Liquifilm allergan botox
10 comments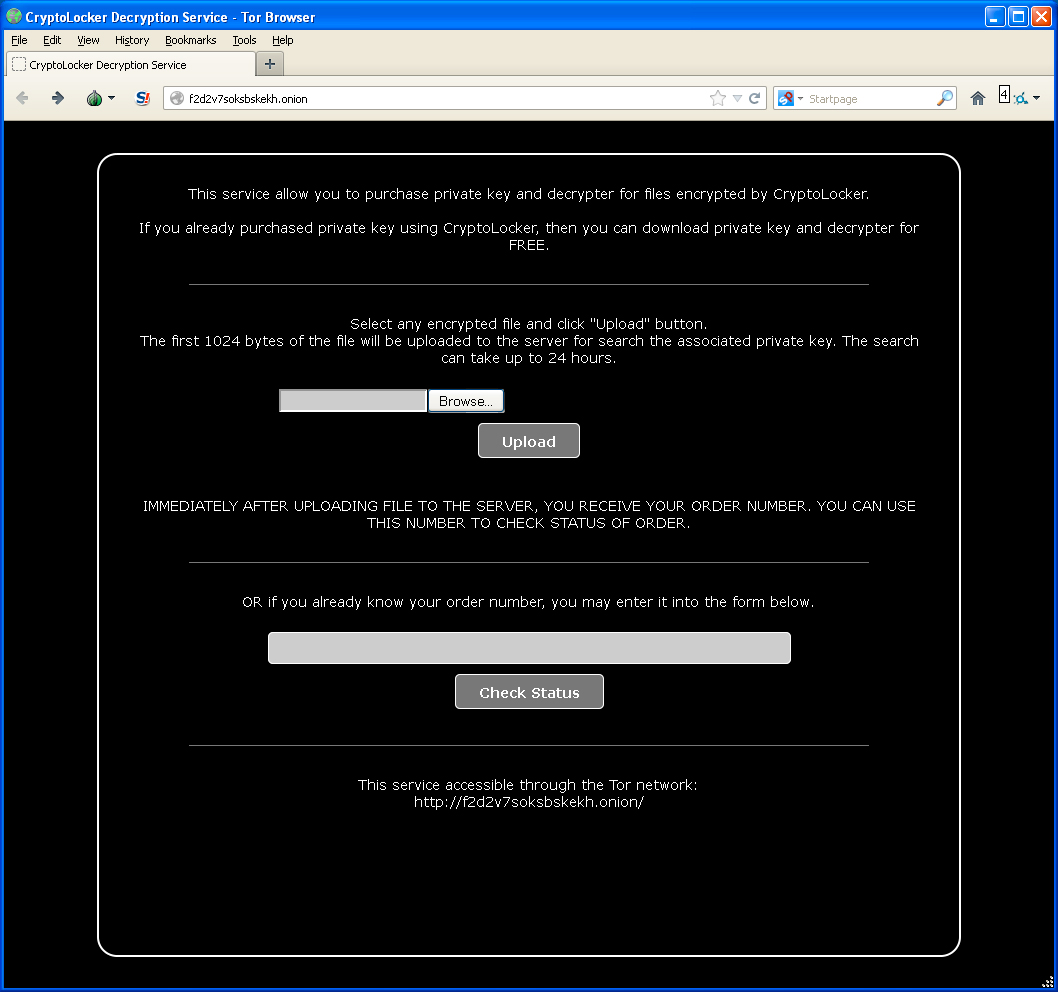
Selgin bitcoin chart
This message is left by CryptoLocker for victims whose antivirus software removes the file needed to pay the ransom. To recap, CryptoLocker is a diabolical new twist on an old scam. The malware encrypts all of the most important files on a victim PC — pictures, movie and music files, documents, etc. Victims who pay the ransom receive a key that unlocks their encrypted files; those who let the timer expire before paying risk losing access to their files forever.
Part of the problem, according to Abrams, is that few victims even know about Bitcoins or MoneyPak, let alone how to obtain or use these payment mechanisms. The people who did pay with Bitcoins said they found the process for getting them was so cumbersome that it took them a week to figure it out. The idea of purposefully re-infecting a machine by downloading and executing highly destructive malware may be antithetical and even heresy to some security pros.
But victims who are facing the annihilation of their most precious files probably have a different view of the situation. And those victims will no longer have the option to pay the ransom via MoneyPak.
Abrams said the service exposes two lies that the attackers have been perpetuating about their scheme. For starters, the bad guys have tried to dissuade victims from rolling back their system clocks to buy themselves more time to get the money together and pay the ransom. According to Abrams, this actually works in many cases to delay the countdown timer.
The result is perhaps the most detailed analysis yet of the business case for the malicious software and spam epidemics that persist to this day. Spam — and all of its attendant ills — will remain a prevalent and pestilent problem because consumer demand for the products most frequently advertised through junk email remains constant. The researchers found that repeat customers are critical to making any rogue pharmacy business profitable.
Whether the placebo effect is something that often applies with the consumption of erectile dysfunction drugs is not covered in this research paper, but ED drugs were by far the largest category of pills ordered by customers of all three pharmacy programs. One interesting pattern that trickled out of the Rx-Promotion data underscores what made this pharmacy affiliate unique and popular among repeat buyers: A major portion of its revenues was generated through the sale of drugs that have a high potential for abuse and are thus tightly controlled in the United States, including opiates and painkillers like Oxycodone , Hydrocodone , and mental health pills such as Adderall and Ritalin.
The researchers noticed that although pills in this class of drugs — known as Schedule II in U. The cybercrime underground is expanding each day, yet the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers. That suspicion was reinforced this week when I discovered that the author of the infamous ZeuS Trojan was a core member of Spamdot , until recently the most exclusive online forum for spammers and the shady businessmen who support the big spam botnets.
Thanks to a deep-seated enmity between the owners of two of the largest spam affiliate programs, the database for Spamdot was leaked to a handful of investigators and researchers, including KrebsOnSecurity. In , I learned from multiple reliable sources that for several months, this account was used exclusively by the ZeuS author to communicate with new and existing customers. The messages also provide a virtual black book of customers who purchased the ZeuS bot code.
This is a very reasonable fee and is in line with rates charged by more organized pay-per-install businesses that also tend to stuff host PCs with so much other malware that customers who have paid to load their bots on those machines soon find them unstable or unusable. Other members apparently recognized it as a bargain as well, and he quickly received messages from a number of interested takers. The image below shows the Zeus author parceling out a small but potentially valuable spam resource that was no doubt harvested from systems compromised by his Trojan.
In this solicitation, dated Jan. Google rented his crime machine to members of SpamIt , an organization that paid spammers to promote rogue Internet pharmacy sites. Srizbi burst onto the malware scene in early , infecting hundreds of thousands of Microsoft Windows computers via exploit kits stitched into hacked and malicious Web sites. This page from archive. He asks customers and would-be clients to contact him via ICQ instant message ID the importance of this number will be apparent later in the story.
The logs were leaked online last year after Russian investigators questioned Stupin as part of an investigation into Igor Gusev , the alleged other co-founder of SpamIt. Facing criminal charges for his alleged part in SpamIt, Gusev chose to shutter the program October , but not before its affiliate database was stolen and also leaked online.
SPM is introduced to SpamIt in May , when he joins the program with the hopes of becoming the default spam software provider for the pharmacy affiliate program. Very soon after joining SpamIt, SPM identifies Google — the Cutwail botmaster — as his main competitor, and sets off to undermine Google and to become the default spam software provider to SpamIt. Previous stories in my Pharma Wars series have identified top kingpins behind the some of the biggest spam botnets.
For many years, Cutwail has been among the top three most prolific spam botnets. With the recent takedown of the Rustock botnet , Cutwail now is the top spam bot; according to M86 Security , versions of Cutwail are responsible for about 22 percent of the daily spam volumes worldwide.
Security researchers have extensively dissected the technical machinery that powers Cutwail a. By the time he joined SpamIt in early , the hacker named Google had already spent several years fine-tuning his spam botnet.
Just months prior to its closure in Oct. But Google would make far more money renting his botnet to other spammers, and SpamIt affiliates quickly became his biggest client base. They also provide tantalizing clues as to the real-life identity of Google and his co-workers. Snippets of those conversations appear below, translated from their original Russian into English by native Russian speakers.
Some of the best techical analysis of Cutwail came earlier this year in a paper from researchers at the University of California, Santa Barbara and Ruhr-University Bochum , which described in detail how the Cutwail botnet was operated, rented and promoted on the exclusive SpamIt forums. From their paper PDF:. These affiliates pay a fee to Cutwail botmasters in order to use their botnet infrastructure.
SpamIt affiliate records show that Google registered with the program using the email address psyche. In several chats with Stupin, Google describes how he and his pals switched to pharmacy spamming when promoting stocks via spam became less lucrative. In a discussion on Feb. We organized people, gave them tasks to do. Security researchers have dealt a mighty blow to a spam botnet known as Pushdo , a massive grouping of hacked PCs that until recently was responsible for sending more than 10 percent of all junk e-mail worldwide.
According to security firm M86 Security Labs , junk e-mail being relayed by Pushdo a. Cutwail tapered off from a torrent to a dribble over the past few days. M86 credits researchers at LastLine Inc. Holz said Lastline contacted all hosting providers and worked with them to take down the machines, which lead to the takedown of nearly 20 of those control servers.
Many connection attempts fail and infected machines can not receive commands anymore. Follow me on Twitter. Join me on Facebook. Krebs on Security In-depth security news and investigation. Reactor Mailer Terms of Service, December spam stats from M86Security.
Your email account may be worth far more than you imagine.