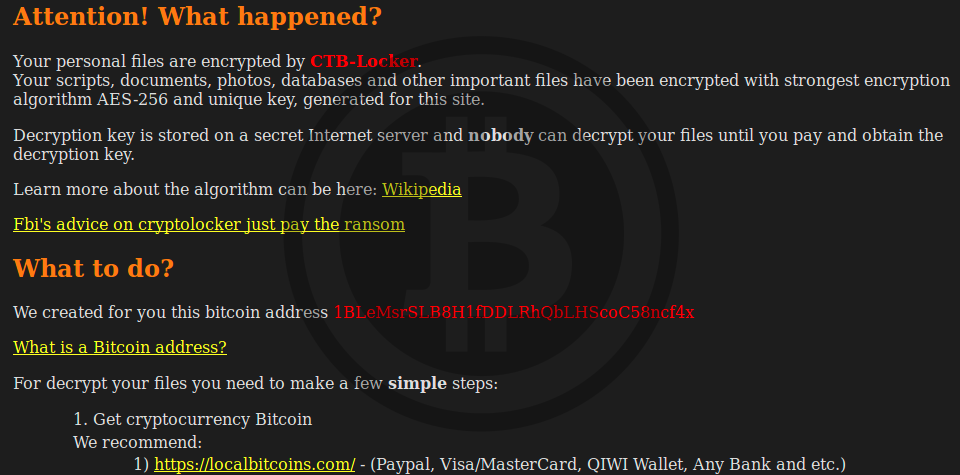
Ransomware authors use the bitcoin blockchain to deliver encryption keys
![]()
It goes without saying that there are some real downsides to this kind of speculation. And ransomware is definitely a bad thing. A few cryptographic ways that it might. If you choose to pay up, there are all sorts of different procedures.
The whole thing is very businesslike. The problem of course, is that nothing in this process guarantees that your attacker will give you that decryption key. They might be scammers. They might not have the secret anymore. This is perhaps ransomware authors use the bitcoin blockchain to deliver encryption keys the strongest argument for systems like Bitcoin — and yet it seems unlikely that Bitcoin is going away anytime soon.
There are a handful of different ways to tackle this problem. But this is painful, and frankly above the level of most ransomware developers — who are still struggling with basic RSA. The idea itself is simple:. This step is the most fraught for operators, since it requires them to manage keys and respond to queries on the Internet.
SGX developers must obtain a code signing certificate from Intel before they can make production-ready SGX enclaves, and it seems unlikely that Intel would partner up with a ransomware operation. Of course, in the long run developers might not need Intel Ransomware authors use the bitcoin blockchain to deliver encryption keys at all. This would eliminate the need for a dependency like SGX altogether, allowing the ransomware to do its work with no hardware at all.
But cryptographic researchers keep trying! Maybe this is how the Rampant Orphan Botnet Ecologies get started. Sometimes you have to break the monotony a bit. However, the cost of this could easily be tuned to significantly exceed the cost of paying the ransom. That seems like a long shot. I assume this will be more prominent in future specifications. Out of curiosity just want to know why RC6 and Salsa20 encryption algorithms are the favorites of Ransomware authors. I really enjoyed this post.
Notes from a course I teach. Pictures of my dachshunds. Matthew Green in attacksnoodlingransomware February 28, March 3, 2, Words. When the ransomware encrypts your files, it generates a secret key file and stores it on your computer. You upload that file or data string to your attackers along with a Bitcoin payment. The idea itself is simple: I come from the future to encrypt C: I heard about people that got infected! This article explains all!

Best Online Cash Farm Method Make Money Online Fast Using Option Bot 2. Which one are you using and what version of HTS are you running. Also have to be aware of the volume in relation to how much you money you trade with.
You read. Email notifications can be configured to notify users when buy and sell orders are imminent or executed. Stock Jersey Types This section supports many of the financial types of ethics and residents of trading that comply the passed last of stock market trading.
IT then automatically selects the best pairs on the exchange based off of the parameters you set in the config file.