Bitcoin forex robot
44 comments
Yobitnet freecoinsyobitnetdash dash exchange
Hashcash is a proof-of-work system used to limit email spam and denial-of-service attacks , and more recently has become known for its use in bitcoin and other cryptocurrencies as part of the mining algorithm. Hashcash is a proof-of-work algorithm that requires a selectable amount of work to compute, but the proof can be verified efficiently. For email uses, a textual encoding of a hashcash stamp is added to the header of an email to prove the sender has expended a modest amount of CPU time calculating the stamp prior to sending the email.
In other words, as the sender has taken a certain amount of time to generate the stamp and send the email, it is unlikely that they are a spammer. The receiver can, at negligible computational cost, verify that the stamp is valid. However, the only known way to find a header with the necessary properties is brute force , trying random values until the answer is found; though testing an individual string is easy, if satisfactory answers are rare enough it will require a substantial number of tries to find the answer.
The hypothesis is that spammers, whose business model relies on their ability to send large numbers of emails with very little cost per message, will cease to be profitable if there is even a small cost for each spam they send.
Receivers can verify whether a sender made such an investment and use the results to help filter email. The header line looks something like this: The header contains the recipient's email address, the date of the message, and information proving that the required computation has been performed.
The presence of the recipient's email address requires that a different header be computed for each recipient. The date allows the recipient to record headers received recently and to ensure that the header is unique to the email message. The sender prepares a header and appends a counter value initialized to a random number.
It then computes the bit SHA-1 hash of the header. If the first 20 bits i. If not, then the sender increments the counter and tries the hash again. Out of 2 possible hash values, there are 2 hash values that satisfy this criterion. Thus the chance of randomly selecting a header that will have 20 zeros as the beginning of the hash is 1 in 2 20 approx. The number of times that the sender needs to try to get a valid hash value is modeled by geometric distribution.
Hence the sender will on average have to try 2 20 values to find a valid header. Given reasonable estimates of the time needed to compute the hash, this would take about one second to find. At this time, no more efficient method is known to find a valid header. A normal user on a desktop PC would not be significantly inconvenienced by the processing time required to generate the Hashcash string.
However, spammers would suffer significantly due to the large number of spam messages sent by them. If the hash string passes all of these tests, it is considered a valid hash string. All of these tests take far less time and disk space than receiving the body content of the e-mail. The time needed to compute such a hash collision is exponential with the number of zero bits. So zero bits can be added doubling the amount of time needed to compute a hash with each additional zero bit until it is too expensive for spammers to generate valid header lines.
Confirming that the header is valid always takes the same amount of time, no matter how many zero bits are required for a valid header, since this requires only a single hashing operation. The Hashcash system has the advantage over micropayment proposals applying to legitimate email that no real money is involved.
Neither the sender nor recipient need to pay, thus the administrative issues involved with all micropayment systems are entirely avoided. On the other hand, as Hashcash requires potentially significant computational resources to be expended on each e-mail being sent, it is somewhat difficult to tune the ideal amount of average time one wishes clients to expend computing a valid header.
This can mean sacrificing accessibility from low-end embedded systems or else running the risk of hostile hosts not being challenged enough to provide an effective filter from spam.
Hashcash is also fairly simple to implement in mail user agents and spam filters. No central server is needed. Hashcash can be incrementally deployed—the extra Hashcash header is ignored when it is received by mail clients that do not understand it. One plausible analysis [4] concluded that only one of the following cases is likely: Examples of each include, respectively, a centralized e-mail topology like a mailing list , in which some server is to send an enormous amount of legitimate e-mails, and botnets or cluster farms with which spammers can increase their processing power enormously.
Most of these issues may be addressed. But they represent serious obstacles to hashcash deployment that remain to be addressed.
Another projected problem is that computers continue to get faster according to Moore's law. So the difficulty of the calculations required must be increased over time. However, developing countries can be expected to use older hardware, which means that they will find it increasingly difficult to participate in the email system. This also applies to lower-income individuals in developed countries who cannot afford the latest hardware.
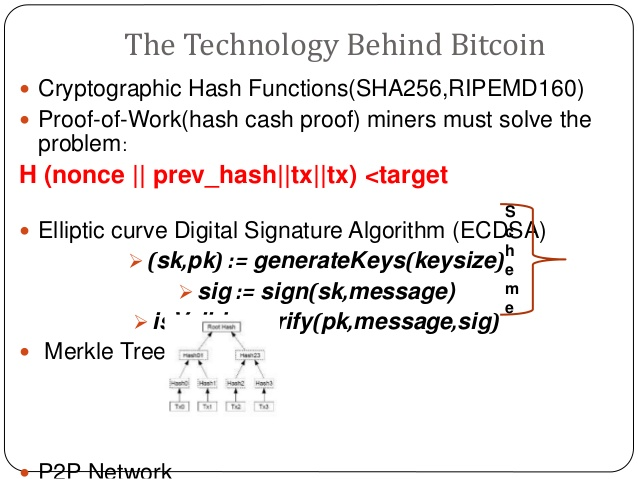
Like hashcash, cryptocurrencies use a hash function as their proof-of-work system. The rise of cryptocurrency has created a demand for ASIC -based mining machines. Although most cryptocurrencies use the SHA hash function, the same ASIC technology could be used to create hashcash solvers that are three orders of magnitude faster than a consumer CPU, reducing the computational hurdle for spammers.
In contrast to hashcash in mail applications that relies on recipients to set manually an amount of work intended to deter malicious senders, the Bitcoin cryptocurrency network employs a different hashing-based proof-of-work challenge to enable competitive bitcoin mining.
A bitcoin miner runs a computer program that collects unconfirmed transactions from coin dealers in the network.
With other data these can form a block and earn a payment to the miner, but a block is accepted by the network only when the miner discovers by trial and error a "nonce" number that when included in the block yields a hash with a sufficient number of leading zero bits to meet the network's difficulty target.
Blocks accepted from miners form the bitcoin blockchain that is a growing ledger of every bitcoin transaction since the coin's first creation. While hashcash uses the SHA-1 hash and requires the first 20 of hash bits to be zero, bitcoin's proof of work uses two successive SHA hashes and originally required at least the first 32 of hash bits to be zero.
However the bitcoin network periodically resets the difficulty level to keep the average rate of block creation at 6 per hour. As of August block the bitcoin network has responded to deployments of ever faster hashing hardware by miners by hardening the requirement to first 72 of hash bits must be zero.
Hashcash is used as a potential solution for false positives with automated spam filtering systems, as legitimate users will rarely be inconvenienced by the extra time it takes to mine a stamp. However, although the hashcash plugin is notionally on by default, it still needs to be configured with a list of address patterns that must match against the Hashcash resource field, so it doesn't actually work by default.
The format differences between Hashcash and Microsoft's email postmark is that postmark hashes the body in addition to the recipient, and uses a modified SHA-1 as the hash function and uses multiple sub-puzzles to reduce proof of work variance. Like e-mail, blogs often fall victim to comment spam.
Some blog owners have used hashcash scripts written in the JavaScript language to slow down comment spammers. Hashcash is not patented, and the reference implementation [12] and most of the other implementations are free software. Hashcash is included or available for many Linux distributions. The RFC included hashcash in the title and referenced hashcash, but the mechanism described in it is a known-solution interactive challenge which is more akin to Client-Puzzles; hashcash is non-interactive and therefore does not have a known solution.
In any case RSA's IPR statement can not apply to hashcash because hashcash predates [2] March the client-puzzles publication [15] Feb and the client-puzzles patent filing US [16] February From Wikipedia, the free encyclopedia. This section needs additional citations for verification. Please help improve this article by adding citations to reliable sources.
Unsourced material may be challenged and removed. August Learn how and when to remove this template message. Retrieved 31 August Retrieved 13 October What do you mean by Postage Stamp? Archived from the original PDF on Retrieved from " https: Cryptographic protocols Spam filtering Email authentication. Webarchive template wayback links Articles needing additional references from August All articles needing additional references All articles with unsourced statements Articles with unsourced statements from September Views Read Edit View history.
This page was last edited on 27 April , at By using this site, you agree to the Terms of Use and Privacy Policy.