400 kh s litecoin values
38 comments
What is the ethereum ice age
Like firemen getting paid to put out the fires they started, Jha and White would target organizations with DDoS attacks and then either extort them for money to call off the attacks, or try to sell those companies services they claimed could uniquely help fend off the attacks. As part of this scheme, victim devices were used to transmit high volumes of requests to view web addresses associated with affiliate advertising content.
The documents show that Norman helped Jha and White discover new, previously unknown vulnerabilities in IoT devices that could be used to beef up their Mirai botnet, which at its height grew to more than , hacked devices. The Mirai malware is responsible for coordinating some of the largest and most disruptive online attacks the Internet has ever witnessed.
The biggest and first to gain widespread media attention began on Sept. That September digital siege maxed out at Gbps, almost twice the size of the next-largest attack that Akamai — my DDoS mitigation provider at the time — had ever seen. The third week of September was a dark and stormy one for KrebsOnSecurity.
Damian Menscher , a Google security engineer with whom I worked very closely on the migration to Project Shield, spoke this week about the unique challenges involved in protecting a small site like this one from very large, sustained and constantly morphing attacks.
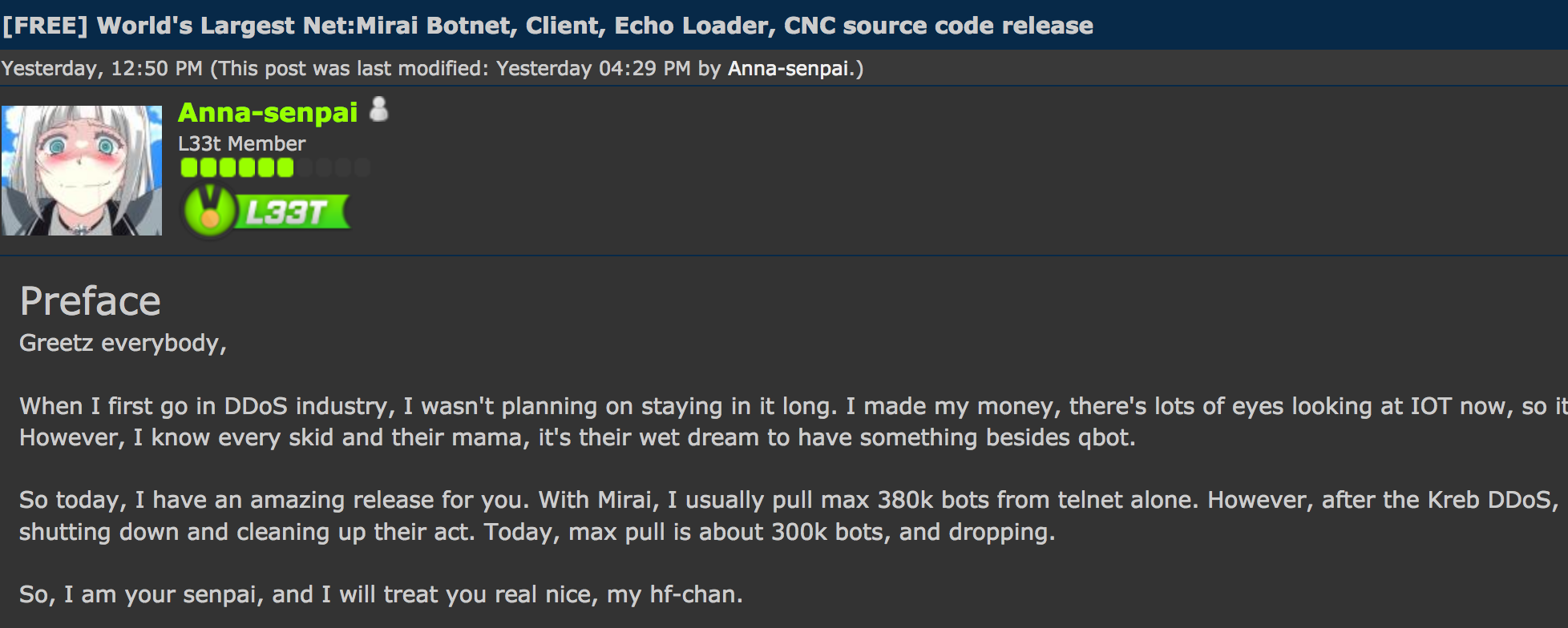
Addressing the Enigma security conference in Oakland, Calif. So we really had nothing to lose here. Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept.
The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross.
And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed. Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai.
And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras.
The most frequent target of the lelddos gang were Web servers used to host Minecraft , a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection. The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game — particularly pre-teen males. Microsoft has sold more than a million copies of Minecraft , and at any given time there are over a million people playing it online.
Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Robert Coelho is vice president of ProxyPipe, Inc. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.
In June , ProxyPipe was hit with a gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted. Verisign said the attack was launched by a botnet of more than , servers running on SuperMicro IPMI boards. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, , when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
I scanned the internet with a few sets of defualt logins The second time I heard from Sculti on Skype was Sept. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. So today, I have an amazing release for you. With Mirai, I usually pull max k bots from telnet alone. Today, max pull is about k bots, and dropping. Follow me on Twitter. Join me on Facebook. Krebs on Security In-depth security news and investigation. The Hackforums post that includes links to the Mirai source code.
Your email account may be worth far more than you imagine.