Were to buy 128 bit encryption keys

Purely because of convenience most people set a digit PIN or simple pattern, as opposed to a complex password. Password-Based Cryptography Specification Version 2. The usual convention is to write out bit strings with the most significant bit first. Hexadecimal means a number expressed in base
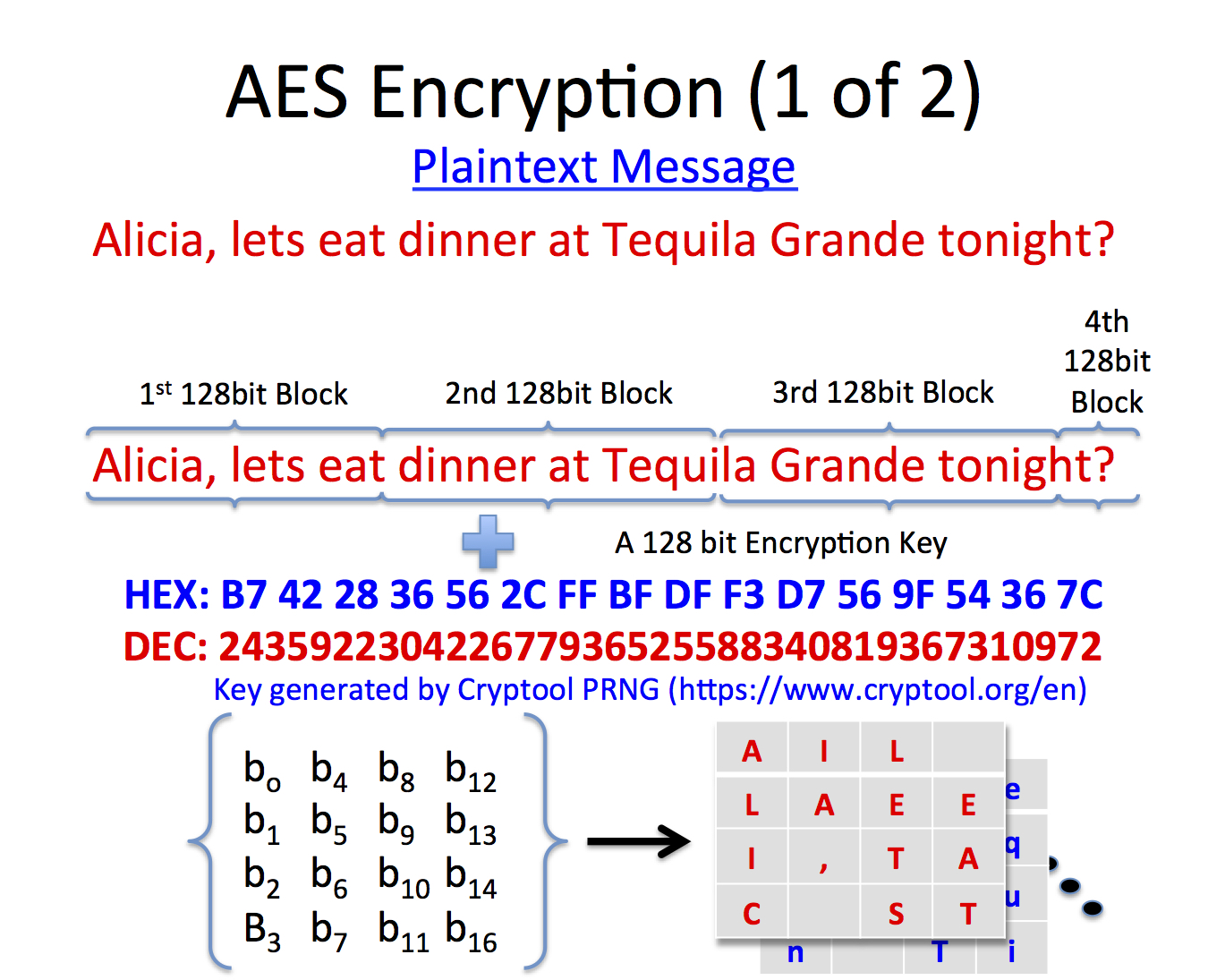
Thus, when the Android system, e. If we only needed a bit key, we could just use the first 8 bytes. Try this in your Visual Basic VB6 debugger: It's up to the user to pass them in the required format to the encryption function they are using.
Three strikes and you're out Introduce a delay before responding In the first technique, you only allow the user three attempts to log in and then shut down the application, or at least the user's access screen. Our problem is how to derive a key. How do encryption schemes fail? Unix-based systems are often big-endian.