To Salt or Not To Salt? - Salting is not the only answer to securing passwords
5 stars based on
54 reviews
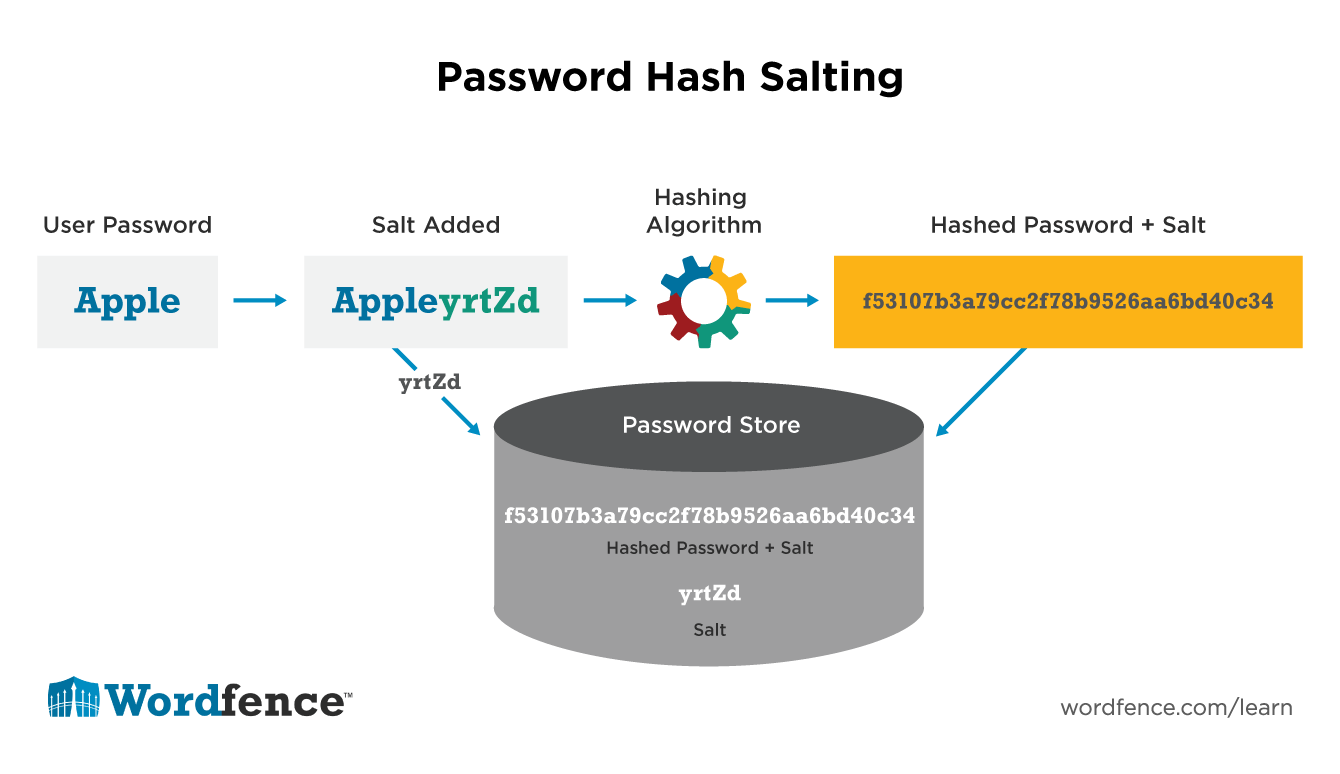
So it has been released that LinkedIn failed to salt its passwords in the hack, and while salting would have increased the time it bcrypt hash calculator bitcoin to crack a salted hash, it is merely a bump in the road if users use passwords such as "". Because the salt is typically stored with the hashed password, so if the user selects "", the cracker just selects a dictionary with this password and then adds the salt, and compares it.
You don't have to be Eve The Magician to realise that if I tell you that my password is "qwerty", and you take a hash signature of it to get: If the salt is stored with the hashed value, it is of little bcrypt hash calculator bitcoin with easily guessed passwords. While this is true, the shocking truth that the passwords themselves would have been cracked even with salting. If the salt is kept with the hashed password, as most systems do, bcrypt hash calculator bitcoin weak passwords which come from dictionaries would have been easily cracked.
In Linkedin was hacked, and there was a leak of 6. The passwords themselves are hashed version, but these are fairly easily to crack with rainbow tables, especially as users tend to pick weak passwords. Many organisations think they are safe as they use salted passwords, but they are not if they use bcrypt hash calculator bitcoin passwords. With Bcrypt we get a number of rounds for the hashing, so if I increase the number of rounds from 6 to The penalty is that it is slower to hash, bcrypt hash calculator bitcoin there a sweet spot, but with computing power vastly increasing in the cloud, every crypto method needs a bit of slack!
Bcrypt hash calculator bitcoin cryptography we like things to be fast in order that we can process things in real-time. Generally we have moved from running cryptography on hardware to software implementations.
With hashing methods we often want to bcrypt hash calculator bitcoin things down, as we want to stop an intruder from brute forcing the hash where they try a wide range of passwords. We can add salt, but if the intruder gets the salt, they can try popular passwords. Computing power, too, is increasing massively, especially around parallel processing in the Cloud, and with GPU Graphics cards which can have over 4, cores, each capable of try a range of hash values.
There are four core concepts in cryptography: All of the methods above allow for the easy reverse of the encryption or encoding process if the key is known, apart from one-way hashing where it should be almost impossible to reverse back the hashed value to the original data. Unfortunately technology has moved on since the creation of hashing methods, and they can often be easily cracked using brute force where an intruder keeps hashing values until the output matches the hash using a dictionary of common passwords, or use a rainbow table which has a pre-compiled list of hash values.
Now this becomes more difficult as the same password is likely to produce a different bcrypt hash calculator bitcoin. Before, with simple hashing, if one hashed password was cracked, all the other passwords with the same value will also be cracked. The weakness is that the salt requires to be stored with the password, so the intruder just uses a fast computer - such bcrypt hash calculator bitcoin using NVIDIA graphics cards bcrypt hash calculator bitcoin the Amazon Cloud - and tries all the main passwords, and is able to determine the original password.
The reason this happens is become SHA has been designed to be fast, so the intruder uses this for their advantage, and can quickly try lots passwords. If the password is weak and in a dictionary it is relatively easy for the bcrypt hash calculator bitcoin. So the walls of crypto are falling, especially due to high performance computers, but one solution is to use a hashing method which slows down the process of hashing, adds a bit of salt, and then iterates.
This makes it extremely difficult to compile the list of hashes, as it is computationally expensive to compute them - on the Cloud time is money, so a computationally difficult challenge many take years to complete and thus be costly.
It is used in TrueCrypt to generate the key required to read the header information of the encrypted drive, and which stores the encryption keys, and also in WPA-2 to protect the wi-fi password for the pre-shared key.
If you're interested, here's an overview:. And a calculator is here:. MD5 and SHA-1 produce a hash signature, but this can be attacked by rainbow tables. Bcrypt is a more powerful hash generator for passwords and uses salt to create a non-recurrent hash. It is used as the default password hashing method for BSD and other systems.
Overall it uses a bit salt valuewhich requires 22 Base characters. It can use a number of iterations, which will slow down any brute-force cracking of the bcrypt hash calculator bitcoin value. The bit 22 character salt values comes after this, and then finally there is a bit hash code which is 31 bcrypt hash calculator bitcoin. The following provides an example of Bcrypt [ here bcrypt hash calculator bitcoin.
With John The Ripper:. So, although the main hashing methods are fast and efficient, this speed has bcrypt hash calculator bitcoin down-side, in that they can be cracked easier. With Bcrypt the speed of cracking is considerably slowed down, with each iteration doubling the amount of time it takes to crack the hash with brute force.
Bcrypt hash calculator bitcoin this case we see we are using 12 iterations and a pre-prepared salt of "" 22 characters to give a bit salt value:. So, in the days of massively parallel systems, swimming in molasses is a good thing for protecting passwords. The bcrypt hash calculator bitcoin iterations we have for each round is good too, as it makes it more difficult to crack. Bcrypt is still a strong contender, though. I reckon the value goes from 6 to So, just because your company uses salted passwords, doesn't make them secure.
What we need is multi-factor authentication for logging into system, and if we use passwords they should be long phrases with a mixture of character types. Unfortunately, many on-line systems are still not supporting these.
Virgin Media, for example, ask for a password between 8 and 10 digits long, and think that 'qwerty11' is a good password and where the first character must be a character:. In particular, LinkedIn failed to adequately protect user data because it stored passwords in unsalted SHA1 hashed format.
Background In Linkedin was hacked, and there was a leak of 6. A Few Basics There are four core concepts in cryptography: If you're interested, here's an overview: And a calculator is here: The following provides an example of Bcrypt [ here ]: With John The Ripper: Here is the Python implementation: In fact it will show by a factor of 4.
Conclusion So, in the days of massively parallel systems, swimming in molasses is a good thing for protecting passwords. Postscript So, just because your company uses salted passwords, doesn't make them secure. Virgin Media, for example, ask for a password between 8 and 10 digits long, and think that 'qwerty11' is a good password and where the first character must be a character: Finally, you can test password strength here: