270x litecoin toxique
37 comments
Davi barker bitcoin stock price
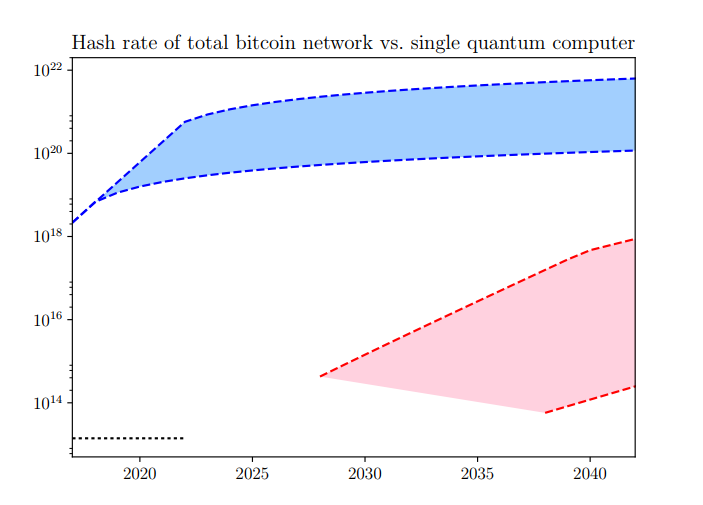
The researchers from Singapore, Australia and France say that scenario represents the worst case, and would see a quantum computer able to run Shor's algorithm against the cryptocurrency's protective elliptic curve signature quicker than the 10 minutes Bitcoin needs to record a transaction in the blockchain.
There are two items of good news in the paper for Bitcoin: In their paper , which landed at arXiv in late October, Divesh Aggarwal and his collaborators say ASIC-based mining rigs are fast compared to even optimistic theoretical quantum computer clock speeds. The extreme speed of current specialized ASIC hardware for performing the hashcash PoW, coupled with much slower projected gate speeds for current quantum architectures, essentially negates this quadratic speedup, at the current difficulty level, giving quantum computers no advantage.
Future improvements to quantum technology allowing gate speeds up to GHz could allow quantum computers to solve the PoW about times faster than current technology. As far as defeating hashcash goes, the numbers are daunting for quantum computer designers: Shor's algorithm, a quantum algorithm for factoring integers that's how it would attack cryptography , is a better path, they write. Deploying a quantum computer against the secpk1 elliptic curve Bitcoin uses is much more dangerous: As with cracking the proof-of-work, the researchers assume quantum computers get big and fast relatively quickly, and even so, they fall slightly short: The Register - Independent news and views for the tech community.
Part of Situation Publishing. Join our daily or weekly newsletters, subscribe to a specific section or set News alerts. The Register uses cookies. Blame everything on 'computer error' — no one will contradict you If you're a Fedora fanboi, this latest release might break your heart a little Microsoft's latest Windows 10 update downs Chrome, Cortana LLVM contributor hits breakpoint, quits citing inclusivity intolerance. Password re-use is dangerous, right?
So what about stopping it with password-sharing? Master Amazon Web Services: Get on top of reliability with our best practices webinar El Reg's Serverless Computing London call for papers shuts tonight Now that Kubernetes has won, DigitalOcean takes a late dip in K8s Software dev and deployment luminaries head to Westminster. Geek's Guide Put Nov. Hopefully Pentagon in uproar: Boffins think they've found the evidence.
Now for some security headaches Silicon can now reconfigure itself with just a jolt of electricity day drone flights? You are like a little baby. How about a full YEAR? Verity Stob Mystery crapper comes a cropper The steaks have never been higher: Swiss Lidl is selling local cannabis Texas residents start naming adopted drains No top-ups, please, I'm a millennial: Lightweight yoof shunning booze like never before. An international group of quantum boffins reckons Bitcoin could be broken by the year Most read Cambridge Analytica dismantled for good?
It just changed its name to Emerdata Democrats need just one more senator and then a miracle to reverse US net neutrality death Take-off crash 'n' burn didn't kill the Concorde, it was just too bloody expensive to maintain Microsoft's latest Windows 10 update downs Chrome, Cortana Exclusive to all press: Atari launches world's best ever games console.
More from The Register. Google, Volkswagen spin up quantum computing partnership Pair to work on traffic optimisation and better batteries. Microsoft ports its Quantum Development Kit to Linux and macOS Now that it's not Windows-only, you can simulate a theoretical computer on a real computer. Microsoft asks devs for quantum leap of faith Try writing quantum code in Q , because We don't have a quantum computer yet, but we have a compiler It's quantum, it's open source, it's on GitHub. Did we miss anything?
Alibaba fires up a cloudy quantum computer Five-qubit creation is behind the great firewall and outside it at the same time! I spy with my little eye Whitepapers Don't Overlook Your Email Archiving Systems Today, business users need on-the-go access to all their critical data, which includes emails, documents and attachments. Seeking to reduce costs and to provide better customer experience.
Before proceeding we must understand what the definition of the words Certification and Accreditation. Sponsored links Get The Register's Headlines in your inbox daily - quick signup! About us Who we are Under the hood Contact us Advertise with us. Sign up to our Newsletters Join our daily or weekly newsletters, subscribe to a specific section or set News alerts Subscribe.