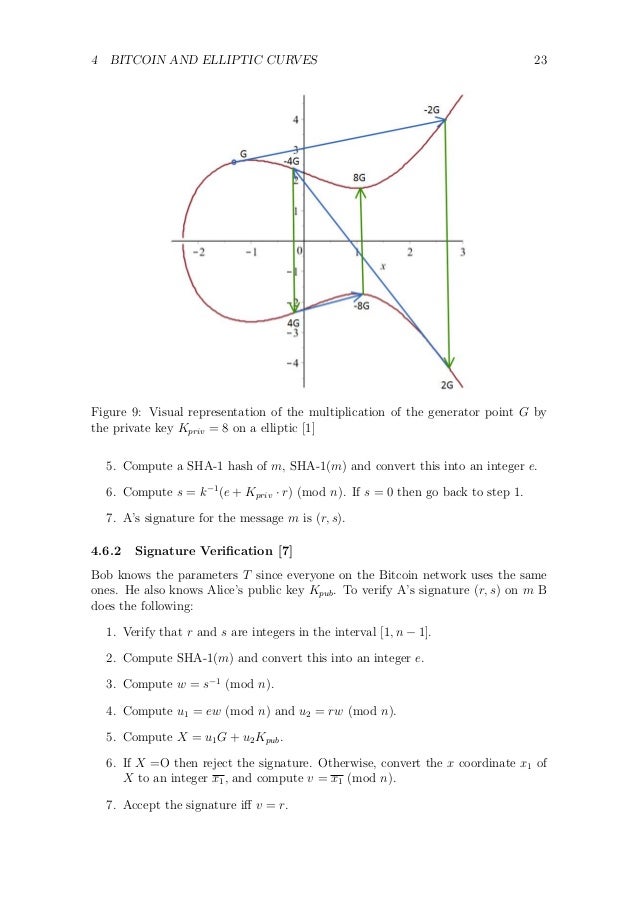
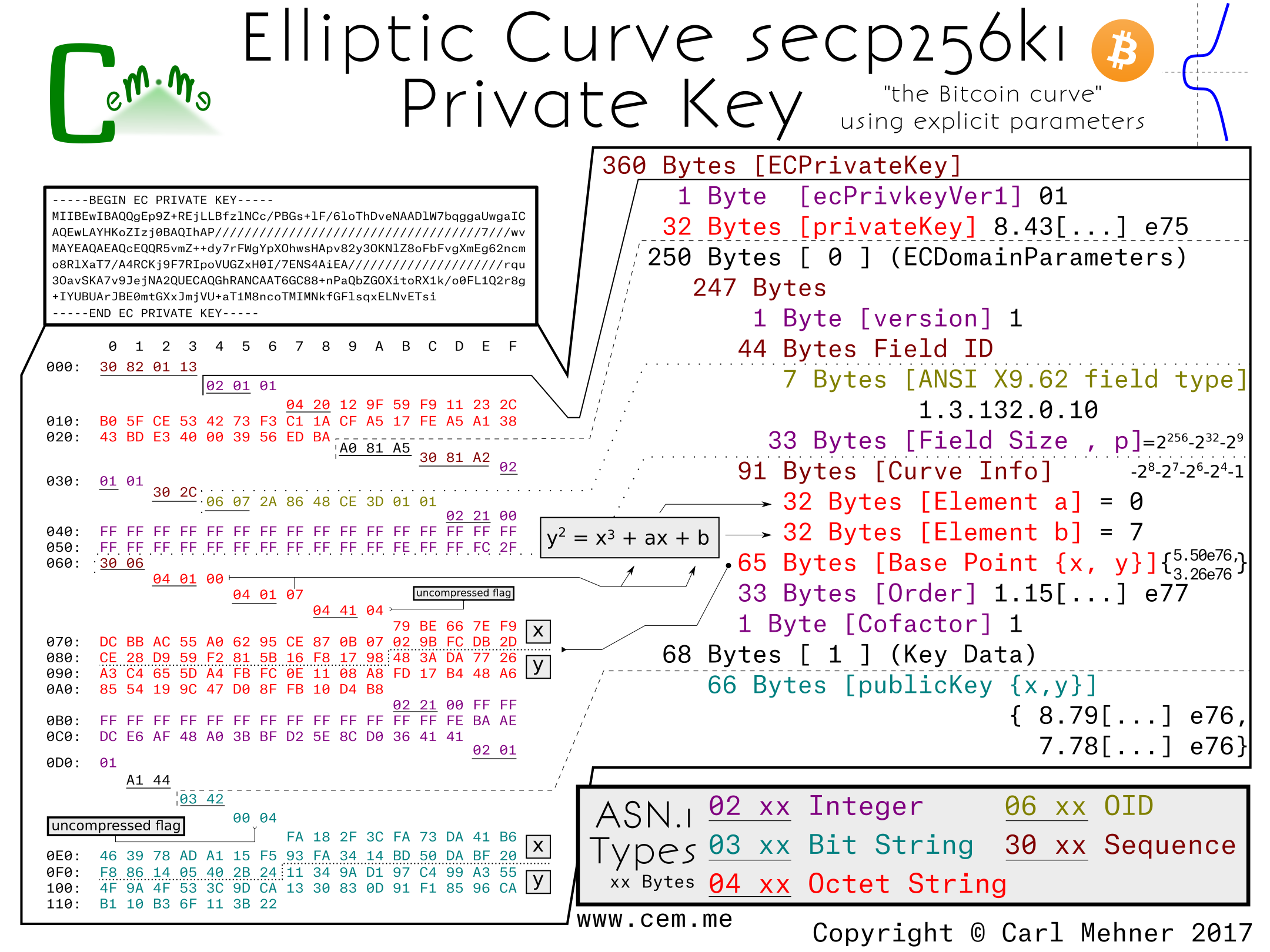
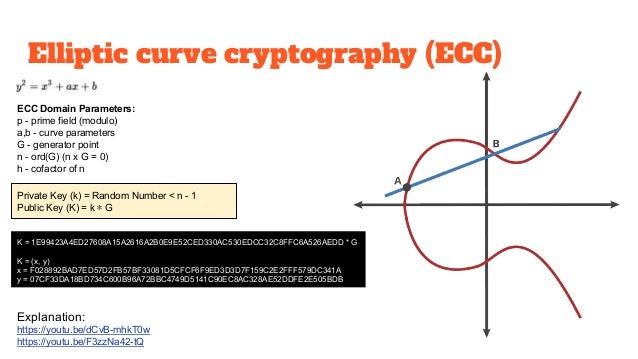
Elliptic Curve Key Generation
5 stars based on
64 reviews
Many cryptographic standards widely used in commercial applications were developed by the U. Unless the government has access to some highly advanced math not known to academia, these ciphers should be secure. This is how it works: What Shumow and Ferguson showed is that these numbers have a relationship with a second, secret set of numbers that can act as a kind of skeleton key.
If you know the secret numbers, you can predict the output of the random-number generator after collecting just 32 bytes of its output. This is important because random number generators are widely used in cryptographic protocols. If the random number generator is compromised, so are the ciphers that use it. All of this has been known for several months. ECDSA keys are derived from elliptic curves that themselves are generated using certain parameters. Secpr1 is supposed to use a random number in generating the curves.
The seed need not be random since the output of the hash function is not predictable. Now as Vitalik pointed out, even if the NSA knew of a specific elliptic curve with vulnerabilities, it still should have been near impossible for them rig the system due to the fact that brute-forcing a hash function is not feasible.
However, if they discovered a flaw that occurred in say, one curve in every billion, then they only need to test one billion numbers to find the exploit. However, the kicker in all this is that the parameters for secpr1 were developed by the bitcoin elliptic curve parameters of elliptic curve research at the NSA!
Now the decision to use secpk1 instead of secpr1 was made by Satoshi. I did not know that BitCoin is using secpk1. Indeed, I am surprised to see bitcoin elliptic curve parameters use secpk1 instead of secpr1.
This was either random luck or pure genius on the part of Satoshi. Either way, Bitcoin dodged a huge bullet and now almost seems destined to go on to great things. I have written a piece a while ago speculating about these same issues.
Thanks for the Article! Even with something open source, this makes it nearly impossible to notice the weakness in the code — you have to know about the specific problem with the standard itself.
My big concern is with client side scripting for wallet generation. You point out that the Bitcoin devs dodged a bullet with choosing a less well established algorithm standard. But so many wallet generators are available now — including bitaddress. How do I — the neophyte bitcoin user, and non-mathematician — verify that these resources are using the same standard as Bitcoin bitcoin elliptic curve parameters and not some weaker method that might give a hacker a window to bitcoin elliptic curve parameters Is there a forum or body that vets these resources?
I really like the advantages of a client side generator I can run in a browser offline — but which ones are verified as true to the Bitcoin methods you talk about in this article? I could be wrong but I was under the impression bitaddress. I kind of rely on the fact that the JS dependencies that are used are open source. So far nobody has documented any vulnerabilities.
NIST recommended fifteen elliptic curves. Bitcoin elliptic curve parameters is hard to believe that ten of them are bitcoin elliptic curve parameters cripples, while the five Koblitz curves are rock solid. If secpr1 is flawed, as you convincingly claim, then secpk1 is likely to be flawed too, since it was chosen by the same trickster. It might not have one, but there is suspicion. Bitcoin has too many disadvantages to be a tool of the intelligence community. It is so insecure that it is easily stolen.
Bitcoin enables fraud and other criminal activities. Not any more so than other currencies. The dollar is still the preferred medium for criminals.
Could Bitcoin be used to launder money from non-drug real crimes? Silk Road was taken down with investigative work not by breaking bitcoin. Digital QR codes make it vulnerable to theft. The Bitcoin elliptic curve parameters that are usually used represent public keys. Nobody can steal your Bitcoins from that QR. The anchor revealed his private key on TV. Mining Bitcoins is a health hazard and energy sink. As far as I know only one person got heat stroke from it back in and it was a bit of a freak accident.
There bitcoin elliptic curve parameters no central bank for Bitcoin. Contrary to the assertion, there is far from a consensus in macroeconomics.
Many economists believe central banks are destabilizing rather than stabalizing. The history of the Fed with the two worst economic disasters in world history under its belt and a number of recessions in between has not engendered confidence that they actually have a correct macro understanding.
If asset bubble and the resulting depressions are causes by ultra low interest rates, then bitcoin will certainly improve economic performance. Minting copycat currencies is easy. Bitcoin elliptic curve parameters is a good thing. It results in innovation and improvement. In the end, however, the market will o my select one for use as the general medium of exchange. Can you name an instance where a hacker was able to hack 1 million completely different targets, with different security systems?
Because some things are infeasible. You said that Bitcoin was insecure but you were only half-right. Did you really link to your own blog as a source of proof? Smart Contracts Great Wall of Numbers. If you think that secpk1 associated with NSA spy Koblitz is not also bitcoin elliptic curve parameters, I have a lake to sell you in the middle of the Pacific Bitcoin elliptic curve parameters.
You are bitcoin elliptic curve parameters using your WordPress. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email. Chris Pacia November 7, at 8: Thanks again — I really appreciate this blog! Chris Pacia December 13, at 1: Tito January 4, at 2: Chris Pacia January 4, at 2: Anthony Alfidi January 14, at 1: Chris Pacia January 14, at 6: Overall I invite you to take a deeper look at bitcoin.
You would be wise to learn how the technology works before you criticize it. Anna Mostowy October 23, at 6: Louis Verdolino October 23, at 6: Ellis November 23, at 9: Satoshi Nakamoto aka Central Intelligence. Leave a Reply Cancel reply Enter your comment here Fill in your details below or click an icon to log in: Email required Address never made public.
Post was not sent - check your email addresses! Sorry, your blog cannot share posts by email.