Why Blockchains and Identity Go Together
4 stars based on
79 reviews
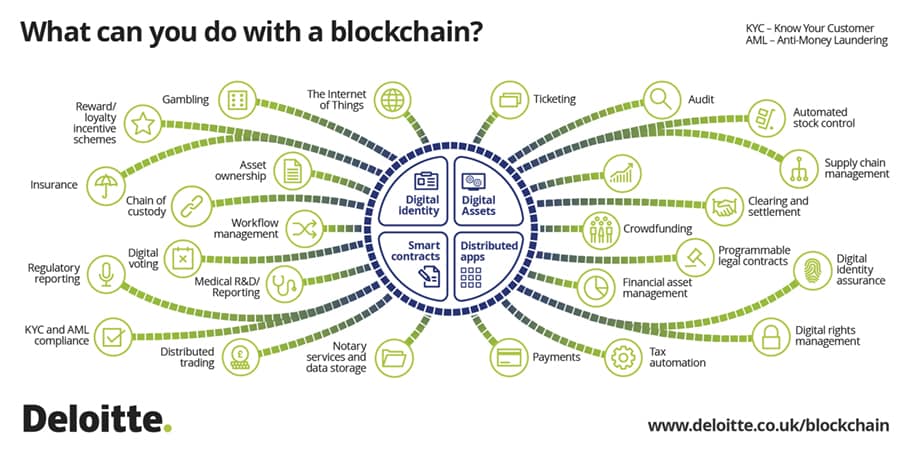
Identity is a universal problem inherent in all technology. Be it banking, healthcare, national security, online retailing or walking into a bar, identity authentication and authorization is a process intricately woven into commerce and culture worldwide. And it is often a very cumbersome, time-consuming and costly process. Blockchains change all that. Imagine having a level of data integrity that would allow you to establish trust instantly.
Imagine the operational transparency that could be achieved without deep, complex layers of IT security. Imagine authenticating your identity once and never having to do it again, despite conducting thousands of online transactions. Identity remains one of the most fascinating and fundamental use cases that many people, including me, believe to be ideal for blockchain technology.
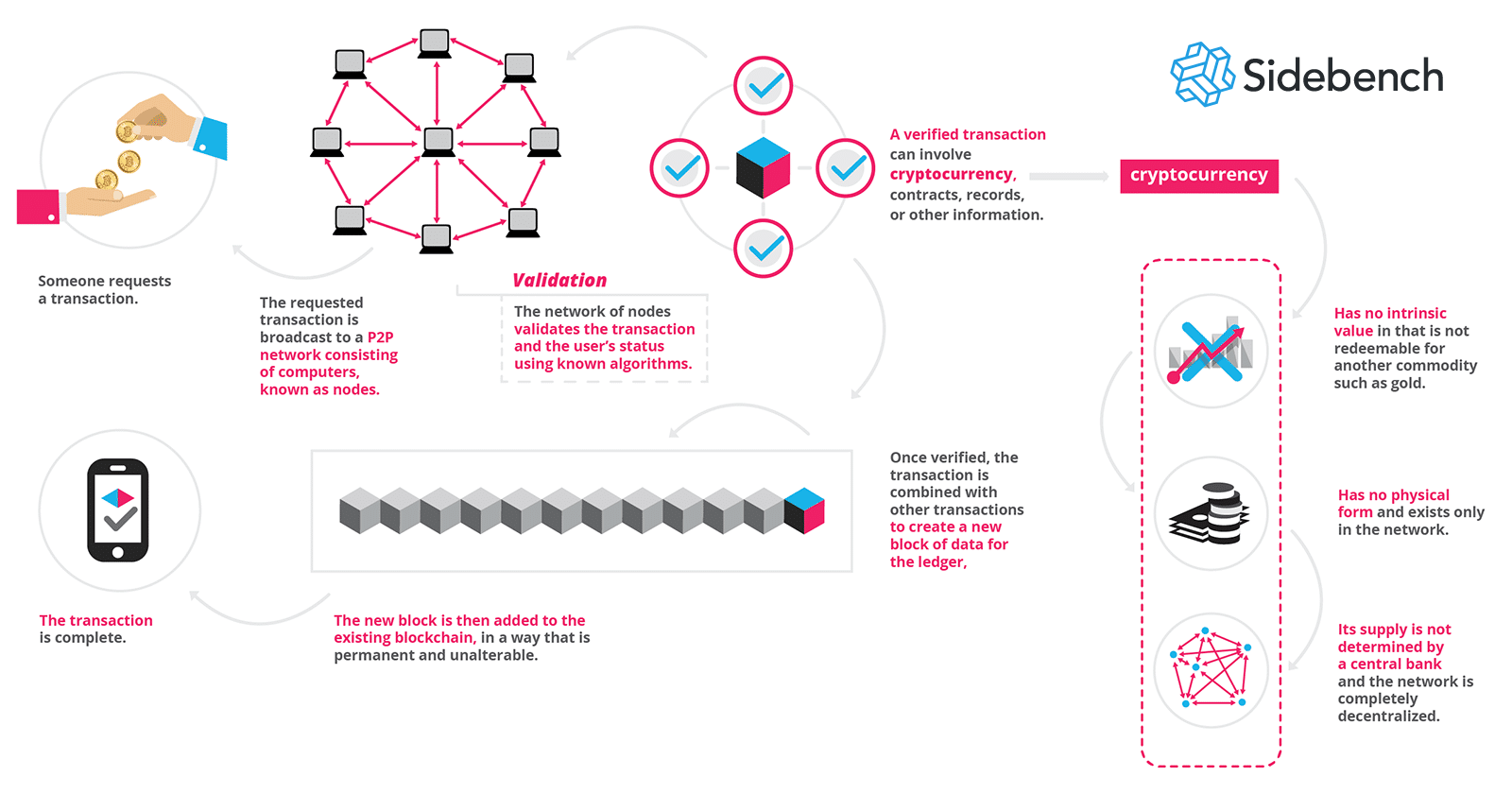
A blockchain does two things very well. It creates a network that people can use to conduct transactions or interactions using a set of rules enforced by the network blockchain identity solutions than a third party. We know this already with regard to Bitcoin, the original blockchain application. Because the other thing a blockchain excels at is identity authentication and authorization. Ensuring that a user is who he says he is, and then authorizing him to do something, is a problem that every industry has to deal with.
Over and over again, day after day, year after year. Blockchain technology is both advanced and straightforward. There have already been limited attempts to implement public key infrastructure PKI solutions for generalized authentication. What I believe is that blockchains can socialize the technology and make PKI popular. Here are a few critical ways that PKI solutions and blockchains will change how we use technology. Everyone can agree that passwords are fundamentally broken.
We literally take a secret, then share that secret with a website, which uses it to authenticate us. To ensure that it can continue authenticating us, the website stores that password in a database.
Despite best practices, we then use the exact same password on dozens if not blockchain identity solutions of other websites across the Blockchain identity solutions. Consider blockchain identity solutions Anthem Blue Cross hack. When the hacker gained access to their databases—and Anthem Blue Cross learned about it—the first thing they did was reach out to their Internet users telling them to blockchain identity solutions their passwords. What we really need is a new way to think about authentication.
Instead of blockchain identity solutions the problematic password-based system of shared secrets exchanged and stored on insecure systems, authentication systems should blockchain identity solutions based on irrefutable verification of an identity using digital signatures based on public key cryptography.
In public key cryptography, we start with a secret, called a private key. For every private key, there is exactly one matching public key that can always be mathematically derived from the private key. However, knowledge of the public key cannot reveal the private key, so you can freely and safely hand out your public key without fear of compromise.
We then use this private and public key pair to generate a digital signature. By using some special math, we can combine the private key and its corresponding public key into a third value, called a digital signature. This blockchain identity solutions signature can be handed to anyone who asks for it, and with knowledge of only the public key and the digital signature, the recipient can verify beyond a shadow of a doubt that whoever created the digital signature must have possessed blockchain identity solutions private key.
In other words, a digital signature acts as proof that its creator is who he or she says they are. What makes blockchains so much blockchain identity solutions efficient than other solutions is that the data cannot be changed. By trusting that the data cannot be changed, we can trust that private key, making it an efficient, irrefutable password.
You use one root private key—called the seed—to create unlimited public keys. You then create a new public key for each website you want to gain access to. Think of your private key as a skeleton key that gives you access to every account you have online. Now you need to keep track of only one key, instead of hundreds.
For example, if I walk into a bar, the bouncer at the door might ask to see my identification to determine if I am legally capable to drink alcohol. Unfortunately, because there is no better mechanism, I have to show him my license, which includes my age, height, eye color, address, identification number and whether or not I am an organ donor.
A capability token sent to a public key on a blockchain could be used to prove that an individual has the capability to drink. This might necessitate the creation of entirely new businesses where people are doing validations of identities. For example, the DMV could be one of the certified authorities.
It could issue a digital token that says the person is allowed to drive, another blockchain identity solutions validating drinking blockchain identity solutions. When I walk into the bar, instead of passing over my entire life story, I pass over the digital signature that proves I have the capability to drink.
We hear about the obvious one, trading and settlement, on a regular basis. However, building a strong identity platform is a blockchain identity solutions to building a blockchain solution in a business. The exchange needs to be sure that John is the one who authorized an exchange. Right now, it uses an extensive identification process that includes the delivery of a physical token used to authenticate trades.
This comes with significant cost. I believe that by having a trusted identity blockchain, this problem would become relatively minor because John Smith could be verified once, and that verification would travel with him as he trades on multiple exchanges and with multiple banks.
Blockchain identity solutions procedures require extensive, repeated blockchain identity solutions. Blockchain solutions can tremendously advance the simplification and efficiency of KYC protocols, saving time and money and eliminating password problems while reducing the resources needed to manage the information collection process.
For example, blockchain technology would allow banks to share KYC information as long as they trust the first bank that collected it.
If you take this further, blockchain identity solutions technology would encourage the emergence of KYC collection companies that establish trust relationships with banks and do all the KYC collection up front, so banks blockchain identity solutions have to collect or store the data themselves. The customer would go through the process very rarely, rather than every time they sign up for a financial service. Storing KYC data is incredibly expensive and exposes banks to security risks because it makes them targets for identity thieves.
Putting KYC management on a blockchain blows wide open the opportunity for more secure, less costly KYC management systems. Blockchains help solve many general IT security issues, such as passwords and authorized identification for blockchain identity solutions actions, but they also provide an environment where individuals are in control of their personal data.
The amount of information that is presently shared with employers, potential partners and other entities is unnecessary. So long as there is a digital signature proving that an individual has the capability to do something, no other information should need to be saved. Sophisticated identity frameworks will be a requirement for building secure blockchain networks.
New opportunities for blockchain applications will develop alongside HD identity security. The Key to Irrefutable Data Integrity. Fixing the Password Problem Everyone can agree that passwords are fundamentally broken.