Blockchain in capital markets operations
49 comments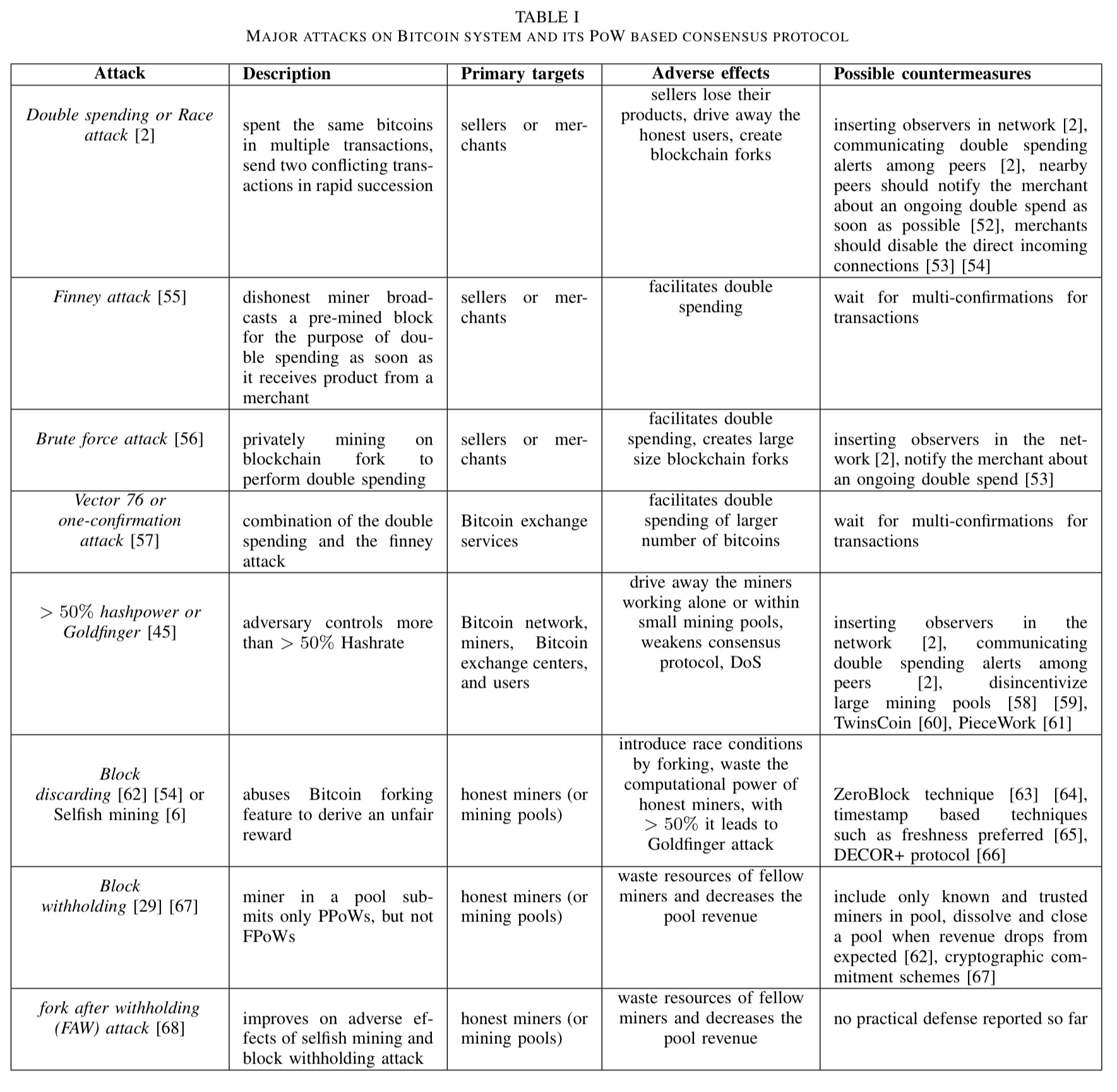
Bitcoin hash rate graphics cards
Bitcoin, is THE most valued crypto currency in the world. From the time of its inception to the very present day, its value has escalated many folds drawing the attention of millions of investors and hackers all over the world. Organizations are moving towards a more decentralized approach in keeping ledger records mutually dependent to keep a check on the integrity as well as assuring safety to the transactions on the blockchain. As Bitcoin grows more popular and expensive, it is becoming more and more prone to cyber-attacks.
Disruption of Bitcoin network could cause a significant drop in the revenue earned by miners and could also prevent smooth transactions from getting processed. In the past few years, there has been quite a number of attacks on Bitcoin network.
There has been Sybil attack, packet sniffing attack, Timejacking attacks and Denial of Service DoS attacks to mention a few. To add further, it has been noticed that the major portion of the traffic flowing in the network might traverse just a few ISPs i.
It is possible for an Internet Service Provider to partition the Bitcoin network. They can do this just by hijacking few IPs prefixes from which a major part of Bitcoin traffic is generated. This is how it happens:.
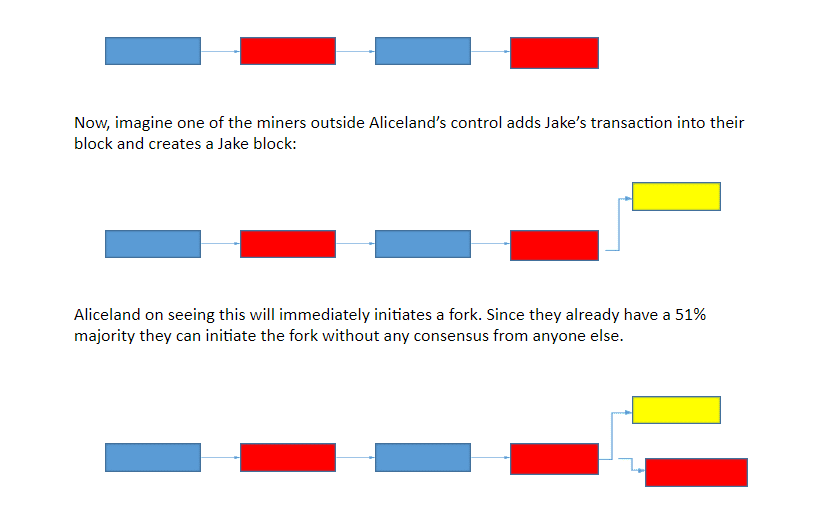
Nodes of the left-hand side and the right-hand side of the network communicate through Bitcoin connections denoted by blue lines. The aim of the attacker is to split the network into two disjoint components: After BGP hijack is successful, all traffic sent from the right-hand side to the left-hand side is forwarded through the Attacker marked in red lines.
In this attack scenario, the intention of the attacker is to delay the delivery of a block to a victim node. During this period the victim is unaware of the most recently mined block and the corresponding transactions. The impact of this attack varies depending on the victim. If the victim is a merchant, it is susceptible to double spending attacks. If it is a minor, the attack wastes its computational power. Finally, if the victim is a regular node, it is unable to contribute to the network by propagating the last version of the blockchain.
It is possible for an attacker to stealthily make the delivery of a Bitcoin block to a victim node with the time delay. During the course of this attack, the victim is completely unaware of the most recently mined block and the corresponding transactions. The impact of this attack varies depending on the role of the victim. Victim Role - Miner: Computational power spent by the miner is wasted as the blocks received are of no value.
Victim Role - Regular node: It will not be able to add any contribution towards the blockchain network as it will propagate an irrelevant version. The attacker modifies the content of the request in such a way that Node C gets an older block from Node A. Before the completion of 20 mins of the original request by Node C the attacker sends another modified GetData request to Node A.
The block is delivered to the victim Node C just before the 20 minutes timeout. Due to this Node, C does not disconnect from Node A and continues to receive the older blocks totally unaware. Skip to main content. Home About Us Jobs. Home Security Articles Bitcoin Under attack!! Due to the above factors, there are two types of attacks which are practically possible: This is a possibility of a node in the Bitcoin network to intentionally delay its block propagation by nearly 20 minutes staying undetected.
This is how it happens: Nodes of the left-hand side and the right-hand side of the network communicate through Bitcoin connections denoted by blue lines Step 2: The Attacker performs a BGP hijack and attracts the traffic destined to the left nodes.
The attacker cuts these connections and divides the network into two separate pieces. The nodes on each side continue to connect to other nodes on the same side. Delay Attack In this attack scenario, the intention of the attacker is to delay the delivery of a block to a victim node. Victim Role - Merchant: Double spending attacks might become possible. Two blocks with the same data are shown by Nodes A and B to victim Node c.
The attacker modifies the content of the request in such a way that Node C gets an older block from Node A Step 3: After the malformed request is received by Node A, it delivers an older block to Node C. Before the completion of 20 mins of the original request by Node C the attacker sends another modified GetData request to Node A Step 5: Related articles baseStriker Attack: An Introduction to Identity and Access Management.