Metcalfe39s law bitcoin chart
50 comments
Bezmaksas bitcoin wallet adreses
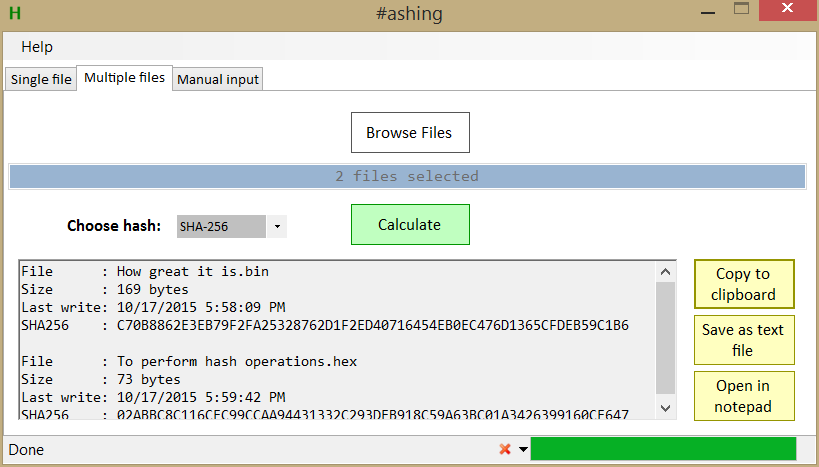
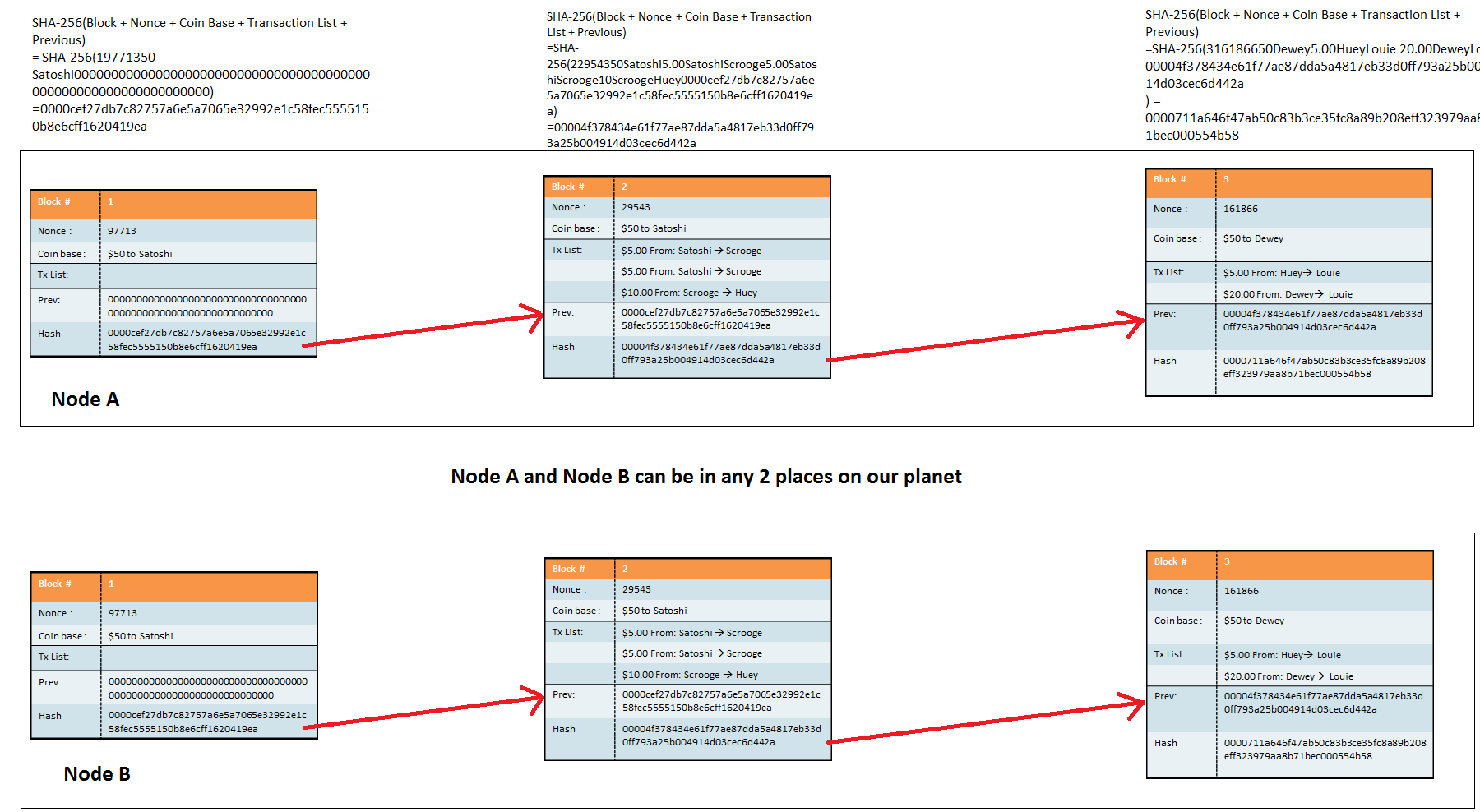
SHA generates an almost-unique bit byte signature for a text. See below for the source code. Such applications include hash tables, integrity verification, challenge handshake authentication, digital signatures, etc. Note that hash functions are not appropriate for storing encrypted passwords, as they are designed to be fast to compute, and hence would be candidates for brute-force attacks. The bit key makes it a good partner-function for AES. NIST also provide a number of test vectors to verify correctness of implementation.
There is a good description at Wikipedia. In this JavaScript implementation , I have tried to make the script as clear and concise as possible, and equally as close as possible to the NIST specification, to make the operation of the script readily understandable.
This script is oriented toward hashing text messages rather than binary data. The standard considers hashing byte-stream or bit-stream messages only. Text which contains multi-byte characters outside ISO i. Note that what is returned is the textual hexadecimal representation of the binary hash. This can be useful for instance for storing hashed passwords, but if you want to use the hash as a key to an encryption routine, for example, you will want to use the binary value not this textual representation.
Using Chrome on a low-to-middling Core i5 PC, in timing tests this script will hash a short message in around 0. Note that these scripts are intended to assist in studying the algorithms, not for production use. See below for the source code of the JavaScript implementation, also available on GitHub.
With its untyped C-style syntax, JavaScript reads remarkably close to pseudo-code: These functions should be simple to translate into other languages if required, though can also be used as-is in browsers and Node. I offer these scripts for free use and adaptation to balance my debt to the open-source info-verse. You are welcome to re-use these scripts [under an MIT licence, without any warranty express or implied] provided solely that you retain my copyright notice and a link to this page.
If you would like to show your appreciation and support continued development of these scripts, I would most gratefully accept donations. If you have any queries or find any problems, contact me at ku.