How to know if you have 32 bit or 64 bit microsoft office 2007
27 comments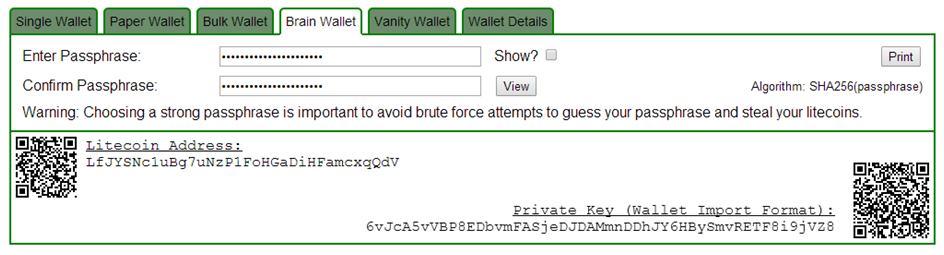
Bitcoin trading bot telegram
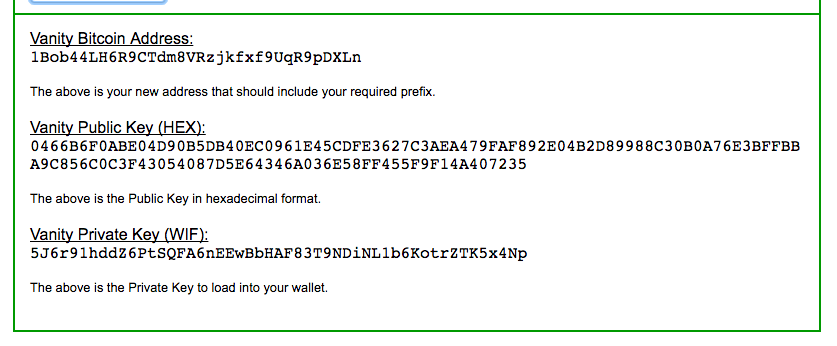
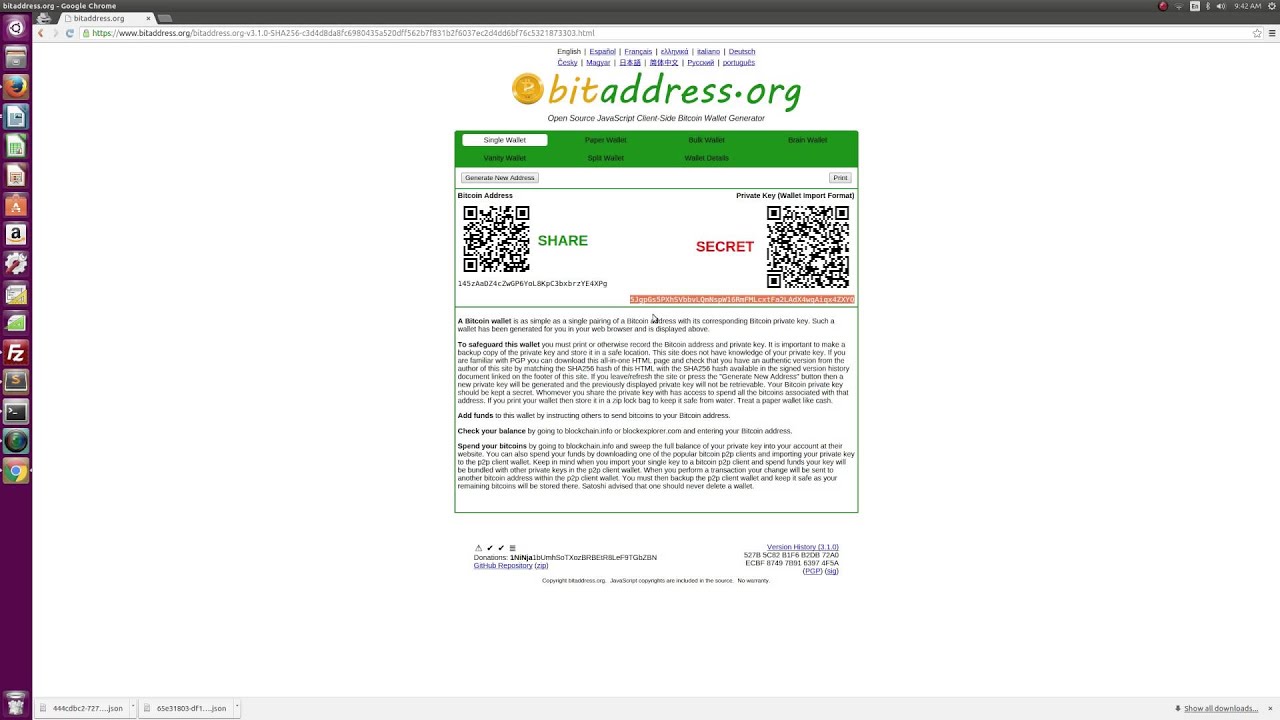
A cryptocurrency wallet stores the public and private keys which can be used to receive or spend the cryptocurrency. A wallet can contain multiple public and private key pairs. In case of bitcoin and cryptocurrencies derived from it, the cryptocurrency is decentrally stored and maintained in a publicly available ledger. With the private key, it is possible to write in the public ledger, effectively spending the associated cryptocurrency.
When choosing a wallet, the owner must keep in mind who is supposed to have access to a copy of the private keys and thus has potentially access to the cryptocurrency. Just like with a bank , the user needs to trust the provider to keep the cryptocurrency safe. Trust was misplaced in the case of the Mt.
Gox exchange, who 'lost' most of their clients' bitcoins. Downloading a cryptocurrency wallet from a wallet provider to a computer or phone does not automatically mean that the owner is the only one who has a copy of the private keys. For example with Coinbase , it is possible to install a wallet on a phone and to also have access to the same wallet through their website. A wallet can also have known or unknown vulnerabilities.
The sending party only needs to know the destination address. Anyone can send cryptocurrency to an address. Only the one who has the private key of the corresponding address can use it. When the private keys and the backup are lost then that cryptocurrency is lost forever. When using a webwallet, the private keys are managed by the provider.
When owning cryptocurrency, those trusted with managing the private keys should be carefully selected. An encrypted copy of the wallet should be kept in a trusted place. In order to initiate or verify a transaction, the cryptocurrency wallet connects to a client or node on the network to process the request. There are several types of clients like: Some of them can process transactions and some of them also have their own wallet functionality. When the user of a hardware wallet requests a payment, the wallet's API creates the transaction.
Then the wallet's hardware signs the transaction and provides a public key, which is sent to the network by the API. That way, the signing keys never leave the hardware wallet. If a hardware wallet uses a mnemonic sentence for backup, then the users should not electronically store the mnemonic sentence, but write it down and store in a separate physical location.
Storing the backup electronically lowers the security level to a software wallet level. Hardware wallets like LedgerWallet and Trezor have models that require the user to physically press or touch the wallet in order to sign a transaction, the destination address and the amount of coins. The private keys remain safe inside the hardware wallet. Without the private key a signed transaction cannot be altered successfully.
Some hardware wallets have a display see the picture where the user can enter a pin to open the wallet and where the transaction can be verified before being signed. When reading a mnemonic sentence from the physical display of the hardware wallet a screencapture of an infected computer will not reveal the mnemonic sentence.
With a watch only wallet someone can keep track of all transactions. Only the address public key is needed. Thus the private key can be kept safe in another location. With a multisignature multisig wallet multiple users have to sign with their private key for a transaction out of that wallet public key address. With a brain wallet someone remembers the information to regenerate the private and public key pair s , like a mnemonic sentence. Terms also used in the context of cryptocurrency wallets are hot and cold wallets.
Hot wallets are connected to the internet while cold wallets are not. With a hot wallet cryptocurrency can be spent at any time. A cold wallet has to be 'connected' to the internet first. As long as something is connected to the internet, it is vulnerable to an attack. The short version is that software wallets where the device is turned on or the wallet software is running are considered hot wallets.
A not connected hardware wallet is considered a cold wallet. Deep cold storage is the process of storing cryptocurrencies in cold wallets that were never connected to the Internet or any kind of network. Additionally the private keys associated with this system are generated offline. The process gained main stream attention, when Regal RA DMCC [21] , the first cryptocurrency licensed company in the middle east took it a couple of steps further by storing the cold wallets in the Almas Tower vault below sea level along with the company's gold bullion and insured the cryptocurrencies for full value.
With a deterministic wallet a single key can be used to generate an entire tree of key pairs. This single key serves as the "root" of the tree. The generated mnemonic sentence or word seed is simply a more human-readable way of expressing the key used as the root, as it can be algorithmically converted into the root private key.
Those words, in that order, will always generate the exact same root key. A word phrase could consist of 24 words like: That single root key is not replacing all other private keys, but rather is being used to generate them. All the addresses still have different private keys, but they can all be restored by that single root key. The private keys to every address it has ever given out can be recalculated given the root key. That root key, in turn, can be recalculated by feeding in the word seed.
The mnemonic sentence is the backup of the wallet. If a wallet supports the same mnemonic sentence technique, then the backup can also be restored on a third party software or hardware wallet. A mnemonic sentence is considered secure. It creates a bit seed from any given mnemonic. The set of possible wallets is 2 Every passphrase leads to a valid wallet.
If the wallet was not previously used it will be empty. In a non-deterministic wallet, each key is randomly generated on its own accord, and they are not seeded from a common key. Therefore, any backups of the wallet must store each and every single private key used as an address, as well as a buffer of or so future keys that may have already been given out as addresses but not received payments yet.
From Wikipedia, the free encyclopedia. This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed. September Learn how and when to remove this template message. This section needs additional citations for verification.
January Learn how and when to remove this template message. Retrieved 14 September Programming the Open Blockchain. Een introductie in de blockchain". Retrieved 9 December Retrieved 23 February Retrieved 9 February Retrieved 5 December The Ultimate in Mobile Money". Retrieved from " https: Bitcoin Alternative currencies Cryptocurrencies.
CS1 Dutch-language sources nl Articles needing additional references from September All articles needing additional references All articles lacking reliable references Articles lacking reliable references from September Articles containing potentially dated statements from January All articles containing potentially dated statements All articles with failed verification Articles with failed verification from April Articles with failed verification from January Articles needing additional references from January Views Read Edit View history.
This page was last edited on 2 May , at By using this site, you agree to the Terms of Use and Privacy Policy.