Hexbug nano v2 hive youtube
49 comments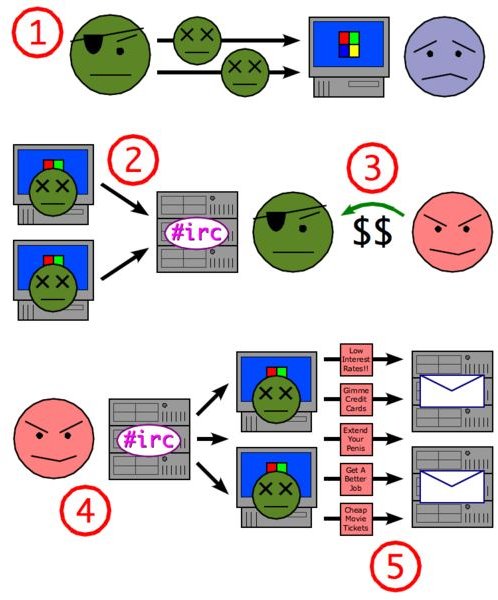
Bitcoin order book history children
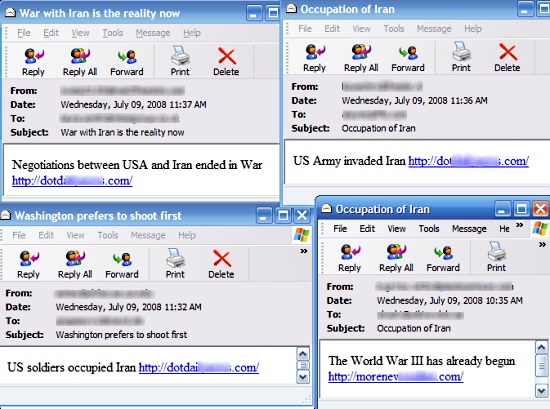
The Storm Worm dubbed so by the Finnish company F-Secure is a backdoor [1] [2] Trojan horse that affects computers using Microsoft operating systems, [3] [4] [5] discovered on January 17, The Storm Worm began attacking thousands of mostly private computers in Europe and the United States on Friday, January 19, , using an e-mail message with a subject line about a recent weather disaster, " dead as storm batters Europe".
Originally propagated in messages about European windstorm Kyrill , the Storm Worm has been seen also in emails with the following subjects: Amado Hidalgo, a researcher with Symantec 's security response group. When an attachment is opened, the malware installs the wincom32 service, and injects a payload, passing on packets to destinations encoded within the malware itself.
According to Symantec, it may also download and run the Trojan. F trojan, and the W Later, as F-Secure confirmed, the malware began spreading the subjects such as "Love birds" and "Touched by Love". These emails contain links to websites hosting some of the following files, which are confirmed to contain the virus:. According to Joe Stewart, director of malware research for SecureWorks , Storm remains amazingly resilient, in part because the Trojan horse it uses to infect systems changes its packing code every 10 minutes, and, once installed, the bot uses fast flux to change the IP addresses for its command and control servers.
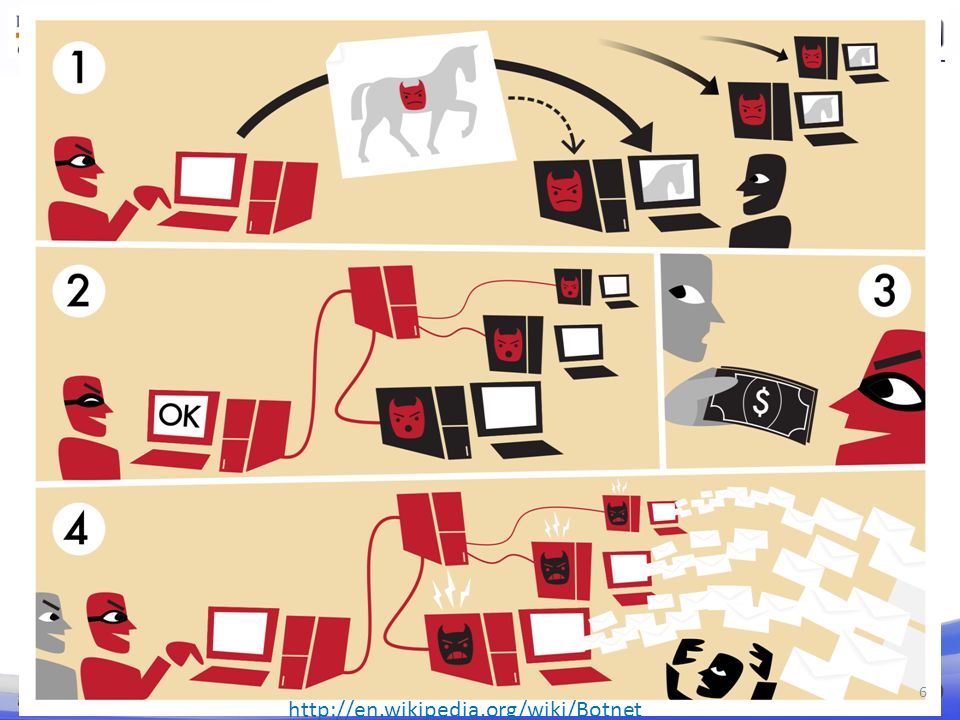
The compromised machine becomes merged into a botnet. While most botnets are controlled through a central server , which if found can be taken down to destroy the botnet, the Storm Worm seeds a botnet that acts in a similar way to a peer-to-peer network , with no centralized control.
While each of the infected hosts share lists of other infected hosts, no one machine has a full list of the entire botnet - each only has a subset, making it difficult to gauge the true extent of the zombie network. Another action the Storm Worm takes is to install the rootkit Win Later variants, starting around July , loaded the rootkit component by patching existing Windows drivers such as tcpip. On April 1, , a new storm worm was released onto the net, with April Fools-themed subject titles.
An intrusion detection system offers some protection from the rootkit, as it may warn that the Windows process "services. Peter Gutmann sent an email [17] noting that the Storm botnet comprises between 1 and 10 million PCs depending on whose estimates you believe. Gutmann makes a hardware resource comparison between the Storm botnet and distributed memory and distributed shared memory high performance computers at TOP , exact performance matches were not his intention—rather a more general appreciation of the botnet's size compared to other massive computing resources.
Consider for example the size of the Storm botnet compared to grid computing projects such as the World Community Grid. An article in PCWorld [18] dated October 21, says that a network security analyst presented findings at the Toorcon hacker conference in San Diego on October 20, , saying that Storm is down to about 20, active hosts or about one-tenth of its former size.
However, this is being disputed by security researcher Bruce Schneier , [19] who notes that the network is being partitioned in order to sell the parts off independently. From Wikipedia, the free encyclopedia. During our tests we saw an infected machine sending a burst of almost 1, emails in a five-minute period and then it just stopped. LiveUpdate definitions also identified it as Trojan.
Retrieved from " https: Windows trojans in computer science Hacking in the s. CS1 uses Russian-language script ru CS1 Russian-language sources ru All articles with unsourced statements Articles with unsourced statements from March Views Read Edit View history. This page was last edited on 3 April , at By using this site, you agree to the Terms of Use and Privacy Policy.