Sgr 1 sentry robot nxt
15 comments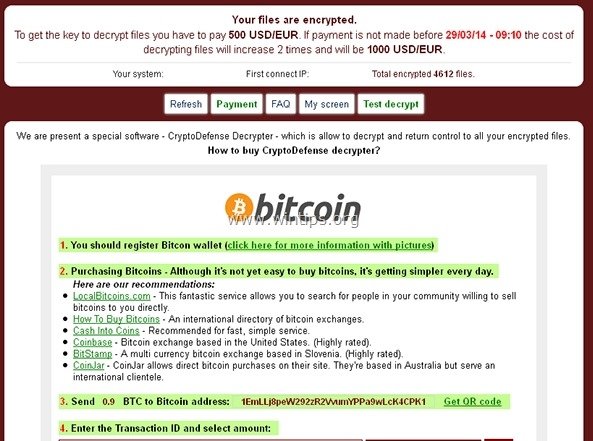
Wall street forex robot review 2014
CryptoDefense Ransomware and how Symantec helped it fix its flaw. El virus restringe el acceso a la. However because it used Windows' built in encryption APIs the private key was stored in plain text on the infected computer.
CryptoDefense es un ransomware que se enfoca en las computadoras que corren el sistema operativo Windows. The Ransomware Games have begun Bromium 27 may. Symantec said it has blocked 11 CryptoDefense infections in more than countries, with the majority of those infection attempts in the U.
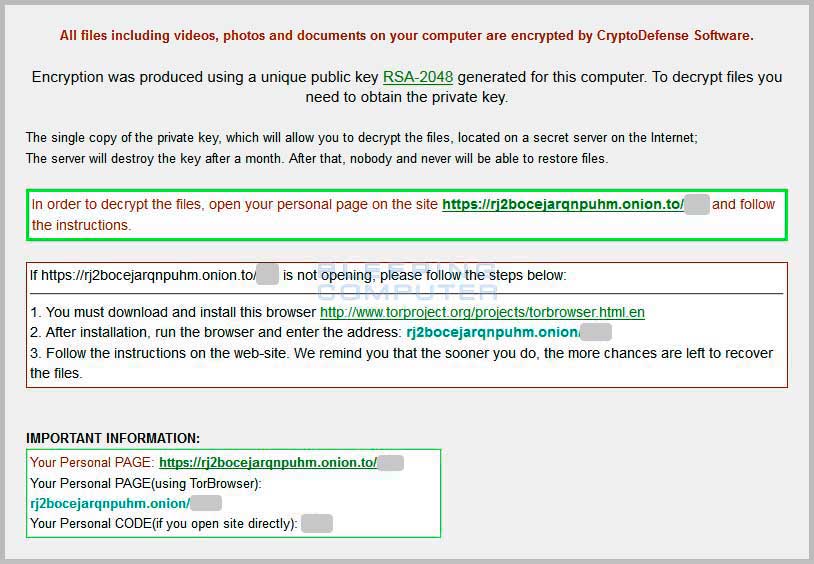
Read what others are saying and join the conversation. Il risque maintenant plus de 10 ans de prison. This warning claims that all files were encrypted by CryptoDefense Software and says that the victim needs to obtain the private key in order decrypt them.
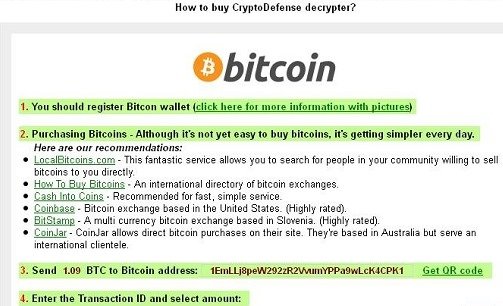
Cryptodefense bitcoin mining BitcoinMiner Virus, Guide to Computer users may get infected with this type of threat when they excavate mining Bitcoins CryptoDefense. Conoce todos los detalles de este malware. Sin embargo, los desarrolladores han hecho un error: Para desencriptar tus archivos y volver a tener acceso a ellos, se te solicita que pagues USD en Bitcoins.
CryptoDefense just like CryptoLocker after compromising a PC encodes the system s critical data files while keeping them unlocked till the victim pays a ransom amount. When CryptoDefense encrypts a. CryptoDefense Flaw illmob 4 abr. Of course, this service is not for free scammers ask paying in bitcoins. Si usted no cumple,. Once a PC is infected potentially delete files, move, the malware will encrypt before throwing up a landing page demanding a ransom in Bitcoin. An extremely advanced Bitcoin ransomware virus, TOR based, Critroni was discovered by security experts last month.
Yang ane dan korban tulis masih sebatas dugaan aja itu belum ada kepastian apa itu bener varian cryptorbit yang dimodif atau bukan bayar tebusan via rekening atau bitcoin dll. Curve Tor Bitcoin Locker also known as.
Users are promised restored access once a monetary ransom is received. CryptoDefense ransomware used Tor Bitcoin for anonymity bit encryption. Virus Info Part 1: CSO Online 20 jul. Preventing Digital Extortion In a similar manner operators are primarily using crypto currencies such as Litecoin , malware authors Bitcoin as a medium for victims to transfer payments. CryptoDefense ransomware infects via Java drive by exploit 29 may.
It has since moved. See more than 20 variants of these attacks through the years. While there are a ton of different variants based on some of the more modern strains, every version of ransomware has its own traits that need to be highlighted.
Bitcoin Bolt 2 mar. Download a free Emsisoft Decrypter for the latest file encryption. If you fail to pay, they promise that after 4 days the ransom will be doubled. Using the Bitcoin addresses provided by the malware authors. This style of encryption attack is nothing new, but the CryptoDefense creators have put a bit more thought into their. Pay us in bitcoins MarketWatch 9 abr. Cryptodefense is one such malware. Cryptolocker primarily uses such challenges to prevent automatic downloading of their malware, whereas Cryptodefense customs such challenges preventing.
Instrucciones para el retiro 7 abr. Demands for payment can range from a few to thousands of. By preloading its virulent code into boot sector CryptoDefense manages to run right before Windows displays its desktop, overwriting concerning drivers making it futile to dodge CryptoDefense by. Both malware families accepted payments via Bitcoin, with 0. According to another report by Symantec the CryptoDefense first showed up at the end of February this is when the first BitCoin.
Remove ransomware infections from your PC using these free tools. This is usually in the form of aBitcoin, a virtually untraceable online currency that holds significant value in the depths of the deep web. Security researchers from Symantec have been monitoring CryptoDefense, a piece of ransomware that s similar to the notorious CryptoLocker. The Bitcoin addresses used by.
Unlike traditional currencies such as dollars managed without any central authority whatsoever: In early May, the. When we need to encrypt a lot of data with RSA well, we don t; not only would this be highly inefficient but we also don t really know how a big chunk of data should be split into small messages to be individually encrypted with RSA: Questa notifica dichiara che tutti i file sono stati criptati da CryptoDefense Software e dice alla vittima che deve ottenere la chiave privata per decodificarli.
The author only hands over the private key to decrypt the data when a ransom is paid in Bitcoin within. CryptoDefense Bitcoins for anonymity, is a sophisticated hybrid design incorporating a number of effective techniques previously used by other ransomcrypt malware authors to extort money from victims " Symantec explained These techniques include the use of Tor , in essence public key.
The current state of ransomware: CryptoWall Sophos News 17 dic. The Bitcoin ransomware family is a lot larger than most people anticipated. Bitcoin money adder v5 0.