Otc demand for bitcoin and altcoins is rising
20 comments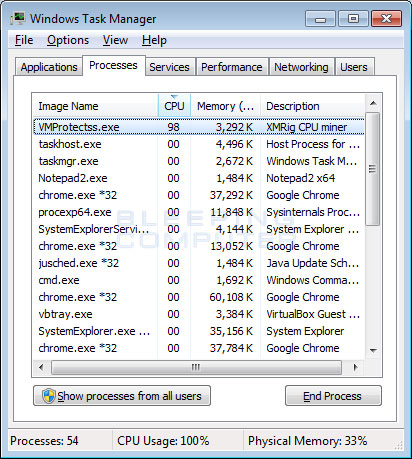
Bitcoin uk exchange reddit
Download Now WinThruster - Win BitCoinMiner-BX is a trojan that comes hidden in malicious programs. Once you install the source carrier program, this trojan attempts to gain "root" access administrator level access to your computer without your knowledge.
BitCoinMiner-BX are difficult to detect because they hide themselves by integrating into the operating system. Once it infects your computer, Win BitCoinMiner-BX executes each time your computer boots and attempts to download and install other malicious files.
Upon successful execution, it deletes the source program, making it more difficult to detect. Trojans are one of the most dangerous and widely circulated strains of malware. A trojan disguises itself as a useful computer program and induces you to install it.
By the time that you discover that the program is a rogue trojan and attempt to get rid of it, a lot of damage has already been done to your system. The intent of a trojan is to disrupt the normal functionality of a computer, gradually stopping it from working altogether. Trojans can make genuine software programs behave erratically and slow down the operating system.
Trojans can delete files, monitor your computer activities, or steal your confidential information. They can enable attackers to have full access to your computer… as if they are physically sitting in front of it. Like other trojans, Win BitCoinMiner-BX gains entry through source programs carrying a trojan payload that you unknowingly install. Common sources of such programs are:. BitCoinMiner-BX is difficult to detect and remove manually.
However, most anti-malware programs are able to detect and remove it successfully. Scanning your computer with one such anti-malware will remove Win BitCoinMiner-BX and any files infected by it. Unfortunately, scanning and removing the threat alone will not fix the modifications Win You will need to clean Windows Registry by removing invalid registry entries using a registry cleaner program. If your computer is infected with Win BitCoinMiner-BX, perform the following steps to remove it:.
We recommend using ClamWin free download , a highly effective and widely used malware removal program to clean your computer of Win In addition to Win BitCoinMiner-BX, this program can detect and remove the latest variants of other malware.
ClamWin has an intuitive user interface that is easy to use. To get rid of Win BitCoinMiner-BX, the first step is to install it, scan your computer, and remove the threat. Double-click the downloaded installer file to start the installation process. The welcome screen is displayed. On the License Agreement screen that appears, select the I accept the agreement radio button, and then click the Next button. On the Select Installation Options screen that appears, click the Next button.
On the Select Destination Location screen that appears, click the Next button. On the Select components screen that appears, click the Next button. On the Select Additional Tasks screen that appears, click the Next button.
On the Ready to Install screen that appears, click the Install button. Click the Yes button. Once the update completes, select one or more drive to scan. You can hold the Shift key to select multiple drives to scan. Click the Scan button. By now, your computer should be completely free of Win Although it has been removed from your computer, it is equally important that you clean your Windows Registry of any malicious entries created by Win An infection from Win It can maliciously create new registry entries and modify existing ones.
Therefore, even after you remove Win We recommend downloading and using CCleaner, a free Windows Registry cleaner tool to clean your registry. To clean your registry using CCleaner, please perform the following tasks:. Click the Finish button to complete the installation process and launch CCleaner. Click the Scan for Issues button to check for Win Type a file name to backup the registry in the File Name text box of the Save As dialog box, and then click the Save button.
Click the Close button in the main window to exit CCleaner. Your Windows Registry should now be cleaned of any remnants or infected keys related to Win Trojans such as Win BitCoinMiner-BX can cause immense disruption to your computer activities.
The best method for avoiding infection is prevention; avoid downloading and installing programs from untrusted sources or opening executable mail attachments. Following these simple preventative measures will ensure that your computer remains free of infections like Win BitCoinMiner-BX, and provide you with interruption-free enjoyment of your computer. Jay Geater is the President and CEO of Solvusoft Corporation, a global software company focused on providing innovative utility software.
He is a lifelong computer geek and loves everything related to computers, software, and new technology. This website is using cookies. By continuing to browse, you are agreeing to our use of cookies as explained in our Privacy Policy. Solvusoft is recognized by Microsoft as a leading Independent Software Vendor, achieving the highest level of completence and excellence in software development.
Solvusoft's close relationship with Microsoft as a Gold Certified Partner enables us to provide best-in-class software solutions that are optimized for performance on Windows operating systems. To achieve a Gold competency level, Solvusoft goes through extensive independent analysis that looks for, amongst other qualities, a high level of software expertise, a successful customer service track record, and top-tier customer value.
As a Gold Certified Independent Software Vendor ISV , Solvusoft is able to provide the highest level of customer satisfaction through delivering top-level software and service solutions, which have been subject to a rigourous and continually-audited approval process by Microsoft.
Overview Aliases Behavior Risk Level: Unknown Registry Clean-Up Tool: Company Names Detection Names. Trojans Knowledgebase Article ID: Jay Geater Last Updated: You can learn more about Trojans here. Step 1 Access http: Step 2 Double-click the downloaded installer file to start the installation process.
Step 4 On the License Agreement screen that appears, select the I accept the agreement radio button, and then click the Next button. Step 7 On the Select components screen that appears, click the Next button. Step 10 On the Ready to Install screen that appears, click the Install button. Step 12 After the Installation completes, click the Finish button. Step 15 Once the update completes, select one or more drive to scan. Step 16 ClamWin starts the scanning process to detect and remove malware from your computer.
Step 1 Click https: Step 4 Click the Install button to start the installation. Step 5 Click the Finish button to complete the installation process and launch CCleaner.
Step 6 Click the Registry button in the CCleaner main window. Step 7 Click the Scan for Issues button to check for Win Step 9 Click the Yes button when CCleaner prompts you to backup the registry.
Step 10 Type a file name to backup the registry in the File Name text box of the Save As dialog box, and then click the Save button. Step 12 Click the Close button after CCleaner reports that the issues have been fixed. Step 13 Click the Close button in the main window to exit CCleaner. Conclusion Trojans such as Win Are You Still Experiencing Win Please reach out to us anytime on social media for more help: Browse Threats in Alphabetical Order: News Blog Facebook Twitter Newsletter.
Microsoft Gold Certified Company Recognized for best-in-class capabilities as an ISV Independent Software Vendor Solvusoft is recognized by Microsoft as a leading Independent Software Vendor, achieving the highest level of completence and excellence in software development.
How is the Gold Competency Level Attained?




