How to pronounce dogecoin
45 comments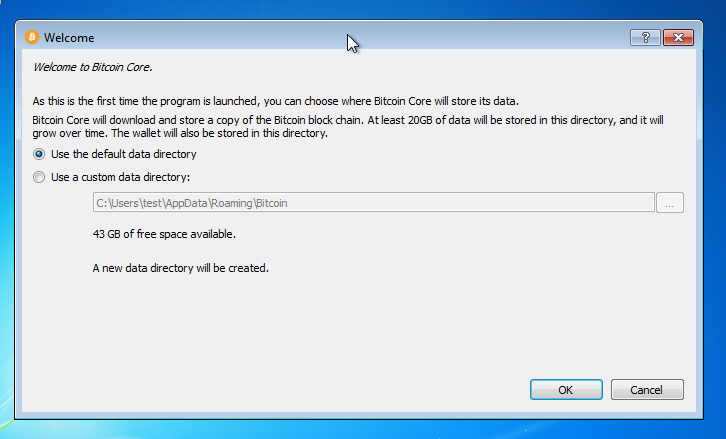
Bitcoin price yahoo
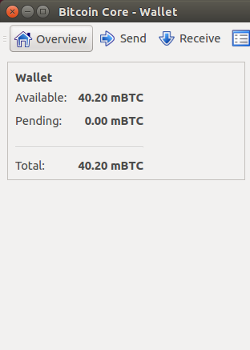
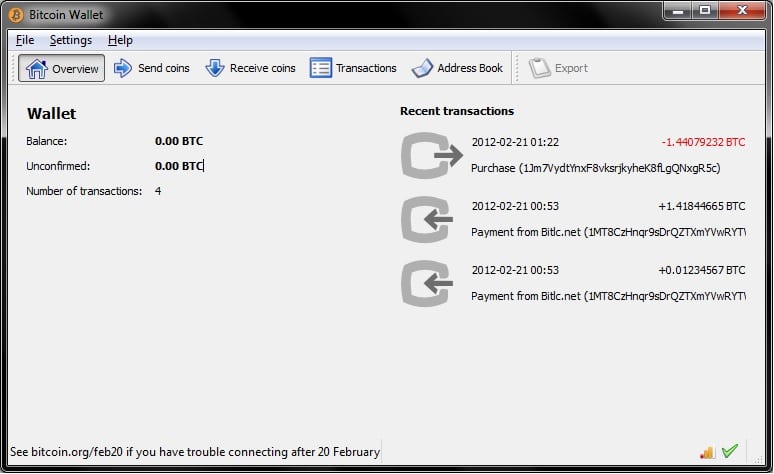
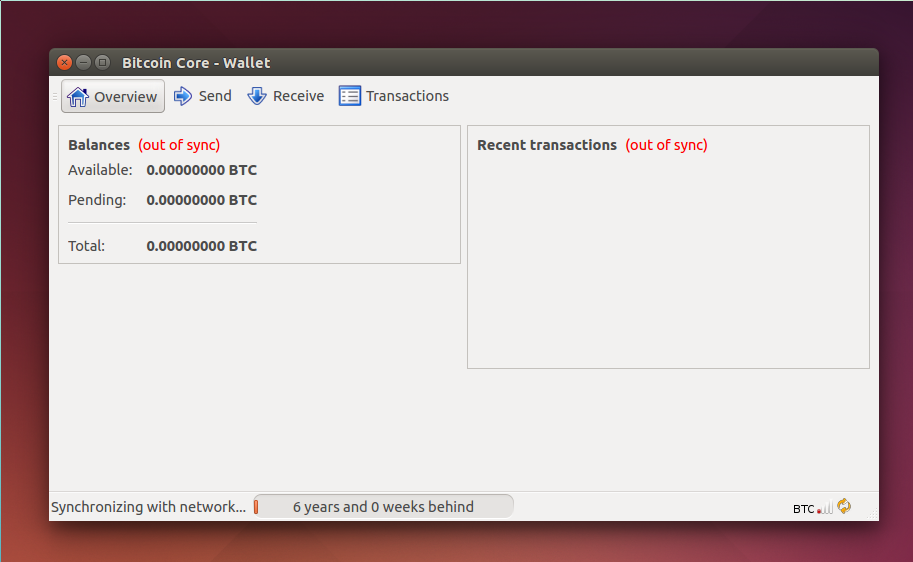
Bitcoin Core is a full Bitcoin client and builds the backbone of the network. It offers high levels of security, privacy, and stability. However, it has fewer features and it takes a lot of space and memory. This wallet gives you full control over your bitcoins. This means no third party can freeze or lose your funds.
You are however still responsible for securing and backing up your wallet. This wallet is a full node that validates and relays transactions on the Bitcoin network. This means no trust in a third party is required when verifying payments. Full nodes provide the highest level of security and are essential to protecting the network.
However, they require more space over GB , bandwidth, and a longer initial synchronization time. This wallet is open-source and built deterministically. This means any developer in the world can audit the code and make sure the final software isn't hiding any secrets. This wallet can be loaded on computers which are vulnerable to malware. Securing your computer, using a strong passphrase, moving most of your funds to cold storage, or enabling two-factor authentication can make it harder to steal your bitcoins.
This wallet makes it harder to spy on your balance and payments by rotating addresses. You should still take care to use a new Bitcoin address each time you request payment. This wallet does not disclose information to peers on the network when receiving or sending a payment. This wallet lets you setup and use Tor as a proxy to prevent attackers or Internet service providers from associating your payments with your IP address.
This wallet gives you full control over fees. This wallet also provides fee suggestions based on current network conditions so that your transactions are confirmed in a timely manner without paying more than you have to. Bitcoin is different from what you know and use every day. Before you start using Bitcoin for any serious transaction, be sure to read what you need to know and take appropriate steps to secure your wallet. Always remember that it is your responsibility to choose your wallet carefully and adopt good practices in order to protect your money.
Control over your money. Prevents spying on your payments This wallet makes it harder to spy on your balance and payments by rotating addresses. Avoids disclosing information This wallet does not disclose information to peers on the network when receiving or sending a payment. Tor can be used This wallet lets you setup and use Tor as a proxy to prevent attackers or Internet service providers from associating your payments with your IP address. Full control over fees. Take time to educate yourself Bitcoin is different from what you know and use every day.