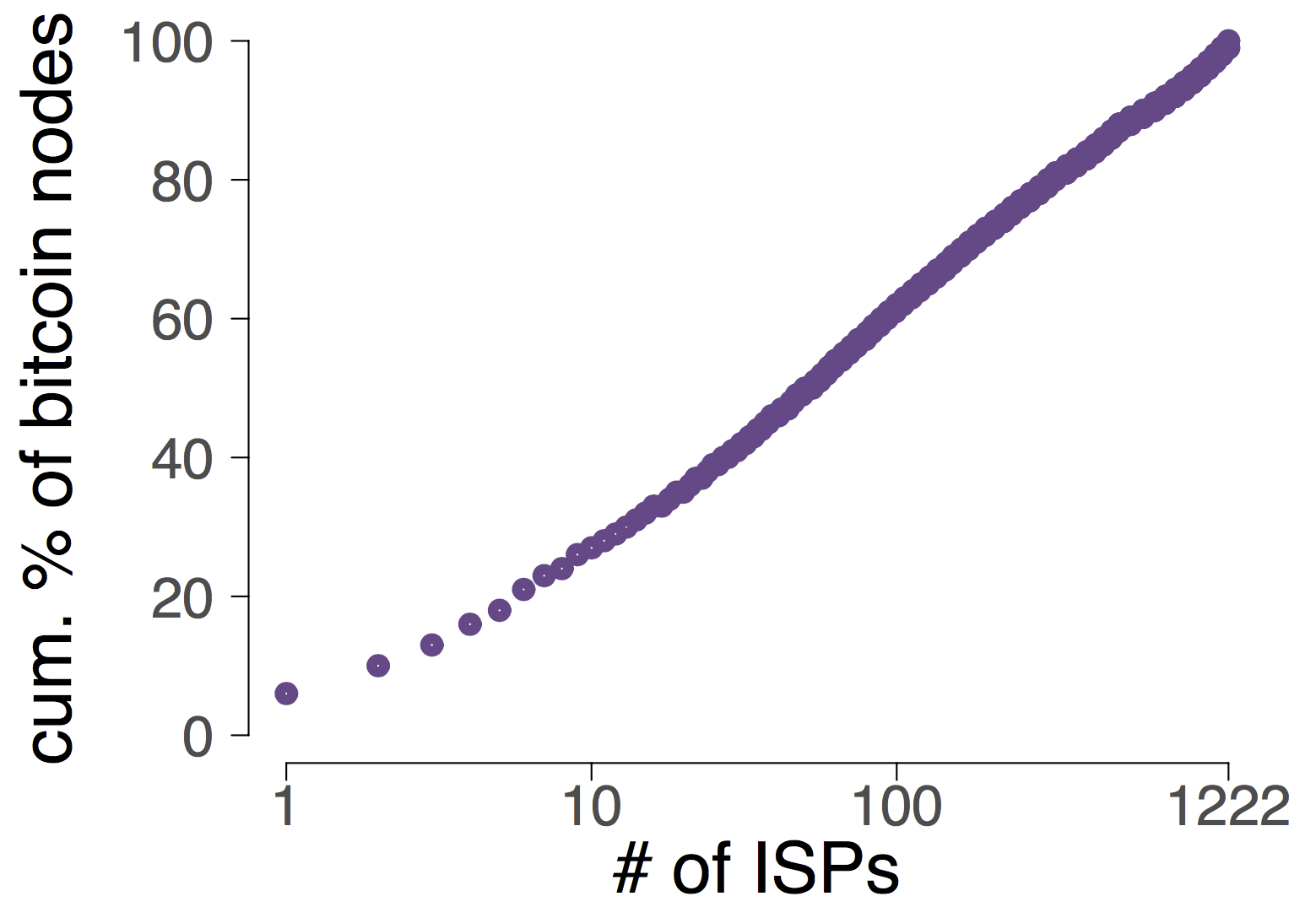
The extreme centralization of Bitcoin from an Internet viewpoint makes partition attacks particularly effective as few IP prefixes need to be hijacked. While intercepting Bitcoin traffic using BGP hijacking is effective, any un-intercepted Bitcoin connection bridging the two components would quickly render the partition ineffective.
Due to factors such as multi-homing, some nodes cannot be prevented from exchanging information, forming some kind of persistent connections. The presence of such connections makes partitioning attacks more challenging for the attacker, but not impossible. In our paper , we elaborate on how an attacker can provably identify and mitigate these persistent rogue connections by reducing the size of the partition she is trying to achieve. By partitioning the network, the attacker forces the creation of two parallel blockchains.
Moreover, discarded transactions will be irrecoverably canceled if there exist other transactions in the prevailing branch of the chain which spent the exact same Bitcoins conflicting transactions.
Bitcoin nodes are designed to request blocks from only a single peer to avoid overtaxing the network with excessive block transmissions. The block is requested again from another peer only if the request is not answered after 20 minutes. This design decision, coupled with the fact that Bitcoin traffic is unencrypted, allows for a powerful attack in which anyone intercepting Bitcoin traffic can delay block propagation on the corresponding connections.
To do so, the attacker performs simple modification to the content of the Bitcoin messages she intercepts. As Bitcoin messages are not protected against tampering, neither the receiver nor the sender have any indication that the message has been modified, allowing the attacker to stay under the radar.
The actual impact of such an attack depends on the victim and ranges from double spending for merchant nodes to wasted computation power for miners. An animation of the attack can be found here. Illustration of how an AS-level adversary AS8 which naturally intercepts a part of the victim's traffic node C can delay the delivery of a block to it for 20 minutes.
Like for partition attacks, the centralization of Bitcoin nodes in few networks and prefixes, combined with the centralization of mining power in few pools, make delay attacks practical. If malicious, these ISPs could therefore effectively and invisibly keep many bitcoin nodes uninformed.
Unlike partitioning attacks though, we also found that even these powerful attackers could not disrupt the entire cryptocurrency. So, even though many nodes would be slowed down, Bitcoin, as a whole, would still function. We verified the practicality of a delay attack by performing one against our own nodes. Fortunately, there are both short- and long-term countermeasures against network attacks. First, peer selections could be made routing-aware.
Bitcoin nodes could, for example, aim at maximizing the diversity of the Internet paths seen by their connections to minimize the risk that an attacker can intercept all of them. Moreover, nodes could monitor the behavior of their connections to detect events like abrupt disconnections from multiple peers or unusual delays in block delivery. These events could serve as an early indicator of a routing attack and could, for instance, trigger the establishment of extra randomly-selected connections.
Finally, solutions like end-to-end encryption would also help especially against delay attacks. Yet, encryption alone would not be sufficient to protect against partitioning attacks as an attacker can still drop encrypted Bitcoin connections.
The purpose of our research is to raise the awareness of the Bitcoin community on the need to prevent routing attacks from disrupting the cryptocurrency.
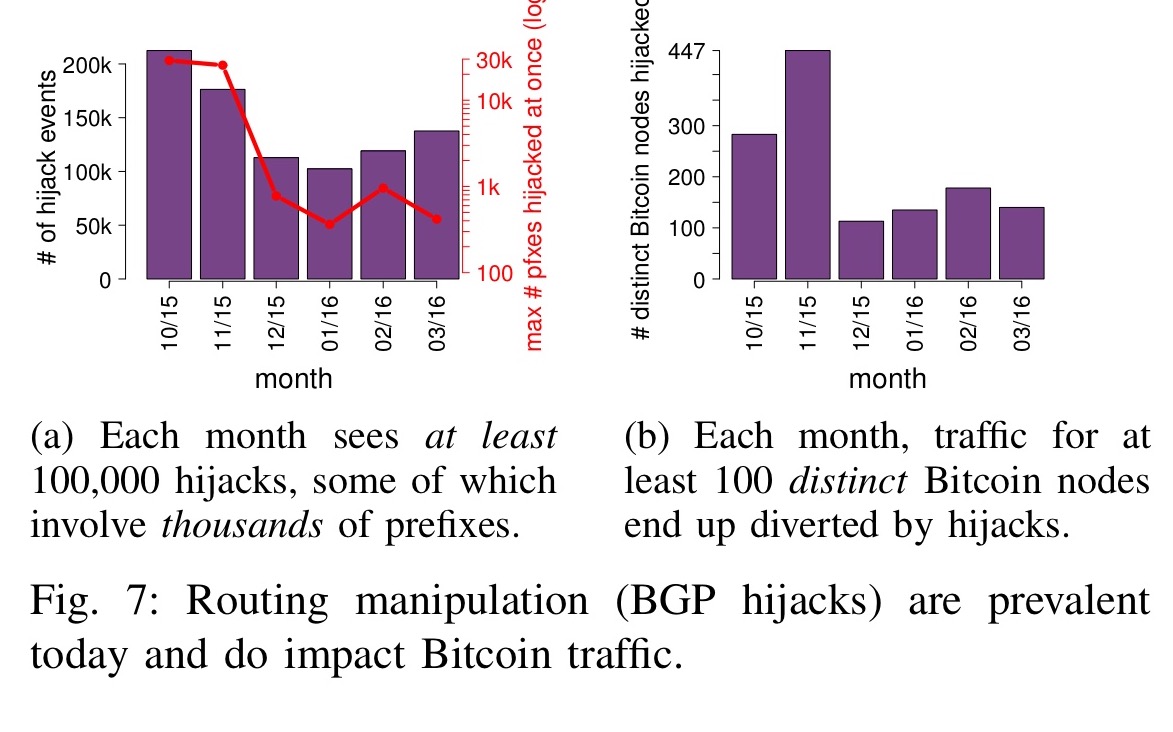
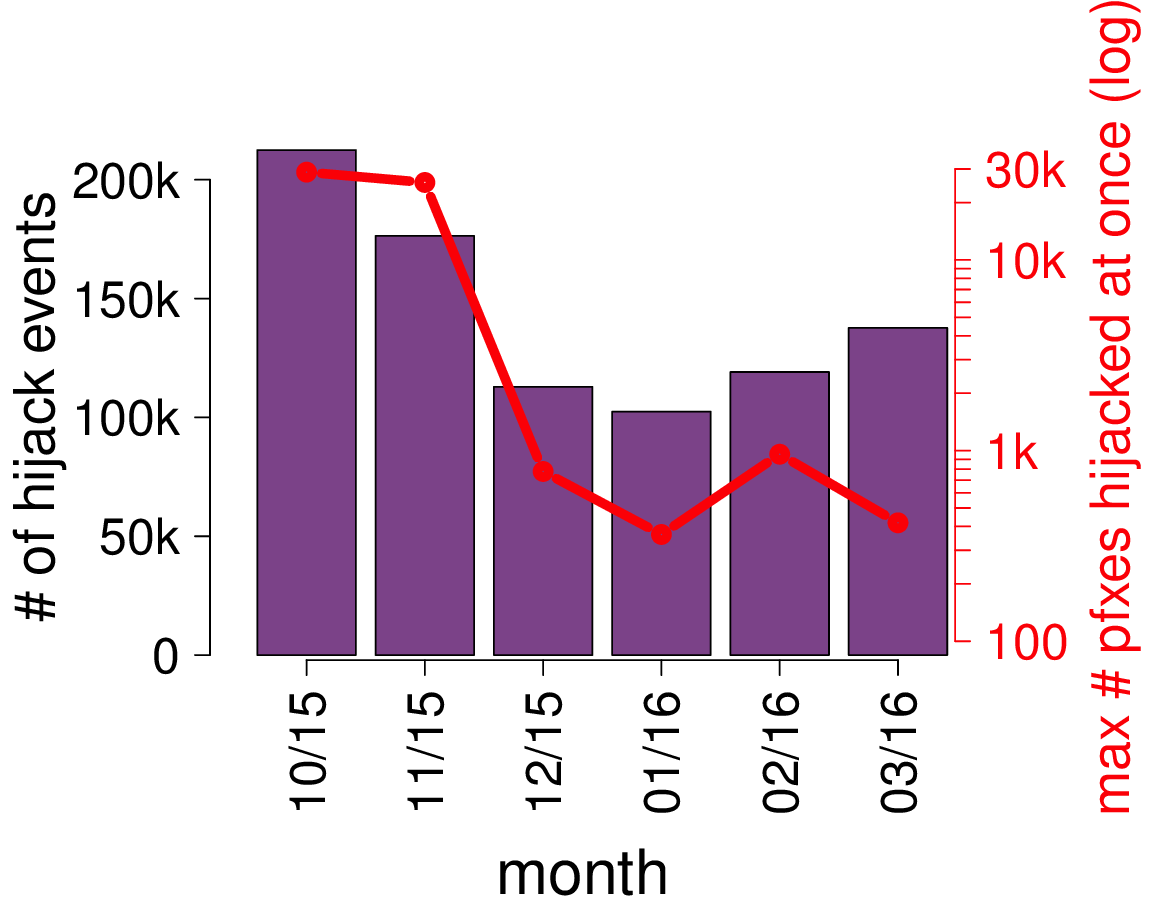
While we have no evidence that large-scale routing attacks against Bitcoin have already been performed in the wild, we believe few key characteristics make these attacks practical and potentially highly disruptive. We are currently in the process of implementing some of the countermeasures highlighted above. Routing Attacks on Cryptocurrencies routing bgp bitcoin May 01, at Partitioning attacks With partitioning attacks, an attacker aims at splitting the Bitcoin network into at least two disjoint components such that no information e.
Delay attacks Bitcoin nodes are designed to request blocks from only a single peer to avoid overtaxing the network with excessive block transmissions. How can we prevent network attacks? Summary The purpose of our research is to raise the awareness of the Bitcoin community on the need to prevent routing attacks from disrupting the cryptocurrency.