Geth ethereum download
31 comments
Dogecoin rpc api
To continue reading this article, please exit incognito mode or log in. Visitors are allowed 3 free articles per month without a subscription , and private browsing prevents us from counting how many stories you've read. We hope you understand, and consider subscribing for unlimited online access. An increasing number of online merchants now offer the ability to pay using the cryptocurrency Bitcoin. One of the great promises of this technology is anonymity: This is handy for some, but the anonymity is by no means perfect.
Security experts call it pseudonymous privacy, like writing books under a nom de plume. You can preserve your privacy as long as the pseudonym is not linked to you. But as soon as somebody makes the link to one of your anonymous books, the ruse is revealed.
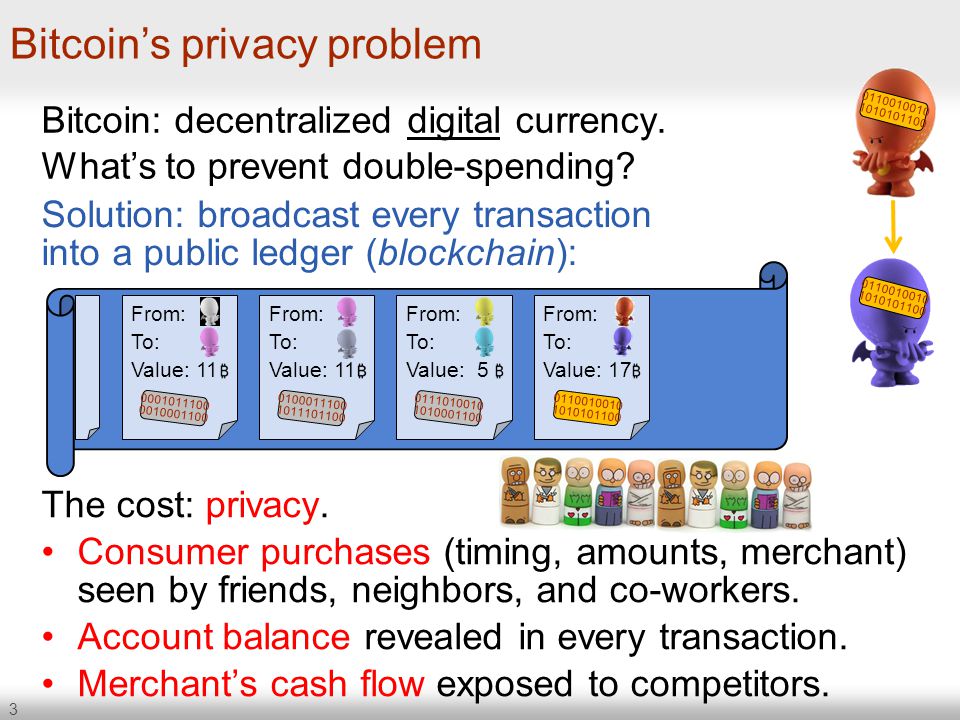
Your entire writing history under your pseudonym becomes public. Similarly, as soon as your personal details are linked to your Bitcoin address, your purchase history is revealed too. That raises an important question for people hoping to use Bitcoin to make anonymous purchases: Today we get an answer thanks to the work of Steven Goldfeder at Princeton University and a number of pals.
These guys say the way information leaks during ordinary purchases makes it straightforward to link individuals with the Bitcoin transactions they make, even when purchasers use additional privacy protections, such as CoinJoin.
The main culprits are Web trackers and cookies—small pieces of code deliberately embedded into websites that send information to third parties about the way people use the site. Common Web trackers send information to Google, Facebook, and others to track page usage, purchase amounts, browsing habits, and so on. Some trackers even send personally identifiable information such as your name, address, and e-mail. The question that Goldfeder and co investigate is how easy it is to use this information to connect people to their Bitcoin transactions.
The team began by listing major merchants that allow Bitcoin transactions. They came up with of them, including Microsoft, NewEgg, and Overstock. They then studied how Web trackers leak information from each of these sites during the purchase process. Most of this information leakage is intentional for the purposes of advertising and analytics.
But the researchers also say some extra information is also sent. But even when the exact transaction is kept hidden, it is still possible to make the link when the leak includes the amount and time of the purchase. In that case, the eavesdropper needs to convert the purchase amount into Bitcoins using the exchange rate at the time and then search the blockchain for a transaction of that amount at that moment. This reveals the Bitcoin address of the user. Any other purchases made using that address are then trivial to track down.
There are a couple of additional factors that make this process trickier. The Web tracker might leak the cost of the product but not include shipping, so the total Bitcoin purchase may not be clear. There may also be a gap between the time the user viewed the page the information leaked from—the checkout cart, for example—and the time when the purchase was actually made.
Bitcoin purchases are time-stamped, so it becomes harder to track them down if the time is not known accurately. The purchase amount is usually given in a local currency such as dollars or pounds and then converted into Bitcoin at the instant of purchase.
Because of the large variability in Bitcoin exchange rates, it can be hard to work out the exact Bitcoin value if the purchase time is not known accurately. All these factors make it harder to link individuals to their Bitcoin transactions, but it is by no means impossible. There are ways to further hide Bitcoin transactions. This mixes their bitcoins, making it harder to identify them.
But Goldfeder and co point out that if an individual uses CoinJoin to make several purchases in this way, it is straightforward to link them back: These are useful but can sometimes miss trackers and at other times prevent purchases entirely.
But it will also be music to the ears of law enforcement agencies hoping to track nefarious activities. When the Cookie Meets the Blockchain: Privacy Risks of Web Payments via Cryptocurrencies. Catch up with our coverage of the event. A new prototype gets at how—and why—manufacturers and product designers might benefit from a blockchain.
Unlimited online access including articles and video, plus The Download with the top tech stories delivered daily to your inbox. Unlimited online access including all articles, multimedia, and more. The Download newsletter with top tech stories delivered daily to your inbox.
Revert to standard pricing. Hello, We noticed you're browsing in private or incognito mode. Subscribe now for unlimited access to online articles. Why we made this change Visitors are allowed 3 free articles per month without a subscription , and private browsing prevents us from counting how many stories you've read.
And that can make it straightforward to link individuals with their Bitcoin purchases, say cybersecurity researchers. AI generates new Doom levels for humans to play. How can we be sure AI will behave? Perhaps by watching it argue with itself. A criminal gang used a swarm of drones to disrupt an FBI raid. Paying with Your Face: The Future of Work Meet the Innovators Under 35 The Best of the Physics arXiv week ending May 5, Meet the blockchain for building better widgets, cheaper and faster.
This article was written by a human the next one may not be. Want more award-winning journalism? Subscribe to Insider Online Only. Unlimited online access including all articles, multimedia, and more The Download newsletter with top tech stories delivered daily to your inbox.
You've read of three free articles this month. Subscribe now for unlimited online access. This is your last free article this month. You've read all your free articles this month. Log in for more, or subscribe now for unlimited online access. Log in for two more free articles, or subscribe now for unlimited online access.