Quantum cryptography bitcoin network
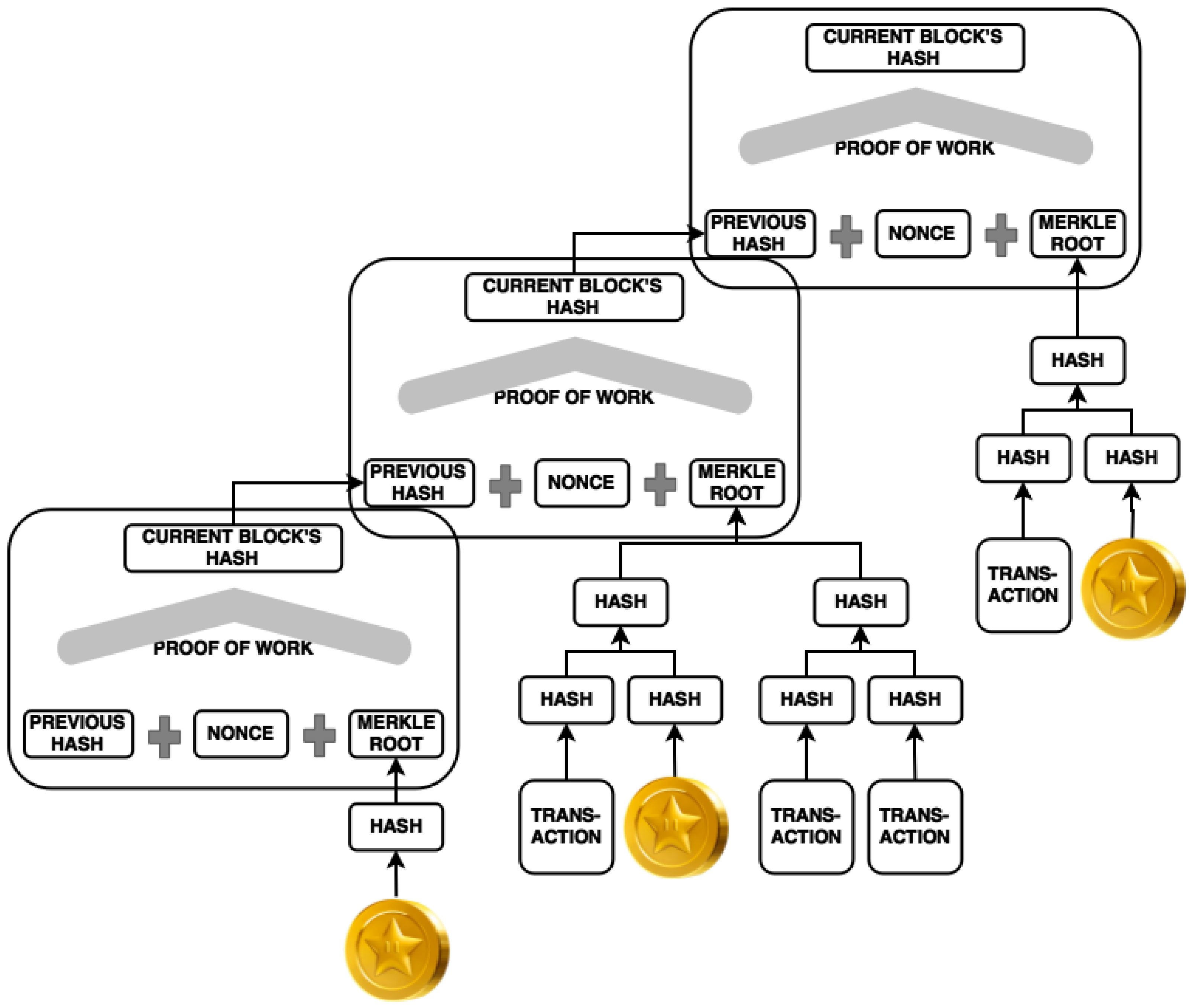
The miners then start work on the next block. Occasionally, two mining groups find different nonces and declare two different blocks. The Bitcoin protocol states that in this case, the block that has been worked on more will be incorporated into the chain and the other discarded.
In that case, it effectively controls the ledger. If it is malicious, it can spend bitcoins twice, by deleting transactions so they are never incorporated into the blockchain. The other 49 percent of miners are none the wiser because they have no oversight of the mining process. That creates an opportunity for a malicious owner of a quantum computer put to work as a Bitcoin miner.
If this computational power breaks the 50 percent threshold, it can do what it likes. Their conclusion will be a relief to Bitcoin miners the world over. Aggarwal and co say that most mining is done by application-specific integrated circuits ASICs made by companies such as Nvidia.
But there is a different threat that is much more worrying. Bitcoin has another cryptographic security feature to ensure that only the owner of a Bitcoin can spend it. This is based on the same mathematics used for public-key encryption schemes. The idea is that the owner generates two numbers—a private key that is secret and a public key that is published.
The public key can be easily generated from the private key, but not vice versa. A signature can be used to verify that the owner holds the private key, without revealing the private key, using a technique known as an elliptic curve signature scheme.
In this way, the receiver can verify that the owner possesses the private key and therefore has the right to spend the Bitcoin. The only way to cheat this system is to calculate the private key using the public key, which is extremely hard with conventional computers. But with a quantum computer, it is easy. Indeed, quantum computers pose a similar risk to all encryption schemes that use a similar technology, which includes many common forms of encryption.
There are public-key schemes that are resistant to attack by quantum computers. So it is conceivable that the Bitcoin protocols could be revised to make the system safer. But there are no plans to do that now. Bitcoin is no stranger to controversy. It has weathered various storms over its security.
But that is no guarantee that it will cope well in the future. One thing is sure: Become an Insider to get the story behind the story — and before anyone else. Operating a botnet is expensive and risky. Everything included in Insider Basic, plus the digital magazine, extensive archive, ad-free web experience, and discounts to partner offerings and MIT Technology Review events.
Unlimited online access including all articles, multimedia, and more. The Download newsletter with top tech stories delivered daily to your inbox. Technology Review PDF magazine archive, including articles, images, and covers dating back to Six issues of our award winning print magazine, unlimited online access plus The Download with the top tech stories delivered daily to your inbox.
Unlimited online access including articles and video, plus The Download with the top tech stories delivered daily to your inbox. Revert to standard pricing. Hello, We noticed you're browsing in private or incognito mode. Subscribe now for unlimited access to online articles. Why we made this change Visitors are allowed 3 free articles per month without a subscription , and private browsing prevents us from counting how many stories you've read. Business Impact Quantum Computers Pose Imminent Threat to Bitcoin Security The massive calculating power of quantum computers will be able to break Bitcoin security within 10 years, say security experts.
Recommended for You Net neutrality gets a thumbs-up from US senators, but it still looks doomed. A stealthy Harvard startup wants to reverse aging in dogs, and humans could be next. Ride-sharing apps Uber and Didi equate surveillance with safety.
These cows are modeling the tracking technology of the future. The researchers from Singapore, Australia and France say that scenario represents the worst case, and would see a quantum computer able to run Shor's algorithm against the cryptocurrency's protective elliptic curve signature quicker than the 10 minutes Bitcoin needs to record a transaction in the blockchain.
There are two items of good news in the paper for Bitcoin: In their paper , which landed at arXiv in late October, Divesh Aggarwal and his collaborators say ASIC-based mining rigs are fast compared to even optimistic theoretical quantum computer clock speeds.
The extreme speed of current specialized ASIC hardware for performing the hashcash PoW, coupled with much slower projected gate speeds for current quantum architectures, essentially negates this quadratic speedup, at the current difficulty level, giving quantum computers no advantage. Future improvements to quantum technology allowing gate speeds up to GHz could allow quantum computers to solve the PoW about times faster than current technology.
As far as defeating hashcash goes, the numbers are daunting for quantum computer designers: Shor's algorithm, a quantum algorithm for factoring integers that's how it would attack cryptography , is a better path, they write. Deploying a quantum computer against the secpk1 elliptic curve Bitcoin uses is much more dangerous: As with cracking the proof-of-work, the researchers assume quantum computers get big and fast relatively quickly, and even so, they fall slightly short: Minds Mastering Machines - Call for papers now open.
The Register - Independent news and views for the tech community. Part of Situation Publishing. Join our daily or weekly newsletters, subscribe to a specific section or set News alerts. The Register uses cookies. It's ISC in Frankfurt. Software development slow because 'Most of our ideas suck' Void Linux gave itself to the void, Korora needs a long siesta — life is hard for small distros Google shoots Chrome 66's silencer after developer backlash Oracle-botherer Rimini Street cuddles up to Salesforce.
Update right now to get rid of the static admin credential Hutchins lawyers claim intoxicated calls aren't proper evidence Mining apps? We're cool so long as they admit to it, says Canonical. Agile development exposed as techie superstition Serverless continuous deployment for the AWS crowd: Feeding time in Lambda-land Hey cool, you went serverless. Now you just have to worry about all those stale functions You're in charge of change, and now you need to talk about DevOps hater Robin.
Policy The Channel Net neutrality is saved in Senate vote! No, not really, it was a giant waste of everyone's time UK has rejected over 1, skilled IT bod visa applications this year Privacy group asks UK politicos to pinky swear not to use personal data for electioneering US senators ask FTC to investigate Google's Location imbroglio.