Unauthorized Coin Mining in the Browser
5 stars based on
57 reviews
Financially motivated threat actors will continue to use malware infections to deploy cryptocurrency mining software for as long as it remains profitable. Compared to complete loss of availability caused by ransomware and loss of confidentiality caused by banking trojans or other information stealers, the impact of unauthorized cryptocurrency mining on a host is often viewed as more of a nuisance.
However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. Furthermore, the deployment and persistence of unauthorized cryptocurrency mining software in an environment reflects a breakdown of effective technical controls. If activity of this nature can become established and spread laterally within the environment, then more immediately harmful threats such as ransomware could as well.
Bitcoin mining en el host web 2017 technical controls used to mitigate the delivery, persistence, and propagation of unauthorized cryptocurrency miners are also highly effective against other types of threat. Although Bitcoin was reportedly used to purchase goods for the first time in Bitcoin mining en el host web 2017serious discussions of its potential as an accepted form of currency began inwhich coincided with the emergence of other cryptocurrencies. There were approximately 1, cryptocurrencies as of December with new currencies added every day, although many cryptocurrencies cannot be mined.
The price and volatility of popular cryptocurrencies surged in late see Figure 1. Market price of various cryptocurrencies from January to March Miners receive cryptocurrency as a reward and as an incentive to increase the supply of miners.
Consequently, cryptocurrency mining can be profitable for as long as the reward bitcoin mining en el host web 2017 the hardware and energy costs. Aggregating computing power, and then splitting any rewards received among the contributors, is a more profitable way of mining cryptocurrency than individual efforts.
Pools are not required to disclose information about the number of active miners in their pool, making it difficult to estimate the number of active miners and mining applications. Cryptocurrency is attractive to financially motivated threat actors as a payment method and as a way to generate revenue through mining:.
Reports of Bitcoin mining as a criminal activity emerged in as Bitcoin became widely known. Between andthere were several notable developments in cryptocurrency mining malware:. Threat actors exploit any opportunity to generate revenue, and their activity can affect unknowing facilitators as well as the end victim. The impact to an individual host is the consumption of processing power; IR clients have noted surges in computing resources and effects on business-critical servers.
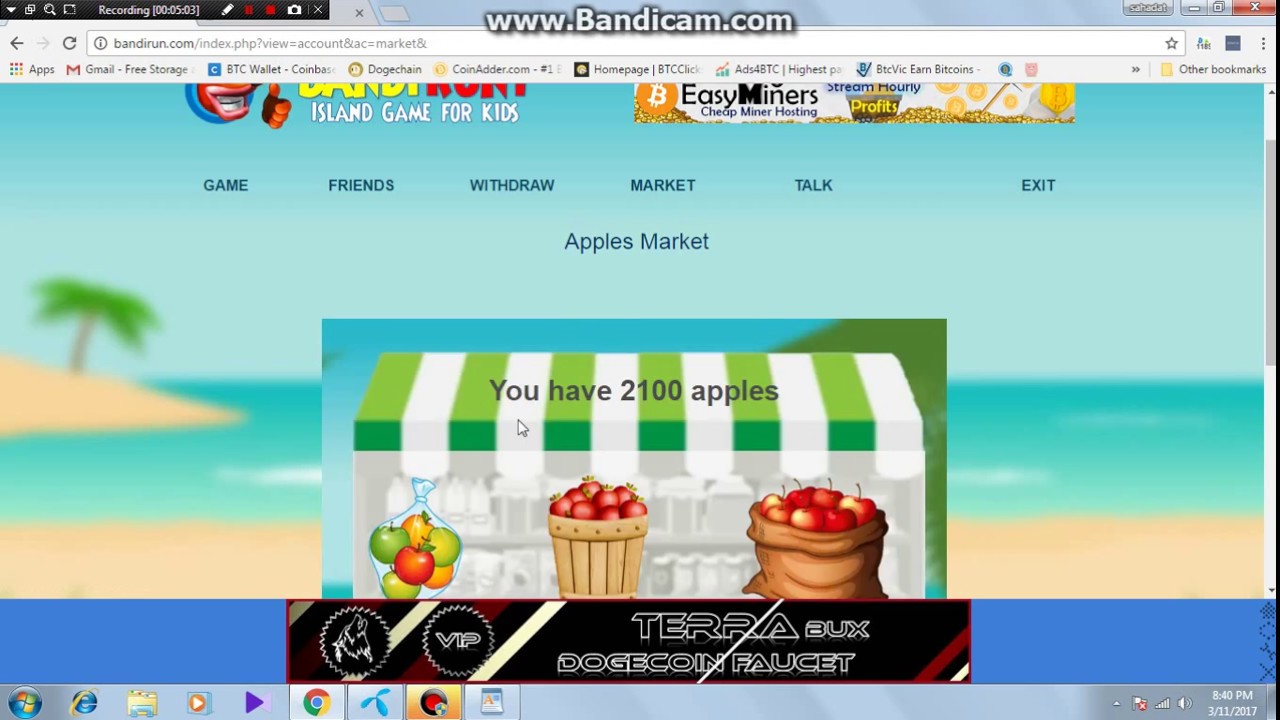
This impact is amplified in large-scale infections. XMRig cryptocurrency miner running as local service bitcoin mining en el host web 2017 an infected host. XMRig accepts several variables as inputs see Figure 4including the wallet, a username and password if required, and the number of threads to open on the system. Figure 5 illustrates the impact on an idling host when the miner uses four threads to consume spare computing capacity. Over time, this performance load forces the host to work harder, which also generates higher energy costs.
After gaining the ability to bitcoin mining en el host web 2017 software on a compromised system, a bitcoin mining en el host web 2017 actor chooses how to monetize the system. InCTU researchers reported that many bitcoin mining en el host web 2017 motivated threat actors had shifted to using ransomware rather than traditional banking trojans, which have higher costs in terms of malware development and maintaining money muling networks.
Cryptocurrencies facilitated the popularity of ransomware by making payment tracking and account disruption more difficult. However, there is a significant chance that victims will not pay the ransom, and that ransomware campaigns will receive law enforcement attention because the victim impact is immediate and highly visible.
In contrast, a victim may not notice cryptocurrency mining as quickly because it does not require capitulation, its impact is less immediate or visible, and miners do not render data and systems unavailable. These factors may make mining more profitable than deploying ransomware.
If the threat actor manages resource demands so that systems do not crash or become unusable, they can deploy miners alongside other threats such as banking trojans to create additional revenue. Threat actors could also decide to deploy ransomware after mining cryptocurrency on a compromised network for a final and higher value payment before shifting focus to a new target. Secureworks iSensor telemetry between and related to Bitcoin and the popular Stratum mining protocol indicates an increase in mining activity across Secureworks clients.
Intrusion detection system events are not a reliable indicator over time due to the addition of clients and better detections as network countermeasures evolve. There was a bitcoin mining en el host web 2017 acceleration around October Bitcoin price compared to iSensor detections for Bitcoin network traffic on Secureworks client networks between December and February Client telemetry shows a similar increase in CoinHive traffic since its launch in September While CoinHive activity is typically a legitimate, if sometimes controversial, form of revenue generation, organizations need to consider how to manage the impact to corporate systems.
Secureworks IR analysts often find cryptocurrency mining software during engagements, either as the primary cause of the incident or alongside other malicious artifacts.
Most identified cryptocurrency miners generate Monero, probably because threat actors believe it provides the best return on investment. Unlike Bitcoin, Monero makes mining more equitable for computers with less computational power, which is suitable for exploiting a large number of standard corporate computing assets. The techniques that Secureworks IR analysts have observed threat actors using to install and spread miners in affected environments align with common methods that CTU researchers have encountered in other types of intrusion activity.
Threat actors will use the most effective techniques to create a large network of infected hosts that mine cryptocurrency. Legitimate cryptocurrency miners are widely available. Underground forums offer obfuscation, malware builders, and botnet access to hide illegitimate mining see Figure 7. Forum advertisement for builder applications to create cryptocurrency mining malware.
Initial access and installation often leverage an existing malware infection that resulted from traditional techniques such as phishing. Secureworks IR analysts commonly identify mining malware alongside downloader scripts or other commodity threats such as Trickbot that could be used to build botnets or download additional payloads.
Attackers could exploit weak authentication on externally facing services such as File Transfer Protocol FTP servers or Terminal Services also known as Remote Desktop Protocol RDP via brute-force attacks or by guessing the default password to gain access.
Threat actors could also exploit remote code execution vulnerabilities on external services, such as the Oracle WebLogic Server, to download and run mining malware. Social media platforms such as Facebook Messenger and trojanized mobile apps have been abused to deliver a cryptocurrency miner payload. Because each instance of cryptocurrency mining malware slowly generates revenue, persistence is critical to accumulate significant returns. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, scheduled tasks, autostart Windows services, and registry modifications.
For example, threat actors have set cron jobs on Linux systems to periodically download mining software onto the compromised host if it is not already present see Figure 8.
A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Script setting cron job to periodically download and run mining software if not already present on Linux host.
Miner malware payloads are often propagated using lateral movement. Threat actors have used malware that copies itself to mapped drives using inherited permissions, created remote scheduled tasks, used bitcoin mining en el host web 2017 SMBv1 EternalBlue exploit, and employed the Mimikatz credential-theft tool.
In one incident, threat actors added iframe content to an FTP directory bitcoin mining en el host web 2017 could be rendered in a web browser so that browsing the directory downloaded the malware onto the system. This technique has also been observed on Internet-facing websites. Recommendations provided bitcoin mining en el host web 2017 Secureworks IR engagements involving cryptocurrency malware. These recommendations address techniques used by cryptocurrency miners bitcoin mining en el host web 2017 threat actors in compromised environments.
Open RDP and other remote access bitcoin mining en el host web 2017, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. After compromising an environment, a threat actor could use PowerShell or remote scheduled tasks to install mining malware on other hosts, which is easier if the process attempting to access other hosts has elevated privileges.
The most effective means of identifying mining malware on infected hosts is through endpoint threat detection agents or antivirus software, and properly positioned intrusion detection systems can also detect cryptocurrency mining protocols and network connections. Comprehensive and centralized logging is critical for a response team to understand the scale and timeline of an incident when mining malware has infected multiple hosts. Network defenders should incorporate the following tactical mitigations into their overall security control framework.
These mitigations are effective against a broad range of threats:. Cryptocurrency mining is an attractive proposition for threat actors seeking to monetize unauthorized access to computing resources. It will remain a threat to organizations as long as criminals can generate profit with minimal overhead and risk. Bitcoin mining en el host web 2017 has bitcoin mining en el host web 2017 a significant increase in cryptocurrency mining activity across the Secureworks client base since July Although cryptocurrency malware may not seem as serious as threats such as ransomware, it can have a significant impact on business-critical assets.
Organizations should ensure that appropriate technical controls are in place. The mitigations for installation, persistence, and lateral movement techniques associated with cryptocurrency malware are also effective against commodity and targeted threats. No Ifs and Buts About It. Zavodchik, Maxim and Segal, Liron. Research Cryptocurrency Mining Malware Landscape.
Key points This threat can have a significant impact. If critical and high-availability assets bitcoin mining en el host web 2017 infected with cryptocurrency mining software, then computational resources could become unusable for their primary business function. Heavy processing loads could accelerate hardware failure, and energy costs could be significant for an organization with thousands of infected hosts.
Unauthorized cryptocurrency mining indicates insufficient technical controls. If it is possible for an initial malware infection to deliver and spread cryptocurrency miners within an environment without being detected, then that same access vector could be used to deliver a wide range of other threats. The threat of cryptocurrency mining malware increased in Financially motivated threat actors are drawn to its low implementation cost, high return on investment, and arguably lower risk of law enforcement action than traditional malware because the impact is less visible or disruptive.
The upward trend of cryptocurrency miner infections will continue while they offer a positive return on investment. Threat actors may carefully manage the impact on an infected host to reduce the likelihood of detection and remediation.
Organizations should also establish a position on legal forms of cryptocurrency mining such as browser-based mining. While this form of mining has a legitimate use, organizations might still consider it an unacceptable use of corporate resources. Cryptocurrency mining criminality Cryptocurrency is attractive to financially motivated threat actors as a payment method and as a way to generate revenue through mining: The decentralized nature of many cryptocurrencies makes disruptive or investigative action by central banks and law enforcement challenging.
Multiple cryptocurrencies promote anonymity as a key feature, although the degree of anonymity varies. For example, security researchers were able to analyze publicly viewable records of Monero payments made to the Shadow Brokers threat group for bitcoin mining en el host web 2017 leaked tools. For criminals with control of an infected system, cryptocurrency mining can be done for free by outsourcing the energy costs and hardware demands to the victim.
Access to networks of infected computers can be sold as a service. Cryptocurrency miners can be combined with threats such as information stealers to provide additional revenue. Organizations may not detect and respond quickly to cryptocurrency mining because they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware.
As a result, threat actors have more time to generate revenue and law enforcement may take longer to react. Between andthere were several notable developments in cryptocurrency mining malware: Cryptocurrency mining malware developers quickly incorporated highly effective techniques for delivery and propagation.