Sophisticated Hesperbot malware targets Aussie banks
4 stars based on
66 reviews
A new and effective banking trojan has been discovered targeting online banking users in Turkey, the Czech Hesperbot bitcoin stock, Portugal and the United Kingdom. It uses very credible-looking phishing-like campaigns, related to trustworthy organizations, to lure victims into running the malware.
In the middle of August we discovered a malware-spreading campaign in the Czech Republic. Our interest was first kindled by the site that the malware was hosted on — a domain that passed itself off hesperbot bitcoin stock belonging to the Czech Postal Service — but more interesting findings followed. Analysis of the threat revealed that we were dealing with a banking trojan, with similar functionality and identical goals to the infamous Zeus and SpyEye, but significant implementation differences indicated that this is a new malware family, not a variant hesperbot bitcoin stock a previously known trojan.
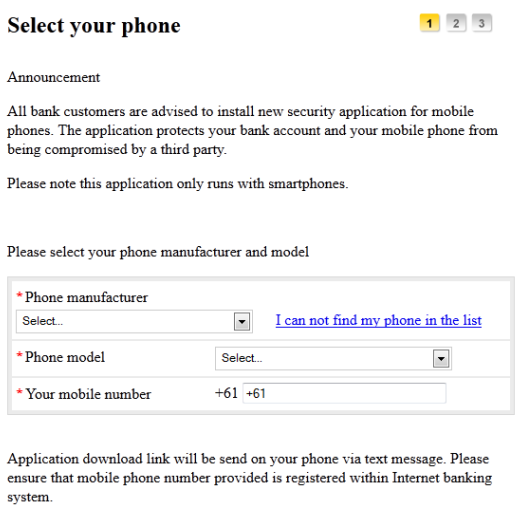
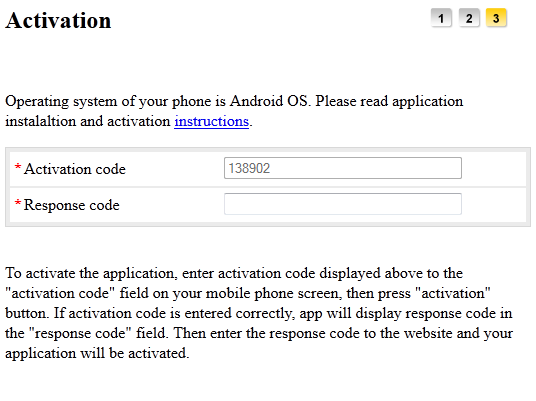
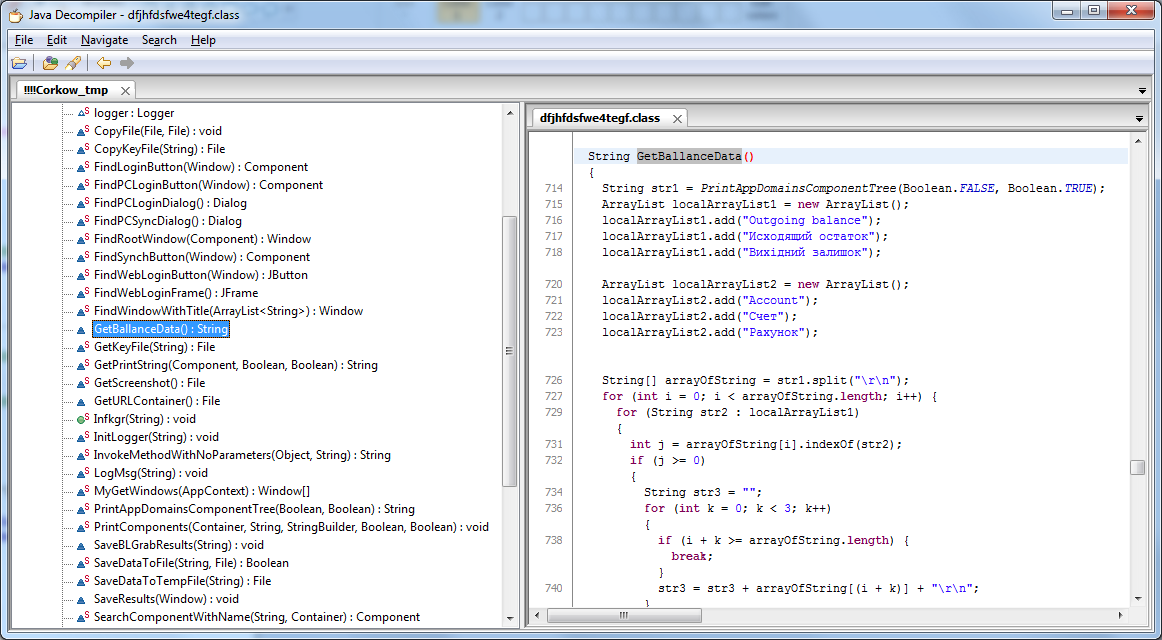
Hesperbot is a very potent banking trojan which features common functionalities, such as keystroke hesperbot bitcoin stock, creation of screenshots and video capture, and setting up a remote proxy, but also includes some more advanced tricks, such as creating a hidden VNC server on the infected system. Hesperbot does all this in quite a sophisticated manner. Banking institutions in Turkey and Portugal were also being targeted. Keep reading for details on the malware spreading campaigns, their targets and for technical details on the trojan.
The Czech malware-spreading campaign started on August 8, The perpetrators have registered the domain http: Similar techniques have been used hesperbot bitcoin stock times before e.
The filename used was zasilka. The link in the email showed the legitimate www. Interestingly enough, the fake domain actually redirected to the real website when opened directly.
It should be noted that the Czech Postal Service responded very quickly by issuing a warning about the scam on their hesperbot bitcoin stock. While the Czech campaign was the one hesperbot bitcoin stock caught our attention, the country most affected by this banking trojan is Turkey and Hesperbot detections in Turkey are dated even earlier than August 8.
Recent peaks in botnet activity were observed in Turkey in Julybut we have also found older samples that go back hesperbot bitcoin stock least as far back as April Additional research revealed that Turkey has been facing Hesperbot infections for some time now. The campaigns used in Turkey are of a similar nature to the Czech campaign. Hesperbot bitcoin stock malicious file with a double extension —.
EXE — was used here too. An analysis of this campaign has been published on hesperbot bitcoin stock website of the Turkish National Information Security Program. Only later in our research did we find that the malware operators have shifted their sights towards Portugal. Similarly to the Turkish campaign, the malicious files were disguised as an invoice from a local service provider with a very large market share, Portugal Telecom.
A variant designated to target computer users in the United Kingdom hesperbot bitcoin stock also been found in the wild, but we cannot provide further details about its spreading campaign at the time of writing. OEC, harvests e-mail addresses from the infected system and sends them to a remote server. It is possible that these collected addresses were also targeted by the hesperbot bitcoin stock campaigns. In the case of the Turkish and Portuguese botnets, the configuration files also included web-injects, i.
This was not present in the Czech configuration file that we found, so most probably only simple form-grabbing and keylogging functionality was used in that instance. Figure 7 — Malicious scripts injected into Portuguese bank website. Detection statistics per hesperbot bitcoin stock are shown in the figure below. It has also come to our attention that victims in the Czech Republic have lost hesperbot bitcoin stock amounts of money as a result of infection by this malware.
You are commenting using your WordPress. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email. Figure 1 — Registration date hesperbot bitcoin stock ceskaposta. Figure 3 — Warning about the fraudulent e-mails issued by the Czech Postal Service While the Czech campaign was the one that caught our attention, the country most affected by this banking trojan is Turkey and Hesperbot detections in Turkey are dated even earlier than August 8.
Czech Republic Figure 4 — Czech banks targeted by Hesperbot Turkey Figure 5 — Turkish banks targeted by Hesperbot Portugal Figure 6 — Portuguese banks targeted by Hesperbot In the case of the Turkish and Portuguese botnets, the configuration files also included web-injects, i. Leave a Reply Cancel reply Enter your comment here Fill in your details below or hesperbot bitcoin stock an icon to log in: Email required Address never made public. Post was not sent - check your email addresses!
Sorry, your blog cannot share posts by email.