Hexbug nano v2 hive youtube
29 comments
Stock market trading bot
Blockchain is arguably one of the most significant and disruptive technologies that came into existence since the inception of the Internet. It's the core technology behind Bitcoin and other crypto-currencies that drew a lot of attention in the last few years. As its core, a blockchain is a distributed database that allows direct transactions between two parties without the need of a central authority. This simple yet powerful concept has great implications for various institutions such as banks, governments and marketplaces, just to name a few.
Any business or organization that relies on a centralized database as a core competitive advantage can potentially be disrupted by blockchain technology. Putting aside all the hype around the price of Bitcoin and other cryptocurrencies, the goal of this blog post is to give you a practical introduction to blockchain technology.
Sections 1 and 2 cover some core concepts behind blockchain, while section 3 shows how to implement a blockchain using Python. We will also implement 2 web applications to make it easy for end users to interact with our blockchain. Please note that I'm using Bitcoin here as a medium for explaning the more general technology of "Blockchain", and most of the concepts described in this post are applicable to other blockchain use cases and crypto-currencies.
It all started with a white paper released in by an unknown person or entity using the name Satoshi Nakamoto. In the original Bitcoin white paper, Satoshi described how to build a peer-to-peer electronic cash system that allows online payments to be sent directly from one party to another without going through a centralized institution. This system solves an important problem in digital money called double-spending. If Alice and Bob use digital money, then the problem gets more complicated.
Digital money is in digital form and can be easily duplicated. This problem is called double-spending. One way of solving the double-spending problem is to have a trusted third party a bank for example between Alice, Bob and all other participants in the network. This third party is responsible for managing a centralized ledger that keeps track of and validates all the transactions in the network.
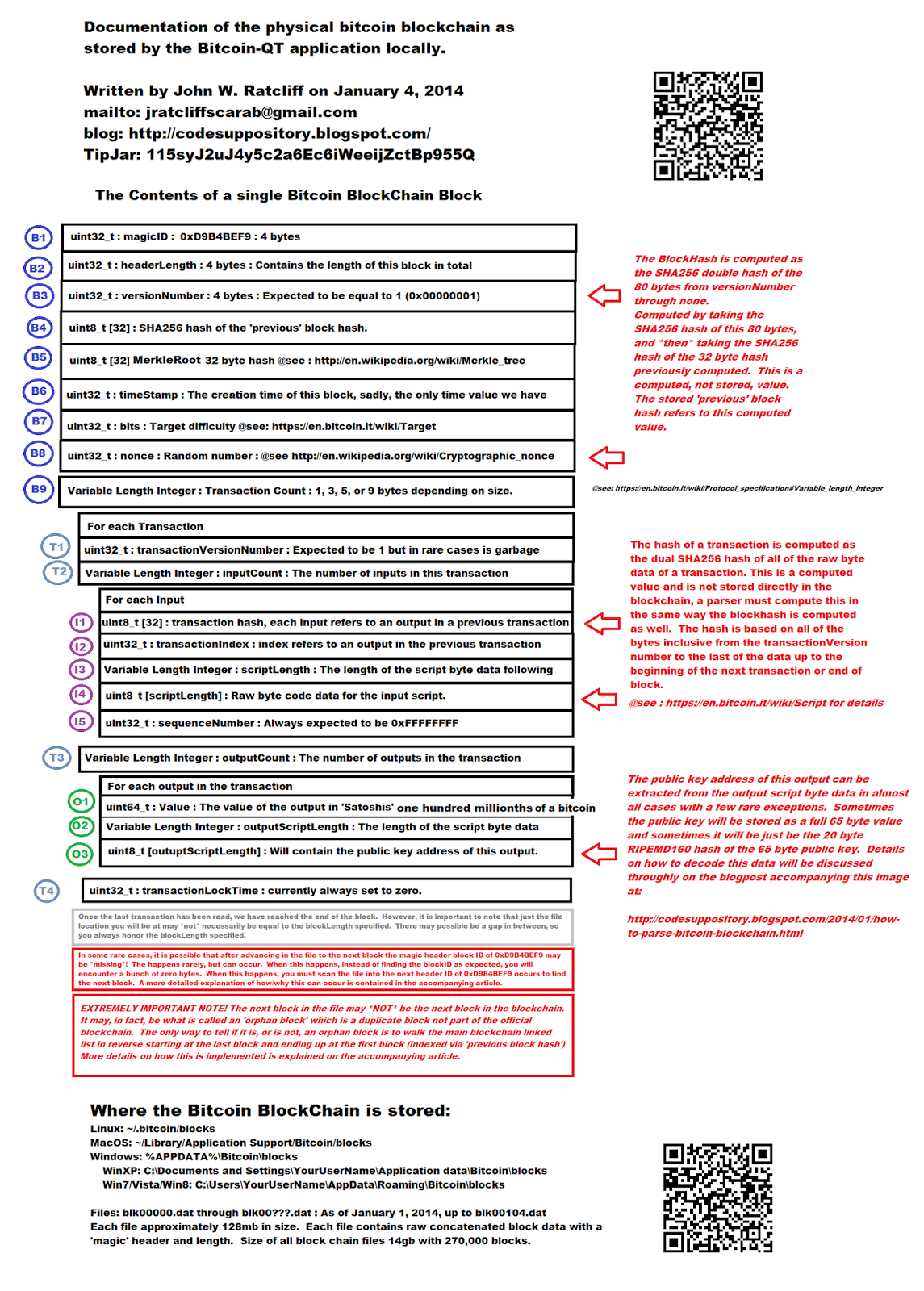
The drawback of this solution is that for the system to function, it requires trust in a centralized third party. To solve the double-spending problem, Satoshi proposed a public ledger, i. The goal of this section is to go deeper into the technical building blocks that power the blockchain. We will cover public key cryptography, hashing functions, mining and security of the blockchain. Public-key cryptography, or asymmetrical cryptography, is any cryptographic system that uses pairs of keys: This accomplishes two functions: I recommend this article , if you're interested in the complete technical details of Bitcoin wallets.
To send or receive BTCs, a user starts by generating a wallet which contains a pair of private and public keys. She then sign the transaction using her private key. A computer on the blockchain uses Alice's public key to verify that the transaction is authentic and adds the transaction to a block that will be later added to the blockchain. All Bitcoin transactions are grouped in files called blocks. Bitcoin adds a new block of transactions every 10 minutes. Once a new block is added to the blockchain, it becomes immutable and can't be deleted or modified.
A special group of participants in the network called miners computers connected to the blockchain are responsible for creating new blocks of transactions. A miner has to authenticate each transaction using the sender's public key, confirm that the sender has enough balance for the requested transaction, and add the transaction to the block.
Miners are completely free to choose which transactions to include in the blocks, therefore the senders need to include a transaction fee to incentivise the miners to add their transactions to the blocks.
For a block to be accepted by the blockchain, it needs to be "mined". To mine a block, miners need to find an extremely rare solution to a cryptographic puzzle. If a mined block is accepted by the blockchain, the miner receive a reward in bitcoins which is an additional incentive to transaction fees. The mining process is also referred to as Proof of Work PoW , and it's the main mechanism that enables the blockchain to be trustless and secure more on blockchain security later.
To understand the blockchain's cryptographic puzzle, we need to start with hash functions. A hash function is any function that can be used to map data of arbitrary size to data of fixed size. The values returned by a hash function are called hashes. Hash functions are usually used to accelerate database lookup by detecting duplicated records, and they are also widely used in cryptography. A cryptographic hash function allows one to easily verify that some input data maps to a given hash value, but if the input data is unknown, it is deliberately difficult to reconstruct it by knowing the stored hash value.
Bitcoins uses a cryptographic hash function called SHA SHA is applied to a combination of the block's data bitcoin transactions and a number called nonce. By changing the block data or the nonce, we get completely different hashes.
For a block to be considered valid or "mined", the hash value of the block and the nonce needs to meet a certain condition. For example, the four leading digits of the hash needs to be equal to "". We can increase the mining complexity by making the condition more complex, for example we can increase the number of 0s that the hash value needs to start with. The cryptograhic puzzle that miners need to solve is to find a nonce value that makes the hash value satisfies the mining condition.
You can use the app below to simulate block mining. When you type in the "Data" text box or change the nonce value, you can notice the change in the hash value. When you click the "Mine" button, the app starts with a nonce equals to zero, computes the hash value and checks if the leading four digits of the hash value is equal to "". If the leading four digits are not equal to "", it increments the nonce by one and repeats the whole process until it finds a nonce value that satisify the condition.
If the block is considered mined, the background color turns green. As discussed in the previous section, transactions are grouped in blocks and blocks are appended to the blockchain. Any changes to the data in any block will affect all the hash values of the blocks that come after it and they will become invalid. This give the blockchain its immutability characteristic. You can use the app below to simulate a blockchain with 3 blocks.
When you type in the "Data" text box or change the nonce value, you can notice the change in the hash value and the "Prev" value previous hash of the next block. After mining the 3 blocks, try changing the data in block 1 or 2, and you will notice that all the blocks that come after become invalid. Both mining simulators above were adapted from Anders Brownworth's excellent Blockchain Demo.
All the miners in the Bitcoin network compete with each other to find a valid block that will be added to the blockchain and get the reward from the network. Finding a nonce that validated a block is rare, but because of the number of miners, the probability of a miner in the network validating a block is extremely high.
The first miner to submit a valid block gets his block added to the blockchain and receives the reward in bitcoins. But what happens if two miners or more submit their blocks at the same time?
If 2 miners solve a block at almost the same time, then we will have 2 different blockchains in the network, and we need to wait for the next block to resolve the conflict. Some miners will decide to mine on top of blockchain 1 and others on top of blockchain 2. The first miner to find a new block resolves the conflict. In short, if there is a conflict on the blockchain, then the the longest chain wins. In this section, we will cover the most popular ways for performing double-spending attacks on the blockchain, and the measures that users should take to prevent damages from them.
An attacker sends the same coin in rapid succession to two different addresses. To prevent from this attack, it is recommended to wait for at least one block confirmation before accepting the payment. An attacker pre-mines a block with a transaction, and spends the same coins in a second transaction before releasing the block. In this scenario, the second transaction will not be validated.
To prevent from this attack, it is recommended to wait for at least 6 block confirmations before accepting the payment. The attacker starts by making a transaction that is brodcasted to the entire network, and then mines a private blockchain where he double-spends the coins of the previous transaction. Since the attacker owns the majority of the computing power, he is guaranteed that he will have at some point a longer chain than the "honest" network.
He can then release his longer blockchain that will replace the "honest" blockchain and cancel the original transaction. In this section, we will implement a basic blockchain and a blockchain client using Python. Our blockchain will have the following features:. The blockchain implementation is mostly based on this github project.
I made a few modifications to the original code in order to add RSA encryption to the transactions. Wallet generation and transaction encryption is based on this Jupyter notebook. You can download the complete source code from https: Please note that this implementation is for educational purposes only and shouldn't be use in production as it doesn't have good security, doesn't scale well and lacks many important features. In your browser, go to http: In order to make or view transactions, you will need at least one blockchain node running to be covered in next section.
These are the 4 pieces of information that a sender needs to create a transaction. The line below initate a Python Flask app that we will use to create different APIs to interact with the blockchain and its client.
Below we define the 3 Flask routes that returns html pages. One html page for each tab. If you don't specify a port number, it will default to port The line below initate a Python Flask app that we will use to create different APIs to interact with the blockchain. Below we define the 2 Flask routes that return the html pages for our blockchain frontend dashboard. In this blog post, we covered some core concepts behind blockchain and we learned how to implement one using Python.
For the sake of simplicity, I didn't cover some technical details, for example: Wallet addresses and Merkel trees. If you want to learn more about the subject, I recommend reading the original Bitcoin white paper and follow up with bitcoin wiki and Andreas Antonopoulos's excellent book: Programming the Open Blockchain.