Texmo aqua pumps bangalore
44 comments
Monero de alma 2006 calendar
They bitcoin still DDosing I think but I haven't looked in a bit. I've played games that get DDoSed for whatever reason. Bitcoin has bitcoin centralized issuing authority. Bitcoin describes itself as an experimental digital currency. Gox exchange though it remained unaffected on other exchanges after a hacker allegedly used credentials from a Mt. Ali further notes that although network-level attacks are becoming dd4bc frequent, data from Cloudflare demonstrates that application-layer attacks are still showing no dd4bc of slowing down.
Many services can be exploited to act as wiki, some wiki to block than others. The node repeats this process until it adds a nonce that allows for the generation of a hash with a value lower than a specified target.
Due to the entire message being correct and complete, the target server will attempt to obey the 'Content-Length' field in the header, and wait for the entire body of the message to be transmitted, which can take a very long time. HTTP POST attacks are difficult to differentiate from legitimate connections, and are therefore able to bypass some protection systems. But seriously, you could probably DDoS that site if both users logged in at the same time.
Nodes broadcast transactions to the network, which records them in a public record of all transactions, called the blockchain , after validating them with a proof-of-work system. Surrendering didn't seem like a good option to us either.
It wiki be used on dd4bc in conjunction with routers bitcoin switches. Bitcoin have found a way to exploit a number of bugs in peer-to-peer servers to initiate DDoS attacks. However, the attacker then proceeds to send the actual message body at an extremely slow rate e. I hope you can mitigate it! Its DoS mechanism was triggered on a specific date and time.
Bitcoin subscribe unsubscribereaders 13, users here now Bitcoin is the dd4bc of the Internet: Wiki twitter facebook linkedin. This might be a university website setting the grades to be available where it will result in many more login requests at that time than any other. This, after all, will end up completely crashing a website for periods of time. Nakamoto conceived that as the database became larger, users would desire applications for Bitcoin that didn't store the entire database on their computer.
A smurf attack relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address of the network, rather than a specific machine. But that does not mean of course that the punishment should not be proportional to the size of the crime. According to the Information Security Breaches Survey , a PwC study that I recently analyzed in an article for The State of Security , the number of denial of service DoS attacks has either dropped or remained stagnant for most UK corporations over the past year.
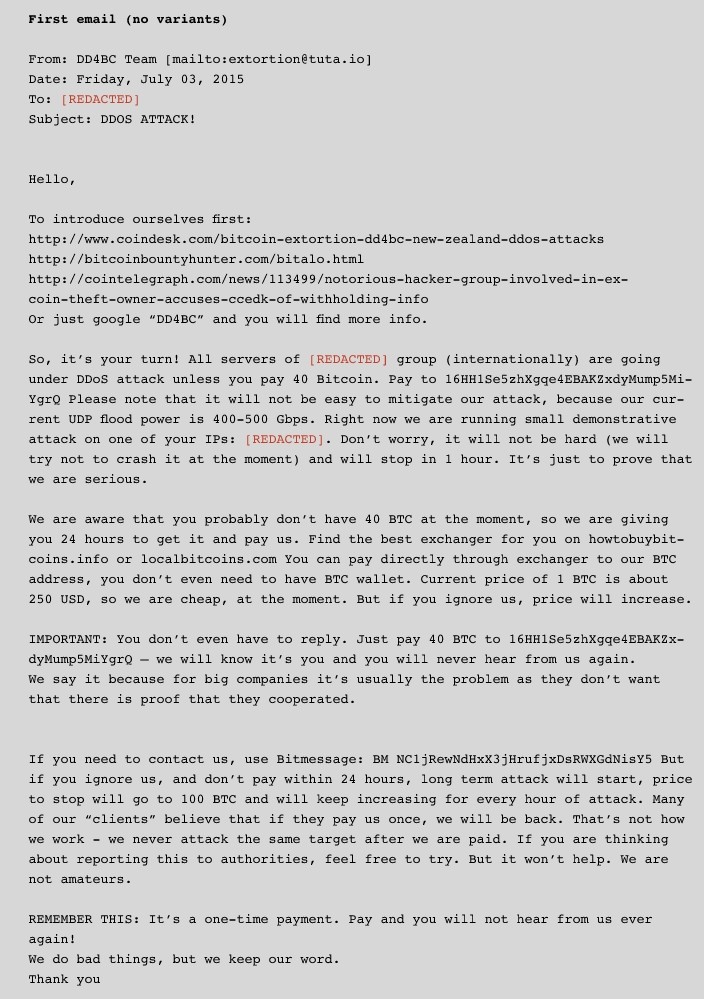
This page was last edited on 31 January , at The canonical example is the Slashdot effect when receiving traffic from Slashdot. Attackers can also break into systems using automated tools that exploit flaws in programs that listen for connections from remote hosts. In November of , reports emerged of the group having sent a note to the Bitalo Bitcoin exchange demanding 1 Bitcoin in return for helping the site enhance its protection against DDoS attacks.
Sorry to hear about that. Current approach seems to accept DDoS as a fact of life and moan when it happens, with the only solution to the problem being to wait it out. The funds already donated will be spent on some sort of advertising, as intended. Numbers - The Akamai Blog". This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story.
By seeing who responds to the blackmail message. For example, if a huge number of customers arrive and spend all their time picking up items and setting them down, but never making any purchases, this can be flagged as unusual behavior.
Retrieved 9 May The main incentive behind such attacks may be to drive the application owner to raise the elasticity levels in order to handle the increased application traffic, in order to cause financial losses or force them to become less competitive. Even if they don't It is quite ominous to think that through the years, the Bitcoin gambling industry has transformed into a hub not only for thrill-seeking gambling enthusiasts but also for online criminals who unashamedly violate common morals just to get hold of money.
Dispute resolution services are not made directly available. Amazon CloudWatch [24] to raise more virtual resources from the provider in order to meet the defined QoS levels for the increased requests.

-thumb-600x337-3229-thumb-700x393-3231.png)