Bitcoin org wallet
36 comments
Dogecoin online wallet
From the department of cosmic justice comes this gem, spotted by researchers from Symantec: Once installed, the trojan components are stored in an invisible folder and use strong encryption to keep communications private. The bot can force its host to take instructions through internet relay chat, perform DDoS attacks, and post fraudulent messages to the victim's Facebook account, among other things.
Now, Symantec researchers have uncovered weaknesses in the bot's peer-to-peer functionality that allow rival criminals to remotely steal or plant files on the victim's hard drive.
That means the unknown gang that took the trouble to spread the infection in the first place risks having their botnet stolen from under their noses. Jnanabot's P2P feature is designed to make botnets harder to take down by providing multiple channels of communication.
After sending an infected machine a single GET request, a website can discover all the information needed to upload any file to any location on the host's file system. Attackers can then install a simple backdoor on a user's machine by, for instance, writing a malicious program to a computer's startup directory. Still, infection statistics gathered by Symantec in December are surprising.
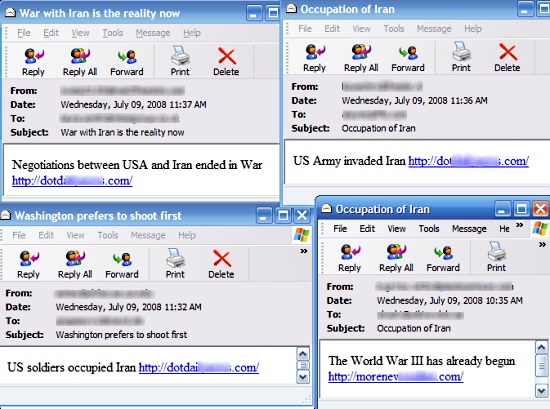
They show that about 16 per cent of infections hit Macs. They didn't show any infections on Linux machines. Turner said that Jnanabot attacks on the open source platform weren't able to survive a reboot. The bot was discovered spreading over Facebook posts that planted the following message on infected users' Facebook pages: Once the recipient is infected, his Facebook page carries the same dire warning.
It's not the first time that malware developers have built gaping vulnerabilities into their wares. In September, researcher Billy Rios disclosed a weakness in the Zeus crimeware kit that makes it easy to take over huge networks of infected PCs. Symantec has more about the trojan here , here , and here. Minds Mastering Machines - Call for papers now open. The Register - Independent news and views for the tech community.
Part of Situation Publishing. Join our daily or weekly newsletters, subscribe to a specific section or set News alerts. The Register uses cookies. Brakes slammed on Pentagon's multibillion cloud deal Risky business: You'd better have a plan for tech to go wrong Africa's internet body hit with sexual harassment cover-up claims.
Windows Notepad fixed after 33 years: Now it finally handles Unix, macOS line endings Microsoft reckons devs would like an AI Clippy to help them write code Microsoft vows to bridge phones to PCs, and this time it means it. Give us notch support or … you don't wanna know.
Equifax reveals full horror of that monstrous cyber-heist of its servers Android P to improve users' network privacy Hacking charge dropped against Nova Scotia teen who slurped public records from the web That Drupal bug you were told to patch weeks ago? Cryptominers hope you haven't bothered.
Get on top of reliability with our best practices webinar. Sony reports shortage of cute robot puppies! Predictable senility allows boffins to spot recycled NAND chips Waymo van prang, self-driving cars still suck, AI research jobs, and more Congratulations, we all survived Star Wars day! Now for some security headaches.
Verity Stob Yes, people see straight through male displays of bling they're only after a fling New Monty Python movie to turn old jokes into new royalties Mystery crapper comes a cropper The steaks have never been higher: Swiss Lidl is selling local cannabis.
Attackers can use the same vulnerability to steal files on infected machines. Most read Equifax reveals full horror of that monstrous cyber-heist of its servers Zombie Cambridge Analytica told 'death' can't save it from the law Heir to SMS finally excites carriers, by making Google grovel Microsoft's most popular SQL Server product of all time runs on Linux Admin needed server fast, skipped factory config … then bricked it. More from The Register. Hurry up patching those Oracle bugs: Attackers aren't waiting Honeypots swarmed on within three hours of patch release.
Malware Engine needs, erm, malware protection Stop appreciating the irony and go install the patch now. Umm, Oracle — about that patch?
It might not be very sticky Security researcher says WebLogic fix can be bypassed, posts proof-of-concept. Oracle slurps bot-wrangling security minnow Zenedge Buy price not revealed. Orangeworm malware targets hospitals worldwide Hacking campaign goes after care providers and equipment.
Terix boss thrown in the cooler for TWO years for peddling pirated Oracle firmware, code patches Big Red all smiles after black-market support biz bosses jailed. Security bods liberate EITest malware slaves Miscreants' command and control network traffic sent down sinkhole. Whitepapers Ransomware is Increasing the Risks and Impact to Organizations Ransomware is gaining traction in the criminal community.
Before proceeding we must understand what the definition of the words Certification and Accreditation. Massive backlogs, legacy debt, and scarce resources can hinder digital transformation efforts.
So, how you can overcome these challenges? Sponsored links Get The Register's Headlines in your inbox daily - quick signup! About us Who we are Under the hood Contact us Advertise with us. Sign up to our Newsletters Join our daily or weekly newsletters, subscribe to a specific section or set News alerts Subscribe.