MODERATORS
5 stars based on
65 reviews
Only top voted, non community-wiki answers of a minimum length are eligible. Questions Tags Users Badges Unanswered. Tag Info users hot new synonyms. Hot answers tagged sha day week month year all. How do you perform double-SHA encoding? You're hashing the hexadecimal representation of the first hash.
You need to hash the actual hash -- the binary data that the hex represents. Why are Bitcoin addresses hashes of public keys? It's just to get shorter addresses.
Regular public keys are 65 bytes long, which is much too long to be convenient. Compressed public keys are 33 bytes and could potentially be used instead of hashes, though these are a little longer than byte hashes. It also seems likely that Satoshi didn't know about compressed public keys or wasn't comfortable with What you bitcoin mining sha 256 digestion requesting is described as computing the Wallet Import Format for that private key: Add a 0x80 byte in front of it Another way to look at it is to take a look at a recent block that was mined, for example, block Looking at this block on blockchain.
Why are hashes in the bitcoin protocol typically computed twice double computed? The wiki answers this. Claudiu 2 8. We don't know for sure, but the most popular theory is that a double hash was chosen to protect against length extension attacks. Is bitcoin mining bitcoin mining sha 256 digestion compromising the security of SHA With a look up table you can avoid calculating the hash of a given input twice.
Indeed, the block chain can be considered as a giant look up table, but one with very special forms of inputs: It links bitcoin mining sha 256 digestion and transactions to their hashes.
Though, why should someone choose a transaction or block as her password? Further, why would an attacker even try to Did Satoshi intend to allow midstate computation to speed up hashing? I think Satoshi was not aware that the hashing routine could be optimized by the use of a midstate when he first created bitcoin. If you look here, you can see that the first version of bitcoin that had the midstate optimization built into the miner was version 0.
I got linked this question. I bitcoin mining sha 256 digestion a tool which includes a component that allows one to simulate mining: But it can give you some pointers.
It'll construct a block on JornC 1 3. How to generate a Bitcoin Private Bitcoin mining sha 256 digestion Checksum. F29E are indeed the first four bytes of the double sha of the bytes: However, as already discussed, passing the string CF Sven Williamson 1, 3 How many hashes create one Bitcoin?
These charts show the approximate network hash rate on the left axis: Together this provides enough info to give an approximate answer to your question: The wiki claim that this is to prevent birthday attacks is wrong. If you can successfully execute a birthday attack on a single call to the hash function, you get a successful birthday attack on the second call. If you really wanted to guard against this, you would do Is the SHA value in the bitcoin address wiki accurate?
The problem is that you're treating the pubkey as string data. What you need to do is treat it as raw binary hexadecimal. If you use fileformat. Not that other answers are wrong here, but just to approach your confusion from another angle: SHA hashing algorithm, which produces alphanumeric hashes.
The hashing algorithm produces a stream of bytes. Only when you display that bunch of bytes on your screen it's common for it to be in hexadecimal containing "alphanumeric" Jannes 5, 13 Whilst you are correct that what people are doing is a massively parallel search for double-SHA hash collisions to hash outputs near zero, you can only take advantage of the result if you actually find a collision.
So how often can we get a collision? You want to work with the digests, not the hex strings. Colin Dean 5, 3 16 Good hashes have 4 properties: Does every nonce really have an equal chance of winning? It's not unevenly distributed. The reason it bitcoin mining sha 256 digestion that way in the graphs above is because the x-axis is plotted in logarithmic units.
Here's what it looks like in linear units:. Geremia 2, 1 19 Is there a guaranteed hash for every block? There's no guarantee that you can solve a block just by adjusting the nonce. But there are other things you can change in a block that also change the hash. This question is pretty much an exact duplicate of your question. What values are hashed in the SHA algorithm, and what would be the next iteration until a possible header is found?
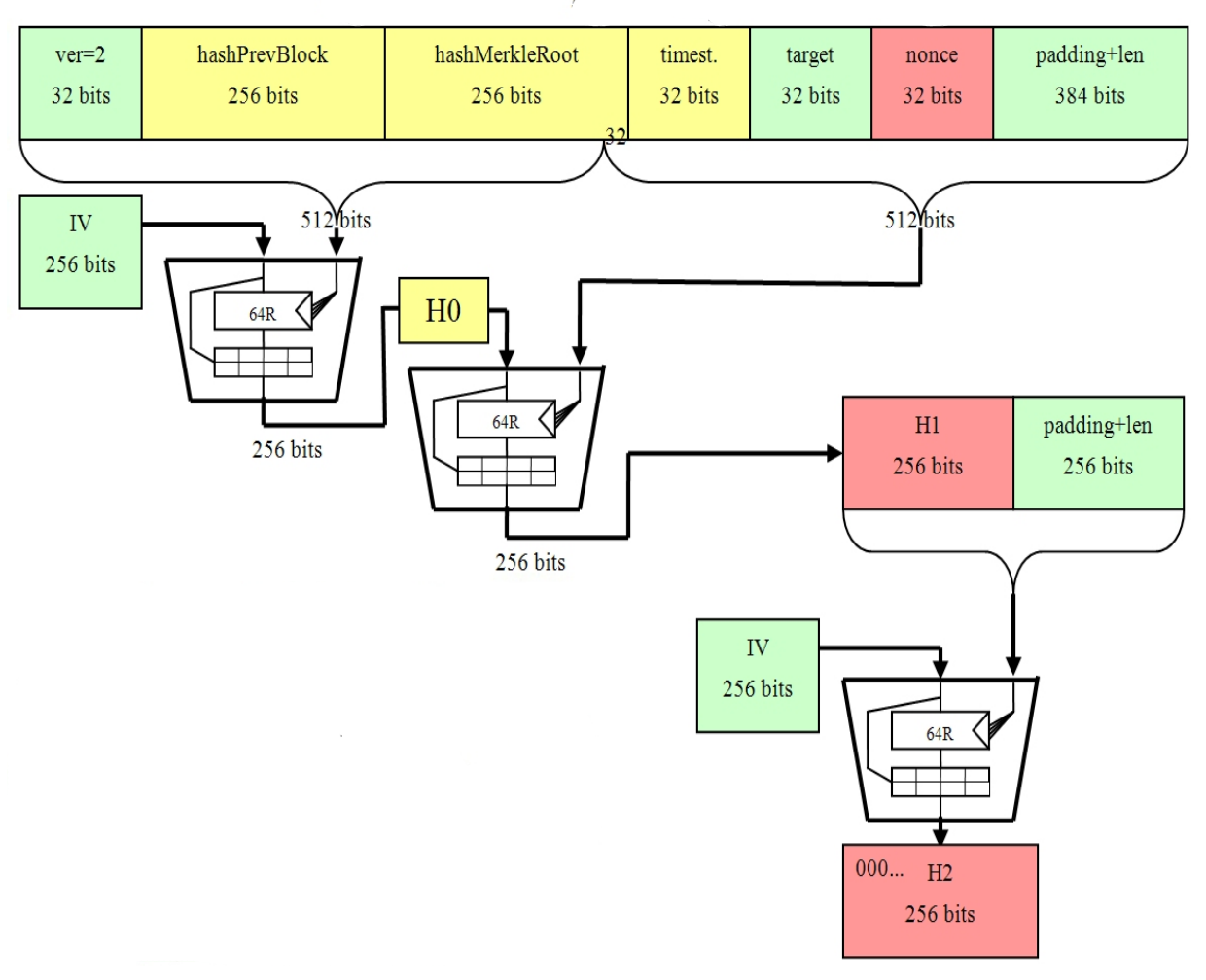
When the nonce range is exhausted, miners change the extraNonce field of the generation transaction. This changes the Bitcoin mining sha 256 digestion root in the header and allows a new range of nonces to be attempted. Since the Merkle root is bits, this bitcoin mining sha 256 digestion be repeated indefinitely.
All block bitcoin mining sha 256 digestion start with a certain number of zeroes by design. The nature of a hash is that knowing something about the output does not help you figure out what the input is supposed to be at least in theory.
So in short, no. NReilingh 2 7. You could easy manipulate a pool to wreck havoc on other SHA coins if you owned it or managed to gain access. You don't even need bitcoin mining sha 256 digestion be a large pool, some altcoins are really small and vulnerable. It has affected other coins before, bitcoin mining sha 256 digestion a pool or a large miner created trouble solely by mining a smaller altcoin.
Feathercoin hit by massive attack Only John T 2, 8 Why don't any of the SHA vulnerabilities matter for mining? Also, what would be most useful for mining is a preimage attack, and those are much harder than collision attacks. You can see in the What is a midstate?
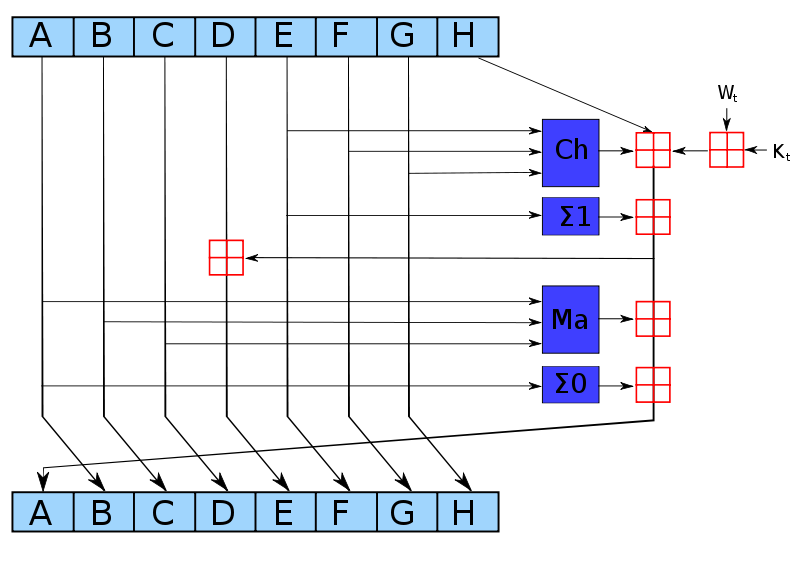
How does using a midstate speed up hashing? People often talk about SHA like it's a single operation, but it isn't. Rather, the input is broken up into byte chunks, and then each chunk is put into a compression function. The state of the hash partway through hashing something does not depend on future parts of the data.
Since the nonce is found in the second chunk, changing the nonce doesn't The hash is not alphanumeric, it's hexadecimal, that is base You can convert that to a decimal number. Jimmy Song 6, 8 How to compute double sha shown in examples of bip ? Where can I see an input that will hash to a solution? Ordering the bytes that make up a block so that you can hash them seems to be fairly complex, but if all you're looking for is an arbitrary string that hashes to something beginning with a few zeroes, you can search using a simple shell command: Bitcoin Stack Exchange works best with JavaScript enabled.