These photos show you inside an Icelandic bitcoin mine
5 stars based on
57 reviews
The glorious view from our windows at Cornell Tech takes in Park Avenue, the tallest residential building in the world. This tower is a monument to many things. Above all, for a student of Financial systems, it epitomizes ways to store wealth with breathtaking waste. Fittingly, it was inspired by a wastepaper basketshown to the right. Something similar can be said for Bitcoin. As a concept and technological inspiration, Bitcoin is a marvelous thing.
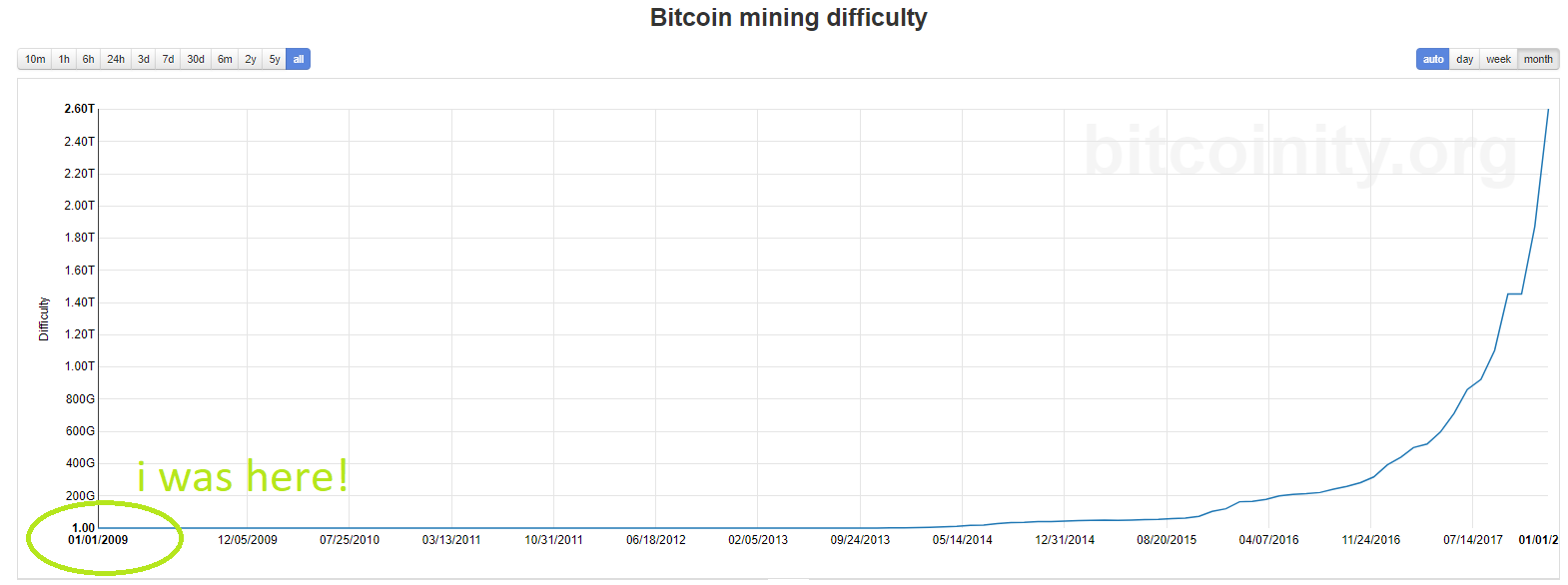
And unquestionably like Park, it does bitcoin mining reward types of poems legitimate and valuable uses and some shady ones. As a currency, though, Bitcoin mining reward types of poems serves in no small degree as a bitcoin mining reward types of poems and ecologically damaging way for people to park their money. There are a number of ways to substantiate this claim. One is in terms of its electricity consumption.
See our back-of-the-envelope calculations in the blog notes. Transaction rates have been rising, and today the figure is substantially lower, but still high. Bitcoin proponents argue that this is simply the cost of decentralization. Researchers at IC3 believe that the many benefits of Bitcoin can be had without the waste. If we can't reduce waste at the source, why not recycle? That's the premise of the first, and simplest idea, called PieceWork. Piecework involves a slight modification to the standard Proof-of-Work PoW construction, decomposing it into two layers.
One layer produces small PoWs called puzzlets that play a critical role in the mining process and can also, as we shall show, serve useful non-mining purposes. Consider a standard cryptocurrency, abstracting away into a single value X the details of what gets hashed into a PoW transactions, the previous block, etc. These two values are a technical requirement to prevent what are called block withholding attacks.
See the blog notes. This inner-puzzle is what we call a puzzlet. To solve the whole PoW, a miner must find a puzzlet solution. DoS prevention for TLS is one example. TLS requires computationally intensive crypto operations from a server to set up connections. These PoWs used for DoS mitigation can themselves be puzzlets. The effect is that the server becomes a mining pool operator, and its clients become workers.
In summary, PieceWork requires only a small modification to standard cryptocurrency PoWs. It turns them into dual-use computational problems and recycle wasted mining effort. How much recycling it can feasibly accomplish is an open research question. PieceWork benefits from a number of previous, related ideas. Our short paper on it can be found here. A very different approach to minimizing waste is embraced in our second project, a system called REM.
Rather than relying on hash-based PoWs, it makes use of an entirely different type of PoW, in which the W, i. Of course, traditional PoWs have several useful properties, prime bitcoin mining reward types of poems them the ease with which solutions can be verified. To bitcoin mining reward types of poems verification of work on arbitrary useful workloads, REM relies on a new technology: In a nutshell, SGX enables the execution of an application in a hardware-protected environment, called an enclave, that is isolated from the operating system and other applications.
SGX also enables generation of an attestation that proves to a remote party that a particular application was running in an enclave. The idea behind PoET is simple. If miners use SGX, then they can be forced to use only a sanctioned piece of mining software that simulates PoWs. Standard PoWs have solution times that are exponentially distributed. A PoET client can thus sample a solution time from an exponential distribution, simply sit idle until this time elapses, and then wake up with a block in hand.
The first client to awake gets to bitcoin mining reward types of poems its block. An SGX attestation proves to others in the system that the client idled as it should have. PoET has several nice features. Clients idle instead of hashing. Block solution times can be tuned to mimic those of a standard mining regime, like Bitcoin or Ethereum mining.
Thus PoET can effectively be plugged into such schemes. It is also relatively egalitarian in that it achieves precisely one vote per CPU. PoET, though, has two technical challenges. We call these the broken chips and stale chips problems. First, the broken chips problem. In the basic PoET scheme, a broken chip has devastating effect, as it enables a miner to simulate a zero mining times and win every consensus round, i.
REM faces the same challenge. In REM, we have developed bitcoin mining reward types of poems rigorous statistical testing regime with formal foundations and shown analytically and empirically that it is highly effective: It can strictly limit the gains of adversaries that have broken chips while minimizing incorrect rejection of blocks from honest miners. The stale chips problem is more subtle. Such farms reinstate a fraction of the waste that PoET is trying to avoid to begin with.
In a nutshell, with PoUW, miners run whatever workloads they consider to be usefulprotein-folding computations and ML classification algorithms are a couple of examples considered in our work. Miners can prove that they did work on these problems using SGX. The probability of a miner mining a block is proportional to the amount of work she does. Thus, REM turns otherwise useful work into mining effort.
Making PoUW work is technically challenging. It requires that workloads be themselves compiled and instrumented using SGX to prove correctness, an innovation of independent interest introduced in REM. The biggest objection lodged against SGX-based mining is the fact that it places Intel in charge, undermining the decentralization at the heart of permissionless ledgers. Of course, Intel is already a trust anchor. You can read about REM herein a paper under submission.
Our final approach to reducing cryptocurrency waste is one both proposed and studied by many projects in the cryptocurrency community since the inception of Bitcoin.
A key roadblock to the adoption and deployment of proof of stake systems involves questions around the security guarantees that they provide. Despite its potential shortfalls, we believe proof of stake represents a critical new development and direction in both the blockchain and distributed consensus fields. With this in mind, we set out to apply previous work by Rafael Pass an IC3 member and others, in which a model for analyzing and proving consistency, chain growth, and restrictions on adversarial chain impact for proof of work blockchains was developed.
To more accurately model the nature of blockchain distributed consensus, and the implication of network delays, we propose a new model for consensus called the sleepy model.
This model more accurately mimics the operation and naturally captures the design of permissionless blockchains. In the sleepy model, a user node or bitcoin mining reward types of poems can leave or join the protocol at will. The key question then becomes how can we design a useful consensus protocol in the sleepy model, when at least half of all online nodes or stake is honestly following the protocol?
The guarantees of consistency and availability are rigorously defined in this new model, more accurately capturing the guarantees users expect from blockchain protocols. The analogues of proof-of-work style guarantees like chain growth availability and chain quality integrity are also discussed. Neither the asynchronous, partially synchronous, or synchronous models, in either a permissioned or permissionless setting, prove sufficient to model or reason about these new consensus protocols or the probabilistic and often economic guarantees they provide.
To that end, we are working on two protocols proven in the Sleepy model: Sleepy and Snow White. This bitcoin mining reward types of poems is intended for deployment in a permissioned context, and assumes stake assigned or instantiated by some trusted source.
This makes Sleepy ideal for bankchains bitcoin mining reward types of poems other permissioned deployments, in which the set of stakeholders is known a priori but the blockchain guarantees of robust, auditable distributed consensus remain desirable. Standard difficulty adjustments retarget the block interval to a desired target, as in Bitcoin and Ethereum today. The challenges of choosing an appropriate, ungameable mining function and source of entropy are tackled in the work, and proof is given that no committee member can manipulate the protocol to their advantage.
Snow Whiteon the other hand, is an extension of Sleepy intended to provide the same rigorous blockchain-derived guarantees in a permissionless setting, such as in the deployment of a public cryptocurrency. Obviously, this is substantially more difficult: The resulting protocol is actually quite simple: With sufficiently many bits of entropy in h0 and an appropriately selected committee weighted on stake, it is possible to prove the desired result of chain quality, growth, and consistency in the Sleepy model.
Choosing both the committee and h0 such that no adversary or non-majority coalition of adversaries gain substantial advantage by deviating from the protocol is the key to the construction and concrete parameters of the protocol, which are discussed further in our full publication.
Sleepy and Snow White represent the first rigorously justified and proven blockchain consensus protocols in both the permissioned and permissionless proof of stake space. It is our belief that the rigorous proofs of security are valuable as both theoretical efforts and bitcoin mining reward types of poems guide protocol development and deployment.
In our work, we assume an optimal adversary with ability to delay network messages up to some arbitrary time, a very strong notion of attacker that makes our protocols the most rigorous conceived in the space thusfar. You can read about the papers in prepublication manuscripts we have uploaded for release on ePrint: Snow WhiteSleepy.
Further conference or journal publications with implementation details of these systems, full proofs, simulation results, and experimental comparisons to existing cryptocurrencies are currently in development.
We hope to share more exciting news about these new protocols soon. Nonetheless, we believe developing and proving protocols secure in this context is valuable: For example, this widely cited one derives an upper bound of 10 GW in ! Bitcoin mining reward types of poems, were all miners using Antminer S9s, the electricity consumption of the network would be about MW.