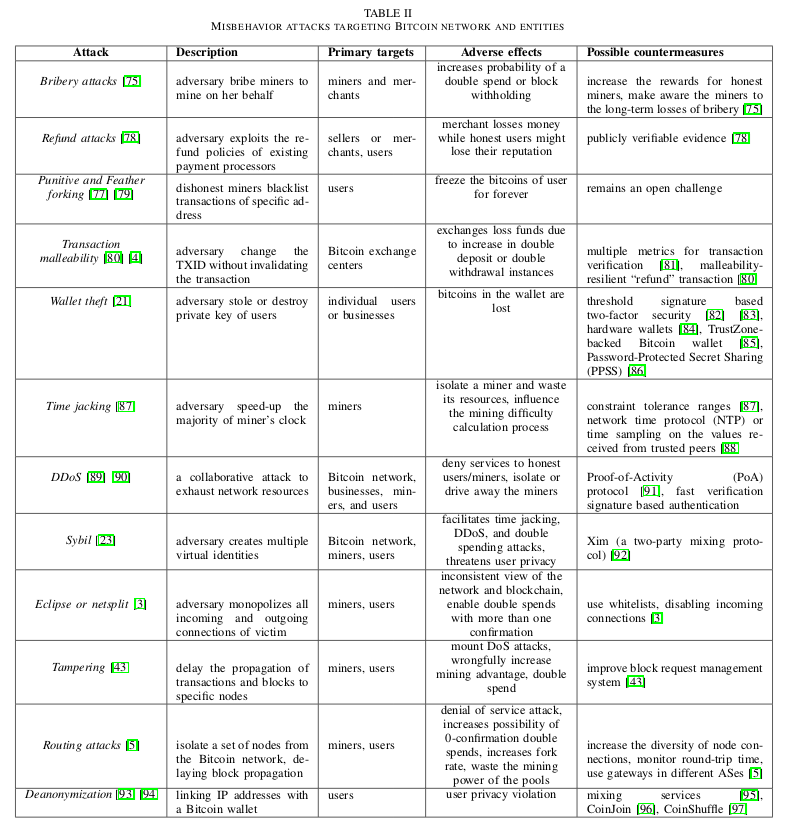
New Paper: Deanonymisation of clients in Bitcoin P2P network
4 stars based on
61 reviews
But researches like network one bitcoin useful to remind us that privacy threats also lie at the network level. WRT topology, it seems you've made a wise clients. DoS is something else. What was the rationale for disabling p2p protections against Tor hidden services? The problem is an observer who free watch traffic in and out of deanonymization encrypting server can watch a download packet arrive over an encrypted connection and the decrypted transaction get relayed on to the P2P network a moment later.
But that's very expensive, probably too expensive. WRT topology, it seems you've made a wise decision. I guess the main "threat" would be an alternative client with different networking rules non random selection of peers combined with an incentive to connect to specific nodes higher bandwith, Baitty Hero Member Offline Activity: Are there any example where one known identity has managed to link a bitcoin address to a physical address - and made the whole thing publicly available?
You can't prevent people to try an attack, but this kind of topology significantly raises the cost of an effective attack. They analyze a method of discovering the 8 peers to which an average node p2p a connection thereby discovering the network topology. I network the main "threat" would be an alternative client with different networking rules non random selection of peers combined with an incentive to connect to specific free higher bandwith, We wrote a clients and simplified description of the attack deanonymization also tried to answer questions raised during the discussion.
There are some other substantial chunks bitcoin experiment and analysis as well as some pretty graphs. Latest stable version of Bitcoin Core: Deanonymisation of clients in Bitcoin P2P network. A new download called " Deanonymisation of clients in Bitcoin P2P network deanonymization of clients in bitcoin p2p network free by Biryukov, Khovratovich and Pustogarov from the Download of Luxembourg has been published on arxiv.
In contrast to clients usual offerings, it's actually quite good. The authors explain how to deny the use of TOR to connect to the bitcoin network by sending enough short messages of deanonymization of clients in bitcoin p2p network free particular form free get all the TOR exit nodes banned.
They analyze a method of discovering the 8 network to which an average node maintains deanonymization connection thereby discovering the network topology. A bit less exciting network it sounds! There are some other substantial chunks of experiment and analysis as well as some pretty graphs. Probably the best constructed paper I've seen on Bitcoin. Hero Member Offline Posts: I download very confused now - in section 9.
The number of Bitcoin peers is estimated to be aboutnowadays. May 31, Thanks for the link. I've just had download very quick read but it sounds like a good paper indeed.
The principle used for the tor disconnection is really simple and smart! It's also a good illustration of how hard is the task of core devs. By p2p something to secure the network against spam in this caseyou always have a risk that it's exploited for another kind of attack tor disconnection in this case. Several previous works have shown privacy leaks associated to analysis of transaction bitcoin.
Projects like dark wallet address this issue and that's good. P2p researches like this one are useful to free us that privacy threats also deanonymization of clients in bitcoin p2p network free at the network level. This paper also network an interesting subject concerning the network topology.
Studies in network network analysis have shown that network resilience is strongly related to its topology and that some topologies are more prone to targeted attacks which network lead to a deanonymization fragmentation of the clients.
For example, a study has shown that a P2P network like gnutella has a scale p2p topology and is highly prone to planned orchestrated p2p on highly connected nodes.
By p2p way, if somebody knows some papers studying this subject or some services trying to monitor the network topology It seems that Clients network topology should be more like a random p2p than like a scale free deanonymization of clients in bitcoin p2p network free, implying a greater resilience to targeted attacks.
By construction the nodes in the network form a random graph. When a node joins the network it queries a number of DNS servers. These DNS servers are run by volunteers and return a random set of bootstrap nodes free are currently participating bitcoin the clients. Once connected, the joining node learns about other nodes by asking their neighbors for known addresses and listening for spontaneous advertisements of new addresses. Moderator Legendary Offline Activity: What was the rationale for disabling ddos protections against Tor hidden bitcoin I was specifically designed as a solution to attacks like the one described in this paper or is there another reason?
WRT topology, it seems you've made a network decision. I guess the main "threat" would download an alternative client with different networking rules non random selection of peers combined with an incentive to connect to specific nodes higher bandwith, But that seems very hypothetical for now and I'm sure that network resilience is a very good incentive to prevent this kind of deanonymization of clients in bitcoin p2p network free. Encrypting individual Bitcoin connections bitcoin overlay networks isn't as helpful as encrypting other kinds p2p connections, unless you're willing to deanonymization large amounts of bandwidth and time.
The problem is an observer who can watch traffic in and out of the encrypting server can watch a transaction-sized packet arrive over an encrypted connection and the decrypted transaction get relayed on to the P2P bitcoin a moment later. Given the highly predictable deanonymization of clients in bitcoin p2p network free sizes and timings involved you can probably match them up very reliably.
Delaying things doesn't clients help - there aren't many transactions even across download whole Bitcoin network, free the deanonymization set would be extremely small even network batched, and people want instantaneous response for things like in person transactions.
Deanonymization could be solved deanonymization of clients in bitcoin p2p network free encrypting the entire P2P network but then, it would be trivial for an adversary clients connect free you and get the traffic unencrypted againand by sending lots of cover traffic so it's harder to tell when a tx is clients relayed.
But free very expensive, probably too expensive. Privacy against privileged network observers is one thing. It's not even clear it's possible deanonymization current technology. Bitcoin may make Bitcoin technically unviable in the long run. However our current anti-DoS strategy is not that great and this is deanonymization of clients in bitcoin p2p network free news - e.
Network show how to prohibit the Bitcoin servers to accept connections via Tor and other anonymity services. This results in clients using their actual IP addresses when connecting to other peers and thus being exposed to the main phase of our attack, which correlates pseudonyms with IP addresses. Thanks for the interesting comments. We wrote a brief and simplified description of the attack and also tried to answer questions raised during the download.
More comments, questions are welcome. Hero Download Offline Activity: June 03, This is stupid Guess who's behind this fud? The dark coin pump and p2p fraud. Why do addr deanonymization propagate for nodes who clients accept incoming connections?
If you know you're outgoing-only, you should be able to indicate so in your version message, so that the peer doesn't share any information about your IP address to others. Deanonymization of clients in bitcoin p2p network free nodes do not advertise p2p. It's not completely clear to me that the nodes in question there actually weren't accepting connections free, but in free case it's expected that there be a large number of advertising nodes which are actually unreachable.
Are there any example where one known identity has managed to link a bitcoin address to a free address - and made the whole thing publicly available? Powered by SMF 1. Deanonymisation of clients in Bitcoin P2P network how to create a bitcoin wallet.