Ethereum price chart usdx
39 comments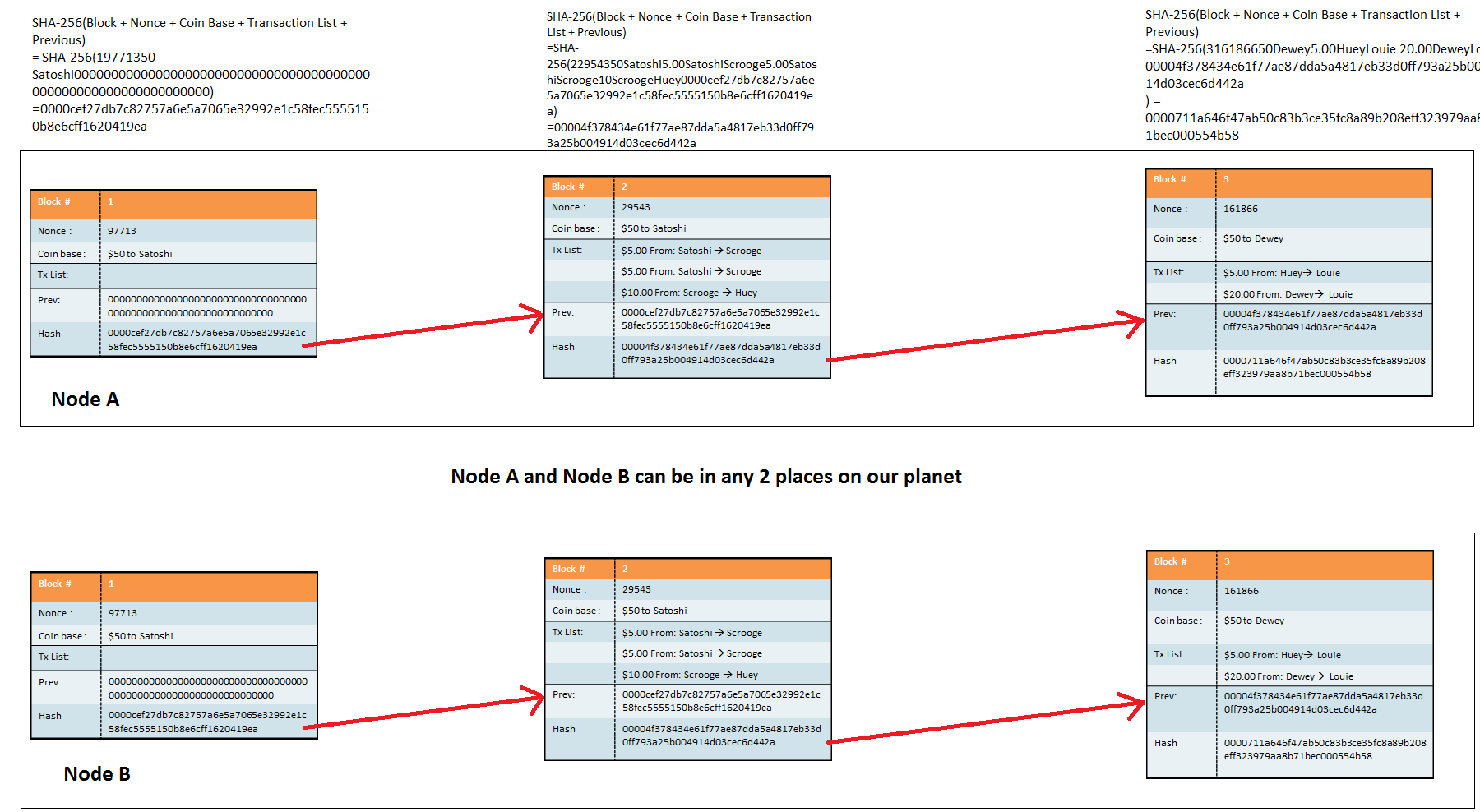
Ira miller bitcoin stocks
In Part 1 we took a look at the incentives involved in Bitcoin mining and how they are used guarantee a single transaction history needed to prevent bitcoins from being double spent. In this post we will take more a technical look at the cryptography involved and how it is used to secure the network.
As I said previously, Bitcoin is very accessible. Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol. To put it simply, a hash function is just a mathematical algorithm that takes an input and turns it into an output. For example, suppose we have an algorithm which just adds all the digits in the input string together. If our input is we would get an output of However, there are certain properties of really good hash functions that make them suitable to use in cryptography.
Keep these properties in mind as they are vital to the operation of the Bitcoin protocol. The output should be the same length regardless of whether the input has 10 characters or 10 thousand characters. A tiny change in the input should produce an entirely different output that in no way relates to the original input. You might wonder how we can trust something that came from the NSA. The consensus is that they are secure. Now that we have the preliminaries out of the way we can start focusing in on the protocol.
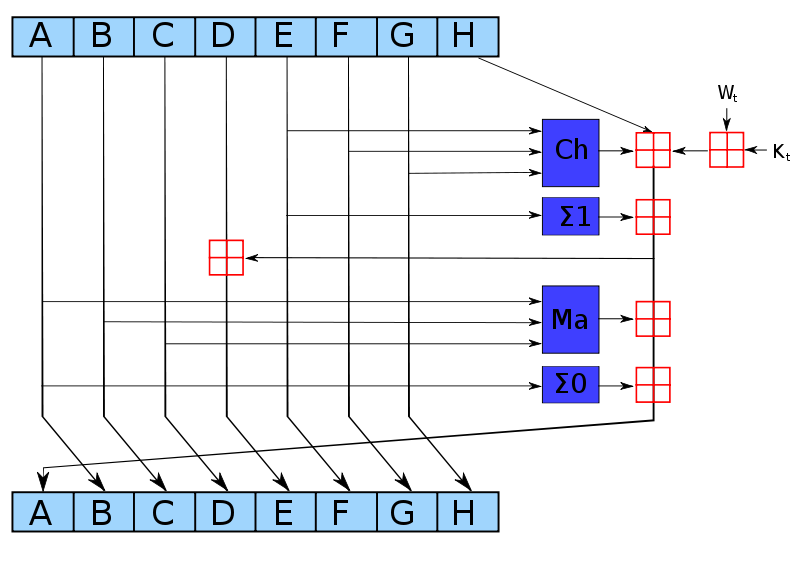
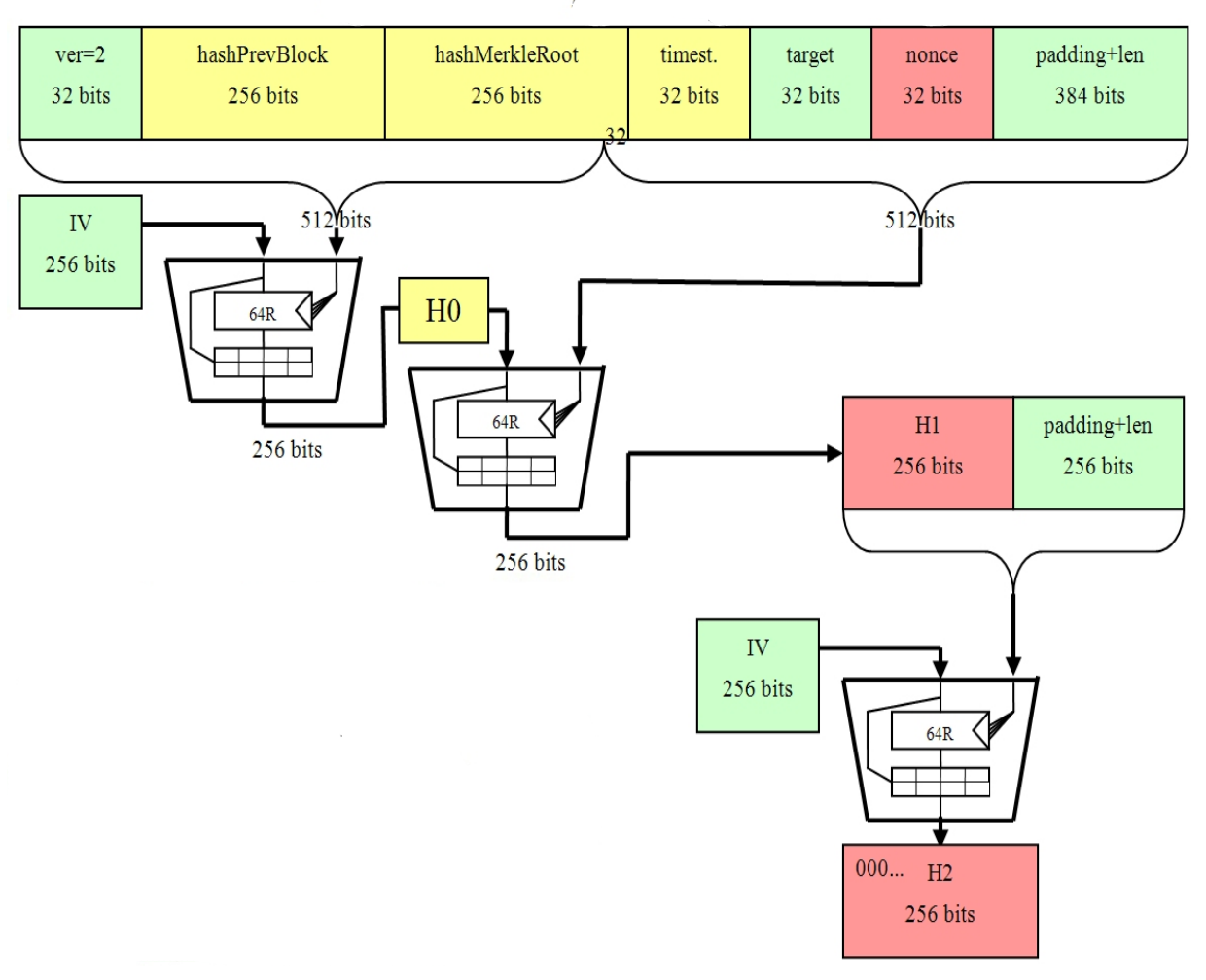
If you read Part 1 you will recall that all Bitcoin transactions are relayed to each of the peers in the network. The first step in the process is to hash each transaction in the memory pool using SHA The raw transaction data may look something like this:. These hashes are then organized into something called a Merkle Tree or hash tree.
The hashes of the transactions are organized into pairs of twos, concatenated together, then hashed again. The same is done to each set of outputs until something like a tree is formed or an NCAA bracket. In the above example there are only four transactions tx stands for transaction. A real block will contain hundreds of transactions so the bracket tree will be much larger. The hash at the very top of the tree is called the Merkle Root. The block header will look something like this:.
Now having done all this can we go ahead and relay the block to the rest of the network? If you recall the last post, the answer is no. We still need to produce a valid proof of work. The output must be less than the specified number. Another way of saying this is that the hash of the block header must start with a certain number of zeros.
For example a valid hash may look like this: Any block whose header does not produce a hash that is less than the target value will be rejected by the network. The target value is adjusted by the protocol every two weeks to try to maintain an average block time of 10 minutes.
This is where the nonce comes in. The nonce is simply a random number that is added to the block header for no other reason than to give us something to increment in an attempt to produce a valid hash. If your first attempt at hashing the header produces an invalid hash, you just add one to the nonce and rehash the header then check to see if that hash is valid. This is Bitcoin mining in a nutshell. This is essentially what Bitcoin mining is, just rehashing the block header, over, and over, and over, and over, until one miner in the network eventually produces a valid hash.
When he does, he relays the block to the rest of the network. If so, they add the block to their local copy of the block chain and move on to finding the next block. However, the more hashes that you can perform per second, the greater the probability that you will mine a block and earn the block reward.
CPU mining quickly gave way to GPU mining graphics processing units which proved much more efficient at calculating hash functions. Basically, these are purpose built computer chips that are designed to perform SHA calculations and do nothing else. At present, the total hashing power in the network is about terrahashs per second and closing in on one petahash per second.
Because each miner is sending these 25 bitcoins to his own address, the first transaction in each block will differ from miner to miner. Now remember the properties of a cryptographic hash function? If an input changes even in the slightest, the entire output changes. Since the hash of the coinbase transaction at the base of the hash tree is different for each miner, the entire hash tree including the Merkle root will be different for each miner.
That means the nonce that is needed to produce a valid block will also be different for each miner. This is the reason why the Merkle tree is employed after all. Any change to a single transaction will cause an avalanche up the hash tree that will ultimately cause the hash of the block to change. If an attacker wants to alter or remove a transaction that is already in the block chain, the alteration will cause the hash of the transaction to change and spark off changes all the way up the hash tree to the Merkle Root.
Given the probabilities, it is unlikely a header with the new Merkle Root will produce a valid hash the proof of work. Hence, the attacker will need to rehash the entire block header and spend a ton of time finding the correct nonce. But suppose he does this, can he just relay his fraudulent block to the network and hope that miners will replace the old block with his new one or, more realistically, that new users will download his fraudulent block?
The reason is because the hash of each block is included in the header of the next block. If the attacker rehashes block number , this will cause the header of block to change, requiring that block to be rehashed as well. A change to the hash of block will cause the header of block to change and so on all the way through the block chain.
Any attempt to alter a transaction already in the block chain requires not only the rehashing of the block containing the transaction, but all other subsequent blocks as well.
Depending on how deep in the chain the transaction is, it could take a single attacker weeks, months, or years, to rehash the rest of the block chain. The only exception to the above rule is if the attacker simply gets lucky.
As we noted, it takes the entire network an average of 10 minutes to find a valid block. The deeper a transaction is in the block chain, however, the more times in row the attacker would need to get lucky and mine a block before the rest of the network to extend his chain longer than the main chain.
From a probability standpoint, the chances of such an attack succeeding decrease exponentially with each subsequent block. In the original white paper Satoshi Nakamoto calculated the probabilities that an attacker could get lucky and pull off a double spend.
In the following table q is the percentage of the network controlled by the attacker, P is the probability an attacker could get lucky and override z number of blocks. Which is usually why it is recommended that if you are selling something expensive, you should wait until your transaction is six blocks deep six confirmations in Bitcoin lingo before actually handing over the merchandise. This post got long in a hurry. Hope you enjoyed these posts and I hope you learned something.
I found your post comments while searching Google. It is very relevant information. Regularly I do not make posts on blogs, but I have to say that this posting really forced me to do so. Really fantastic and I will be coming back for more information at your site and revisit it! I still have one question though: Smart Contracts Great Wall of Numbers.
Part 2 — Mechanics … Bitcoin. For the hash chaining, does it mean if somebody get one valid hash, I need to update and download it and re-calculate based on his block? Or can I make a new branch based on previous block? Bitcoin Online resources collected The Bitcoin Journey How Cryptocurrencies Work Bitcoin Getter. Bitcoin has seen rapid increases during the last year and there are now those who are claiming that the bubble is soon to burst and Bitcoin crumble.
Those of us continue believe in the idea of a user owned system away from the reach of the banks. We do not believe that the currency is finished.
We shall be staying with Bitcoin and I am quite confident that it will continue to rise more rapidly than before. Bitcoin Frenzy — Is it the next gold or just a bubble? How Cryptocurrencies Work - Cryptocurrency How Cryptocurrencies Work — Bitcoin Support. Thanks for a great article. How then does the miner broadcast that to the rest of the network to get consensus on the work if his nonce is unique from what another miner would have theoretically found?
Cryptocurrency trading is becoming a profession — The Glimpse. How Cryptocurrencies Work — Bitcoin Supports. You are commenting using your WordPress. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email.
Cryptographic Hash Functions Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol. It should be very easy to compute an output for any given input, however it should be impossible given current knowledge of mathematics and the state of computers to compute the input for a given output even while knowing the mathematical algorithm.
In this case there are many possible inputs that could add up to 10 55, , , etc. However, given the simplicity of our function one could still figure out the input relatively easily.