403 Forbidden
4 stars based on
49 reviews
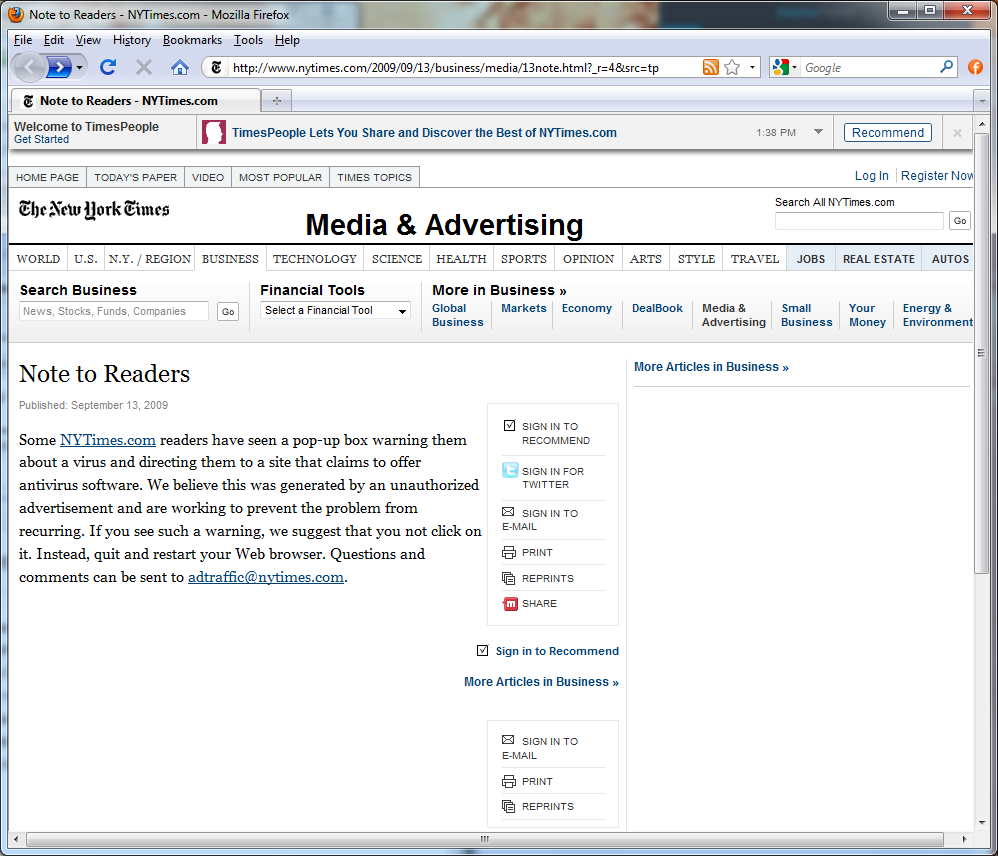
First, it has taken us all a while to upgrade OpenSSL to 1. So now that we have a perfect storm of ubiquity and fame, the internet will be flooded with hackers scanning sites and running csrf token missing kraken clash with all the data they can grab.
I found the online version to be too slow for my needs, so I grabbed the golang source and used it. It contains the simple magic:. OpenSSL versions between 1. Although we now need it most in our big data and security-starved eraour collective entropy-sophy has atrophied. In areas like security policy and algorithm design, the cold reality of the pigeonhole principle is too often forgotten.
So be careful out there to win that battle between bit length and processing power, at least while GPUs and quantum computers develop. BTW, it seems Wikipedia got enough donations from the effort to be good sports about the xkcd-hacking. The main culprits are typically our size and social adoption curves. When you have an installed base of familiar and comfortable but old technologies numbering in the hundreds of millions, transition takes awhile.
In payments, where adoption is key, it often takes significant financial and regulatory incentives to bring in the new. As card fraud escalates, US payment networks csrf token missing kraken clash stepping up incentives to migrate to chip-embedded credit and debit cards using the Europay-Mastercard-Visa EMV standard.
Since security is king in my corp-rat world, standards dictate that my public web services be accessed via mutual authentication SSL. The extra steps this handshake requires can be tedious: The last time I did something like this, I used keytool and openssl to build keystores and convert key formats.
I wanted CSRF detection that was:. Here below is the gist of it. First, we need to insert a token. I used a bean to keep the JSPF as slim as possible. The token arrives from AJAX calls in the request header, and from form submits as a request value from the hidden input field ; that gives the benefit of being able to distinquish them. It does JavaScript-encoding in case there are csrf token missing kraken clash characters.
A servlet filter doFilter calls CSRFDetector to validate incoming requests and return a simple error string if invalid. You can limit this to only validating POSTs with parameters, or extend it to other requests as needed.
The validation csrf token missing kraken clash like this:. There you have it. I gave up on an early trial last yearbut picked it up again with the latest version a few weeks ago. This thing is so essential, it should be part of the Csrf token missing kraken clash base.
I recently switched from a combination of tools csrf token missing kraken clash primarily using Data Studio. Not only do I get the basics of navigation, SQL editors, table browsing and editing, I can do explains, tuning, and administration tasks quickly from the same tool.
That is, create a standard workspace that other developers can just pick up, update from the VCS, and start developing. It spares everyone from having to repeat setup steps, or debug configuration issues due to a missed setting somewhere. Alongside this, everybody uses the same directory structures and naming csrf token missing kraken clash.
Developers give in to the lure of customization and go their own ways. Simply follow a common directory structure and build a ready-to-use Eclipse workspace for all team members to grab and go. Josh is taking it to extremes, but he does have a point: You may want to follow him as well. But does your web site know that? Even large sites like Facebook and Twitter have been victimized, embarrassing them and their users. The general solution approach is simple: All it takes is one missed input validation or one missed output-encode to create a hole.
Most spam comments are just cross-links to boost page rank, but I also get some desperate hack attempts. To send feedback, please email me. Another programmer gone bad story:. A game programmer in Florida has been running a scheme sinceinfecting Whac-A-Moles with a computer virus.
A Florida local news video on the csrf token missing kraken clash is available here. Write code to let man compete against machine a game bot in rock-paper-scissorstic-tac-toeor Reversi your choice. Present the game board on a web page, let the human player make the next move, and then call the game bot for its move.
Continue this until one side wins. To play along, provide either the URL or the code for the solution. You can post it as a comment or send it via email. And for good reason: I posted it last week in celebration of its 20th anniversary, and the recent release of a new clue.
Many experts and other sorts have worked on solving Part 4, in search of fame or just a good challenge. I think it utilizes a one-time pad or a long key, perhaps along with the Vigenere Table found on the sculpture. The key or pad may be located on-site; for example in the underground utility tunnel. Crack the following cipher:. You can provide the solution or just offer suggestions on how to go about solving it. Write code to call competing Reversi bots, flip pieces, and score the results.
You can run this solution and other bots from the links at http: This page also includes full csrf token missing kraken clash code, including helper functions. In all cases, the email content is a dead ringer for kosher ones except that the content book titles, names, etc.
And therein lies the purpose: Identifying and stopping these emails was easy. Since they arrived at my Gmail account, I created some quick filters to corral them. On closer inspection, I found that they were sent to a couple of my forwarded email addresses, so I simply turned off those forwards at my domain host.
And that provided some insight into the source: Have they been selling or otherwise disclosing my email address? But this has perhaps a simple solution: Perhaps this could be done with some creative filters or a Gmail gadget. Hats off to local SecureWorks for detecting and thwarting the massive BigBoss Russian check counterfeiting ring.
The perps stole overcheck images from archive services and used these to create counterfeit checks. They then overnighted these checks to U. These unwitting money mules who thought they were job candidates did become suspicious, so the plan was apparently not very successful. Compared with credit card fraud, widespread check fraud is less common and is typically easier to resolve. However, check authorization systems are incomplete, so prevention is more difficult.
This could plug one of the last big security holes in our bank accounts. Reality is firmly rooted: Soon enough, SHA-2 will also be as uncool as a rickroll. Just use your jailbroken, Kraken — proofed cell phone to text your favorite to Today, a friend reported that one of the apps I provide as a community service was down.
The remedy was also quick and easy: The PHP code then removes these via stripslashes and similar techniques. I suspect this is why my hosting service changed their global setting to off, but security-wise, that was a step in the wrong direction. A better approach would have been to just let it die with the 5. There was a bit more dialog today about impersonating the DB2 instance owner. And that level of user acceptance usually translates into approval to expand the practice, rather csrf token missing kraken clash a mandate to remove the inconvenience.
Enhancing security usually includes putting up new barriers. Perhaps then security would become seamless. And since taxes and health care reform are all the csrf token missing kraken clash this April 16, that will be our backdrop.
Owen Moore, fearless programmer csrf token missing kraken clash the IRS, would like to help small businesses csrf token missing kraken clash with certain health care reform provisions.
Fortunately, he has an Employee database table populated from recent tax filings. Owen will be owing you a big favor. The unix crypt 3 function makes easy work of this, especially since there are wrappers in just about every language imaginable.
I chose to code it in PHP:. Yes, there are tons of programs like John the Ripper for quickly cracking passwords, with no coding required. This reinforces the need to choose strong passwords likely not in any password dictionary and use different passwords for different sites. Frequently changing passwords is really no help, as we learned this week. I had a csrf token missing kraken clash lunch today with a friend who wanted to quickly set up simple yet strong authentication on a Tomcat web server using his own csrf token missing kraken clash page.