Quantum cryptography bitcoin mineral
Bitcoin is taking the world by storm. The decentralized digital currency is a secure payment platform that anybody can use. It is free from government interference and operated by an open, peer-to-peer network.
This independence is one reason Bitcoin has become so popular, causing its value to rise steeply. A crucial feature of Bitcoin is its security. Bitcoins have two important security features that prevent them from being stolen or copied. Both are based on cryptographic protocols that are hard to crack. In other words, they exploit mathematical functions, like factorization, that are easy in one direction but hard in the other—at least for an ordinary classical computer.
But there is a problem on the horizon. Quantum computers can solve these problems easily. And the first quantum computers are currently under development. That raises an urgent question: Today, we get an answer thanks to the work of Divesh Aggarwal at the National University of Singapore and a few pals. These guys have studied the threat to Bitcoin posed by quantum computers and say that the danger is real and imminent.
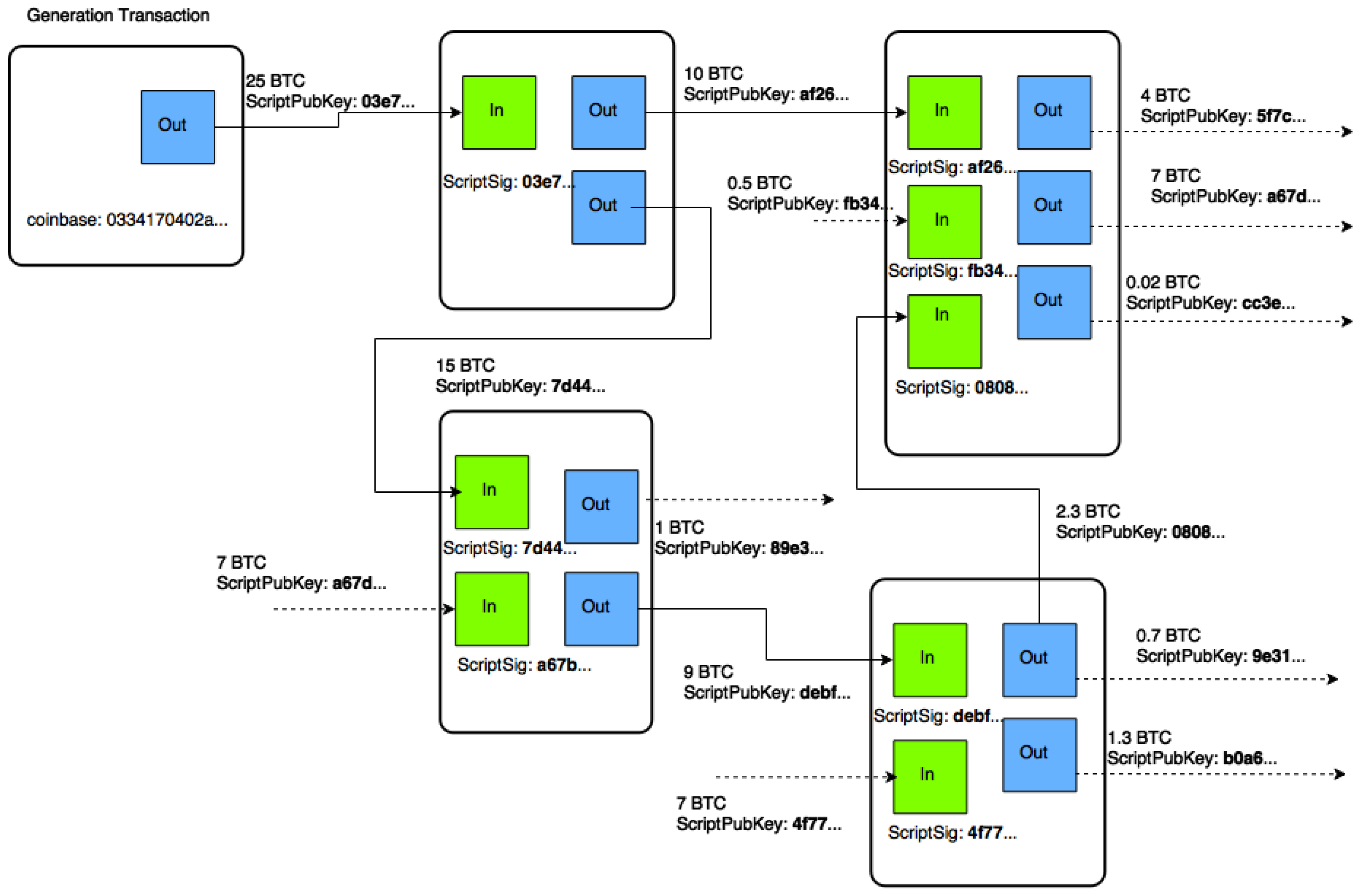
Bitcoin transactions are stored in a distributed ledger that collates all the deals carried out in a specific time period, usually about 10 minutes. This collection, called a block, also contains a cryptographic hash of the previous block, which contains a cryptographic hash of the one before that, and so on in a chain.
Hence the term blockchain. A hash is a mathematical function that turns a set of data of any length into a set of specific length. The new block must also contain a number called a nonce that has a special property. When this nonce is hashed, or combined mathematically, with the content of the block, the result must be less than some specific target value.
Given the nonce and the block content, this is easy to show, which allows anybody to verify the block. But generating the nonce is time consuming, since the only way to do it is by brute force—to try numbers one after the other until a nonce is found. This process of finding a nonce, called mining, is rewarded with Bitcoins.
Mining is so computationally intensive that the task is usually divided among many computers that share the reward. The block is then placed on the distributed ledger and, once validated, incorporated into the blockchain. The miners then start work on the next block. Occasionally, two mining groups find different nonces and declare two different blocks.
The Bitcoin protocol states that in this case, the block that has been worked on more will be incorporated into the chain and the other discarded. In that case, it effectively controls the ledger. If it is malicious, it can spend bitcoins twice, by deleting transactions so they are never incorporated into the blockchain. The other 49 percent of miners are none the wiser because they have no oversight of the mining process.
That creates an opportunity for a malicious owner of a quantum computer put to work as a Bitcoin miner. If this computational power breaks the 50 percent threshold, it can do what it likes. Their conclusion will be a relief to Bitcoin miners the world over.
Aggarwal and co say that most mining is done by application-specific integrated circuits ASICs made by companies such as Nvidia. But there is a different threat that is much more worrying. Bitcoin has another cryptographic security feature to ensure that only the owner of a Bitcoin can spend it.
This is based on the same mathematics used for public-key encryption schemes. The idea is that the owner generates two numbers—a private key that is secret and a public key that is published. The public key can be easily generated from the private key, but not vice versa.
A signature can be used to verify that the owner holds the private key, without revealing the private key, using a technique known as an elliptic curve signature scheme.
In this way, the receiver can verify that the owner possesses the private key and therefore has the right to spend the Bitcoin. Get on top of reliability with our best practices webinar. Sony reports shortage of cute robot puppies!
Predictable senility allows boffins to spot recycled NAND chips Waymo van prang, self-driving cars still suck, AI research jobs, and more Congratulations, we all survived Star Wars day! Now for some security headaches. Verity Stob Yes, people see straight through male displays of bling they're only after a fling New Monty Python movie to turn old jokes into new royalties Mystery crapper comes a cropper The steaks have never been higher: Swiss Lidl is selling local cannabis.
An international group of quantum boffins reckons Bitcoin could be broken by the year Most read Equifax reveals full horror of that monstrous cyber-heist of its servers Zombie Cambridge Analytica told 'death' can't save it from the law Heir to SMS finally excites carriers, by making Google grovel Microsoft: Our most popular server product of all time runs on Linux Admin needed server fast, skipped factory config … then bricked it.
More from The Register. Microsoft ports its Quantum Development Kit to Linux and macOS Now that it's not Windows-only, you can simulate a theoretical computer on a real computer. Google, Volkswagen spin up quantum computing partnership Pair to work on traffic optimisation and better batteries. Microsoft asks devs for quantum leap of faith Try writing quantum code in Q , because Alibaba fires up a cloudy quantum computer Five-qubit creation is behind the great firewall and outside it at the same time!
I spy with my little eye This paper suggests a battery of technical checks that testers can quickly perform to stratify the vast array of applications that exist in the enterprise ecosystem. Using OutSystems, AXA plans to continuously improve the eServe portal so it can provide additional benefits to brokers and customers. The ascendancy of the multi-cloud world gives you some new things to worry about and some old ones to relax about. Sponsored links Get The Register's Headlines in your inbox daily - quick signup!
About us Who we are Under the hood Contact us Advertise with us. Sign up to our Newsletters Join our daily or weekly newsletters, subscribe to a specific section or set News alerts Subscribe.